This post is also available in: 简体中文 (Chinese (Simplified)) 繁體中文 (Chinese (Traditional)) 日本語 (Japanese) 한국어 (Korean) Português (Portuguese (Brazil))
Palo Alto Networks survey data shows that SOC analysts are only able to handle 14% of alerts generated by security tools. When you consider IDC data showing that most alerts are false positives,[1] the results are predictable: Alerts get ignored, analysts waste time chasing false leads, and actual threats get missed.

Beyond initial prevention, most security tools are designed to perform one key function: create and respond to alerts. Servers create alerts. Routers create alerts. Firewalls create alerts. Antivirus tools create alerts. Security teams will often set up alert-only policies – rather than block policies – for potentially risky processes the business uses regularly.
The hopeful assumption is that analysts will review and catch any suspicious behavior based on those alerts. But this strategy falls apart quickly when analysts start to receive thousands of low-fidelity alerts per day. It’s worse that these alerts come from siloed security tools that provide little-to-no context about what’s actually going on.
Alert fatigue reduction checklist
If we eliminate alert-generating sensors and systems, we create security blind spots – yet too much information is as bad as no information at all. We need to use technology in smarter ways to help solve problems without creating new ones. We still need alerts, but we need more accurate alerts. This means embracing the following concepts when considering your tools and processes:
1. Automation
First, organizations can greatly improve their alert triage process using automation. Palo Alto Networks believes that all Tier 1 (alert triage) security operations can and should be automated using SOAR technologies, which use predefined playbooks to automate response actions. For alert triage, these actions include analyzing an alert, updating a case if it’s a known issue, opening a case if it isn’t a known issue, and then triaging the severity of the alert to send it to an analyst. Automating this process greatly reduces the number of alerts analysts must respond to, allowing analysts to spend their valuable time investigating issues rather than staring at logs.
2. Data stitching
Secondly, security teams must start prioritizing integrated tools over siloed ones if they want to improve visibility. If you have seven different tools, each looking at a specific slice of your security infrastructure without talking to each other, the tools won’t be able to provide context that helps with threat hunting and investigations. You won’t know if a series of actions that seem benign on their own are actually being performed in a sequence that may indicate an adversary is in your system. Alternatively, you may spend an hour tracking a piece of malware that snuck past your EPP only to find that it was blocked by your firewall.
A security platform with integrated capabilities allows for much greater insight. Cortex Data Lake, for example, connects endpoint, cloud, and network data together. This integration between security components provides Cortex XDR with the benefit of more enriched telemetry data (for faster investigation and threat hunting) and tainted alerts (to block actions associated with past malicious behavior).
3. Machine learning
Finally, an EDR tool should have machine learning capabilities that allow it to recognize patterns so it can learn and improve. Your EDR should draw from your (hopefully integrated!) data sources to continue to refine its algorithms for generating high-fidelity, prioritized, specific alerts.
Cortex XDR delivers smarter detections
Cortex XDR has proven it delivers the highest combination of high-fidelity alerts, which are the most useful for identifying threats, as well as enriched, correlated telemetry logs for investigation and threat hunting. These types of alerts can help organizations stem the flood of false positives so their analysts can focus on investigating real threats.
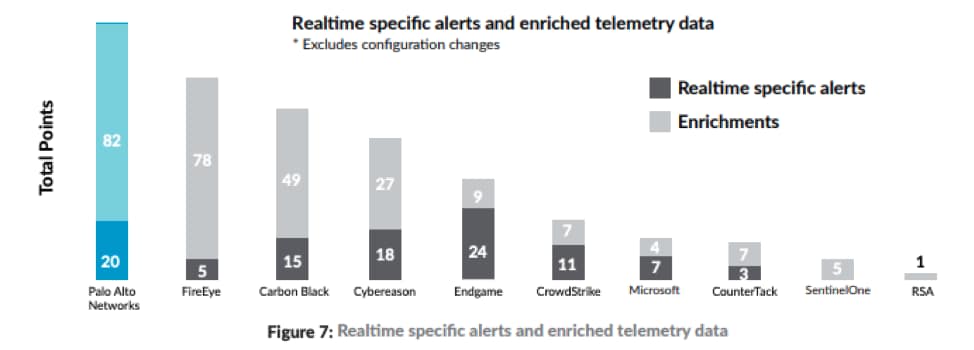
A test of EDR tools using realistic attack emulations from the APT 3 group through the MITRE ATT&CK recently found that Cortex XDR and Traps detected the most attack techniques of 10 endpoint detection and response vendors. This evaluation provided one of the industry’s first open and objective assessments of the true function and performance of the EDR marketplace.
With its default configuration during the MITRE test, Cortex XDR generated 20 realtime, specific alerts and 82 enriched telemetry logs. In a real deployment, customers can give Cortex XDR even more visibility and context into the behavior of potential threat actors by connecting additional network and cloud sensors into Cortex Data Lake. That will further reduce false positives and improve identification of malicious behavior that may otherwise seem benign.
Read more about the MITRE results here.
[1] Ryan Francis, “False positives still cause threat alert fatigue,” CSO Online, May 3, 2017, https://www.csoonline.com/article/3191379/false-positives-still-cause-alert-fatigue.html.