How do you respond to a security incident? In some cases, the answer might be ‘block first, ask questions later.’ That was common a decade ago in the centralized IT infrastructure. Security teams had tools that could help them identify suspicious behavior and promptly block the resource or endpoint. But when it comes to cloud data, things aren’t that simple. Business-critical data is mired in dependencies between pipelines and complicated environments, making it difficult to reach for the kill switch.
Below we explain some of the key challenges of incident response in cloud environments and suggest best practices for security teams to prevent catastrophic breach events without disrupting data-driven operations.
The Challenges of Effective Incident Response Planning for Cloud Data
Security teams need to keep the organization and its customers safe from an evolving threat landscape while minimizing operational disruption. In the context of data, this is challenging to achieve due to the complexities of modern data stacks, as well as the central role that data plays in business operations. In practice, organizations tend to grapple with three questions.
1. Who Takes Action? (Who Owns the Data?)
Data ownership is an elusive concept in the age of data democratization. The same datasets often have multiple uses across departments — developers, analysts, business units and IT teams. And the team producing the data isn’t necessarily the one that most relies on it. Data sources, pipelines and permission schemes form a complex web of interdependencies. Even when there are nominal data owners, they may not understand the downstream impacts of removing access or making a change.
Finding and involving the right people, as you might imagine, is an essential part of remediating a data security incident. The technical team that has the ability to execute changes (such as removing permissions to a database) is only part of the equation. Security teams need to quickly identify the stakeholders and get their input to prevent unintended consequences.
2. Which Incidents Take Priority?
Separating signals from noise is one of the main problems in cloud security. Multicloud environments and an abundance of logging and monitoring services mean that teams are inundated with alerts. Resources are finite. Security teams need to focus on the incidents that matter.
Security teams need a way to escalate issues with major compliance or data security implications while leaving lower-priority incidents to be addressed through standard workflows. Understanding context is key — including the sensitivity of the data (e.g., whether it contains PII or developer secrets), the types of workloads that might be disrupted, and potential impact on the organization.
3. How Do You Automate Without Risking Production?
Automated incident response flows were part of traditional DLP tooling, allowing security or IT to block suspicious behavior based on predefined rules. For the reasons we detailed above, this isn’t usually applicable to cloud data processes. The damage of shutting down a production database is usually too significant, and most organizations wouldn’t be comfortable doing so through a fully automated action.
But organizations are also wary of fully manual processes predicated on people responding to notifications. They’re looking for a middle ground that will allow them to automate parts of their incident response flows — such as collecting information, checking data ownership or identifying relevant misconfiguration — while leaving the final decision in human hands. The exact level of automation applied will remain a middle ground.
An Effective Incident Response Framework Based on DSPM, DDR and Cloud DLP
The challenges we outline aren’t insurmountable, but they do require organizations to evolve their approach to incident response. The prerequisites for an effective incident response program are context into the data being monitored, the ability to identify the data owner and workflows that address real-time risk, as well as misconfigurations.
Stage 1: Advance Preparation
To effectively prepare for and respond to cloud data incidents, organizations need to lay the groundwork.
Inventory
Organizations need visibility into their sensitive data to identify, prioritize and respond effectively to incidents. This requires creating and maintaining an inventory of data assets across cloud services, including classification of datasets based on attributes like personal data, financial data, intellectual property, etc. This allows organizations to assess compliance and security risks when an incident occurs and determine the right response. The inventory should track which cloud services hold sensitive data, who has access, and how it flows between systems.
Ownership
Security teams need to identify who owns each sensitive data asset, and who owns the associated risks. As we’ve noted, this can be difficult to achieve when data is shared and used across multiple business units. A specific resource can fall under the purview of application teams (code and OLTP databases), IT and DevOps (policies and infrastructure), or security teams (security infrastructure, SSO).
Integration
Security tools should be tightly integrated with cloud services and infrastructure. This allows pulling context on users, data and environments to feed into automated investigation and response workflows. Integration should provide visibility into access patterns, data flows between services, and mapping of technical controls like encryption, as well as SIEM and SOAR systems, ticketing platforms and CSPM tools.
Procedural Definition
Procedural definition includes classifying incident severity, specifying escalation paths, delineating stakeholder responsibilities and detailing the steps for investigation, remediation and communication. Well-defined procedures allow for smooth coordination between security, IT, and business teams during high-stress incidents. They also provide guidance on the appropriate response based on incident type, data sensitivity and potential impact.
Stage 2: Risk Mitigation
The following steps should be taken to reduce the risk and potential damage caused by an incident:
Prioritization
Security teams should prioritize incidents based on potential impact and level of risk. This requires understanding the sensitivity of affected data based on previous classification efforts and the level of risk, as well as which applications, workflows and teams may be disrupted. Incidents involving large volumes of highly sensitive data, or critical production systems, should be escalated and addressed first.
Remediation and Validation Workflows
Security teams should execute remediation via standardized predefined workflows. These should include automatically opening tickets in ITSM systems to track the incident response and document actions taken.
Stage 3: Containment and Remediation
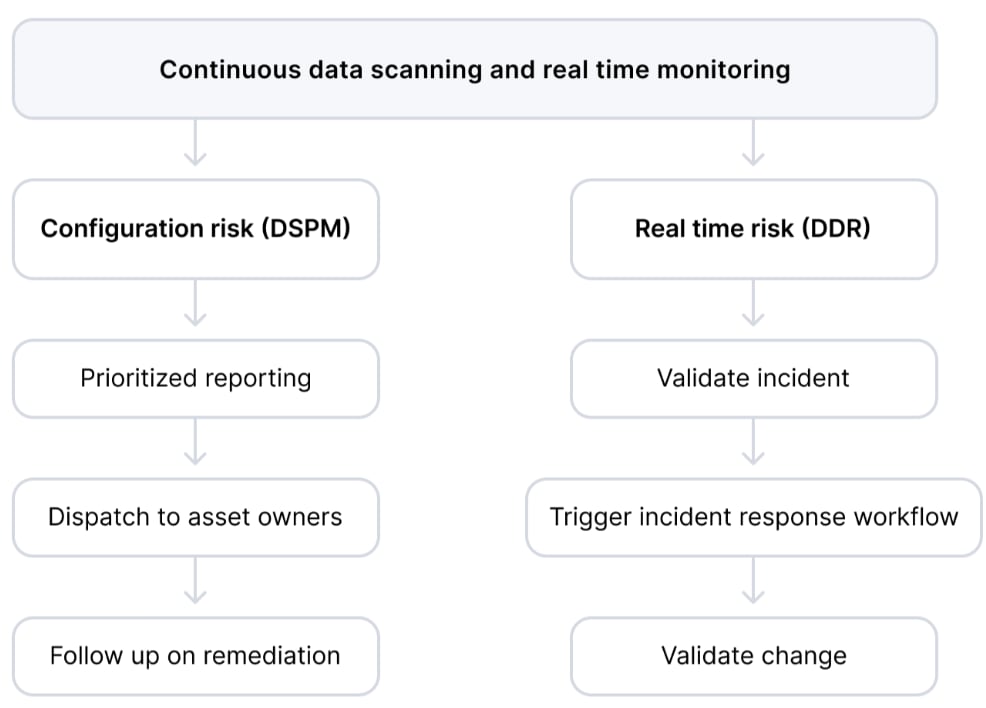
Incident response needs to encompass two types of risks — those that stem from posture (configuration) issues and those that stem from real-time threats.
Configuration-based risk, typically handled by data security posture management (DSPM) tooling, could include improper encryption policies, overly permissive access controls or backup misconfigurations.
Real-time risks are immediate threats, such as an unauthorized user accessing sensitive data, abnormal data transfer activity or severe compliance violations such as customer credit cards being replicated into noncompliant environments. These incidents require rapid triage and containment by security teams to prevent damage. When real-time incidents occur, the priority is to block suspicious access or activity and ask questions later. We might want to revoke access to compromised accounts, block users displaying anomalous behaviors, quarantine impacted assets, etc.
Triage
Once a cloud data incident is identified, triage processes will focus on validating that the access is indeed unauthorized and determining whether the actor is malicious or harmful. This might involve collecting additional information from threat intelligence systems, validating the actor’s identity or identifying the impacted processes. Once the source of the problem and the potential impact are known, teams can select a mitigation pathway.
Containment
Containment actions can include suspending compromised user accounts, stopping affected workloads, restricting network access and isolating affected cloud resources. The goal is to limit damage and prevent escalation while deciding on long-term remediation steps. Containment should be as targeted as possible to avoid unnecessary business disruption.
Remediation and Validation
Misconfigurations and compliance issues are addressed by data teams, application teams, IT or security. After executing approved remediation steps, security tools should rescan affected data to validate that risks have been removed. In the case of compliance violations, validation can help to provide evidence to auditors that issues were addressed.
Using Prisma Cloud for Cloud Remediation
Factors like compliance, data classification and overall risk posture should drive prioritization. Prisma Cloud’s DSPM capabilities help organizations understand which sensitive data they store and where they store it — across S3 buckets, databases, virtual machines, SaaS and shared folders.
Once sensitive data has been identified, it needs to be contextualized from a security and business perspective. Monitoring data flows and lineage can help identify the source of the data and which dependencies will be impacted by a change. At the same time, data access governance can help teams understand the full scope of access permissions and which ones are being used.
Prisma Cloud’s unique DDR capabilities allow it to address real-time threats and configuration-based issues — removing the need for managing multiple DLP tools. These flows, however, would be handled differently, as in figure 1.
Toward Better Cloud Incident Response
Sensitive data remains the most coveted asset for hackers, ransomware and theft. Security and compliance incidents are par for the course and will continue to pose problems for enterprises. By adopting modern approaches and solutions to incident response, organizations can provide effective remediation, prioritize sensitive assets and high-risk scenarios and prevent incidents from spiraling out of control.
Learn More
DSPM with data detection and response (DDR) offers critical capabilities previously missing in the cloud security landscape — data discovery, classification, static risk management, and continuous and dynamic monitoring of complex, multicloud environments. Learn how to secure your sensitive data in the cloud with our definitive DSPM resource, Securing the Data Landscape with DSPM and DDR.
And get a free security assessment to discover how we can help you continuously protect your sensitive data.