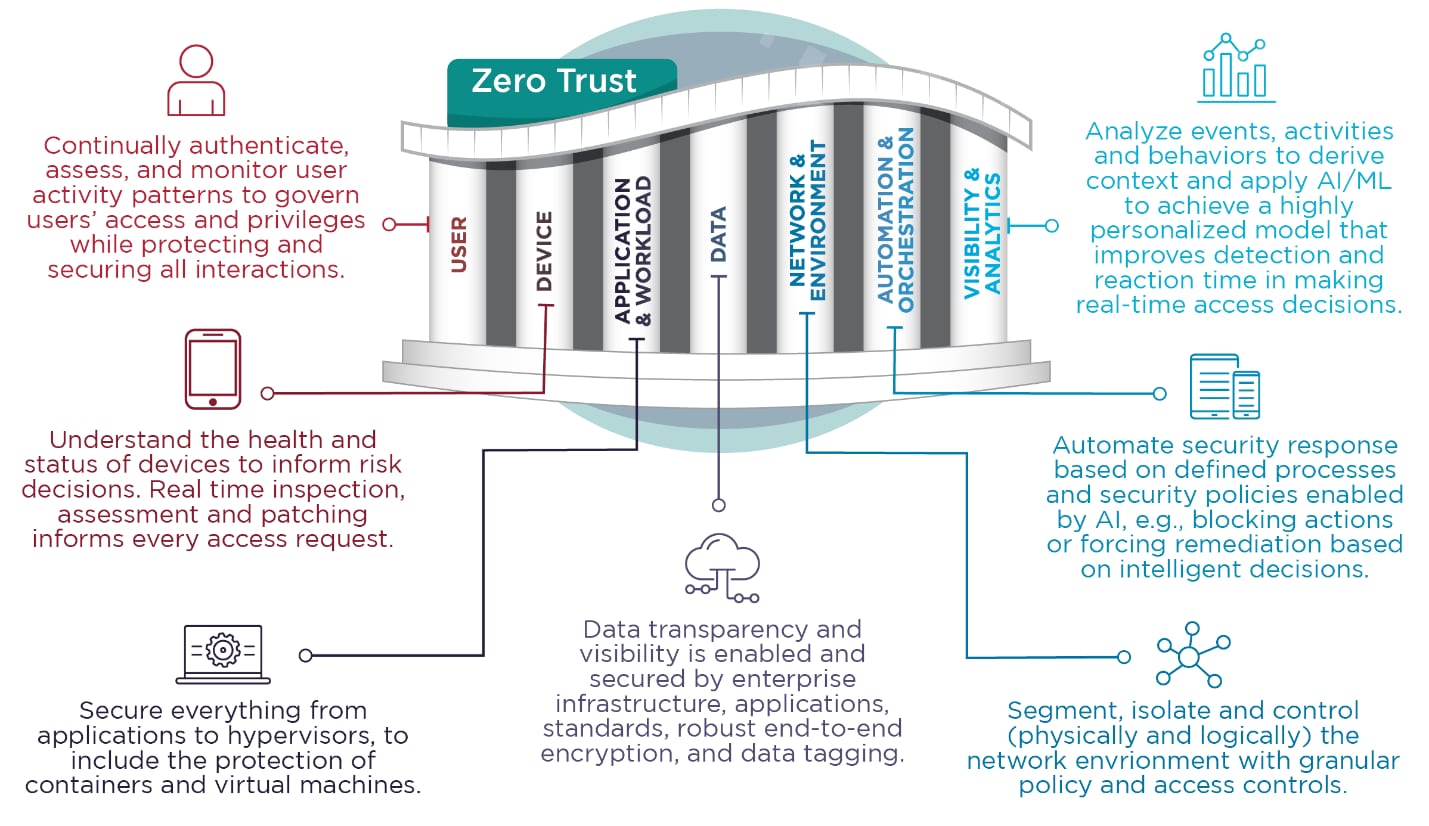
The U.S. National Security Agency (NSA) recently published the cybersecurity information sheet Advancing Zero Trust Maturity Throughout the Application and Workload Pillar.
For many years, the cybersecurity industry has made advancements in securing networks, users and data with the “never trust, always verify” process. What I find interesting about this document is that the NSA acknowledges the need to expand beyond traditional Zero Trust pillars and shift toward securing cloud-native applications.
Seventy-one percent of organizations acknowledge that rushed application deployments introduce security vulnerabilities. It’s essential to design a Zero Trust architecture that secures applications from the first line of code to runtime in the cloud. Furthermore, 84% say that security processes cause delays in software development. With this in mind, security must protect applications without hindering developer productivity.
Here are some key takeaways from the NSA's guidance and what you can do to apply recommendations without slowing down development.
Secure by Design
At Palo Alto Networks, we recognize the importance of securing applications by design. We’re thrilled to see that the NSA considers this important too. But what does secure by design really mean?
Traditionally, securing applications only meant protecting the digital assets that run in the cloud, such as compute, data, networks and identities. Meanwhile, the application lifecycle begins with code created by developers, which means that security risks can be introduced before applications run.
According to the guidance document, “Most organizations rely on software and code from sources that could contain vulnerabilities or malicious injected functionality. Having secure software that can be relied on to perform its intended functions and not be exploited to perform malicious operations is just as important, if not more important, as securing the provided software.”
The NSA goes on to say, “The ZT model recommends adopting the DevSecOps framework and utilizing the continuous integration/continuous delivery (CI/CD) approach for organizations that develop applications to ensure secure development and deployment”
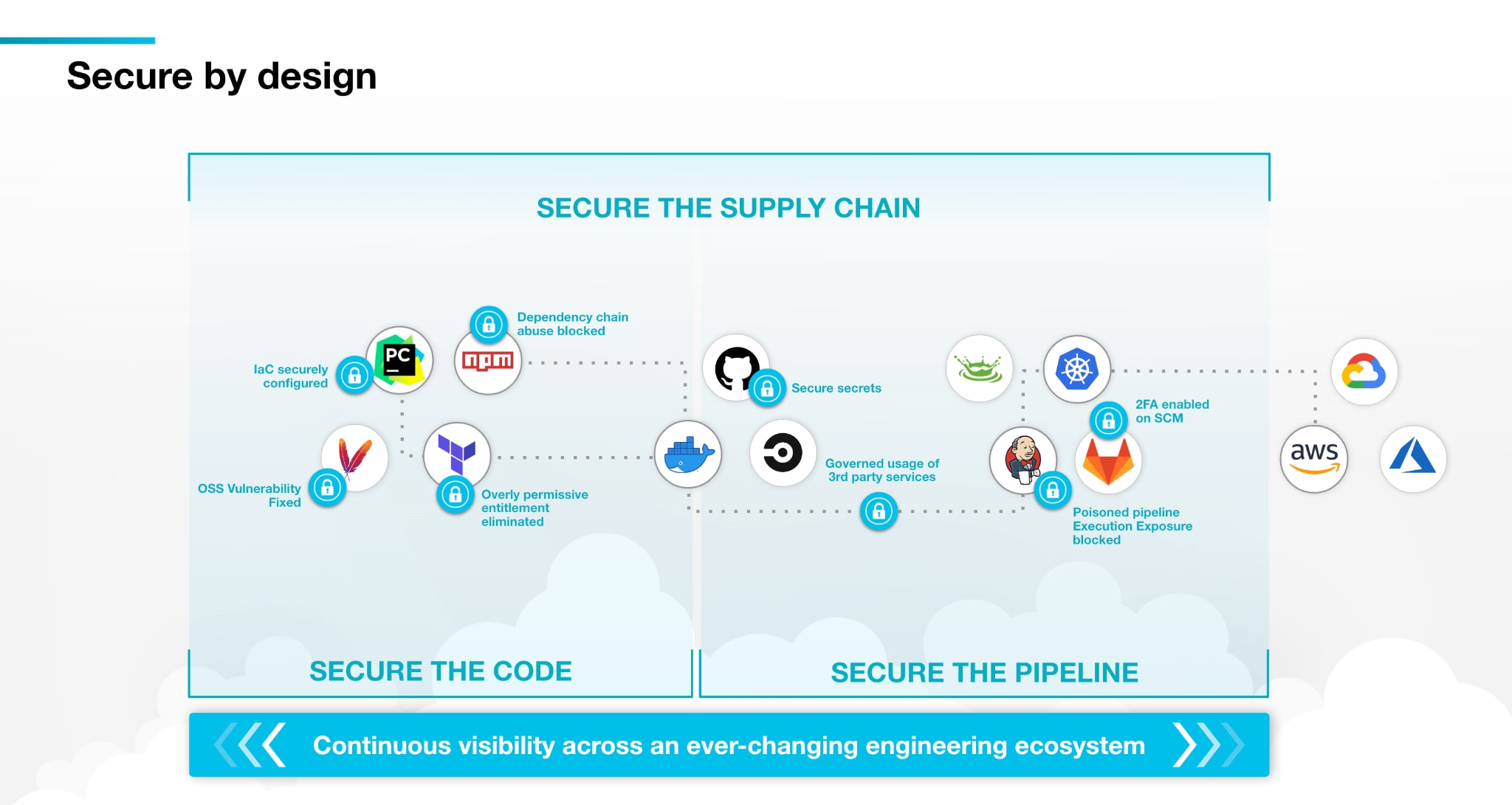
Palo Alto Networks believes there are a series of controls to help secure applications by design:
- Secure the code: Enable developers to fix flaws in code repos, such as infrastructure as code (IaC) misconfigurations, open-source vulnerabilities and exposed secrets.
- Secure the pipeline: Protect the pipeline that delivers the software by mitigating OWASP Top 10 CI/CD Security Risks and remediating hidden attack paths.
- Secure the supply chain: Govern the entire engineering ecosystem — from coding languages to CI/CD platforms — and generate software bill of materials (SBOMs).
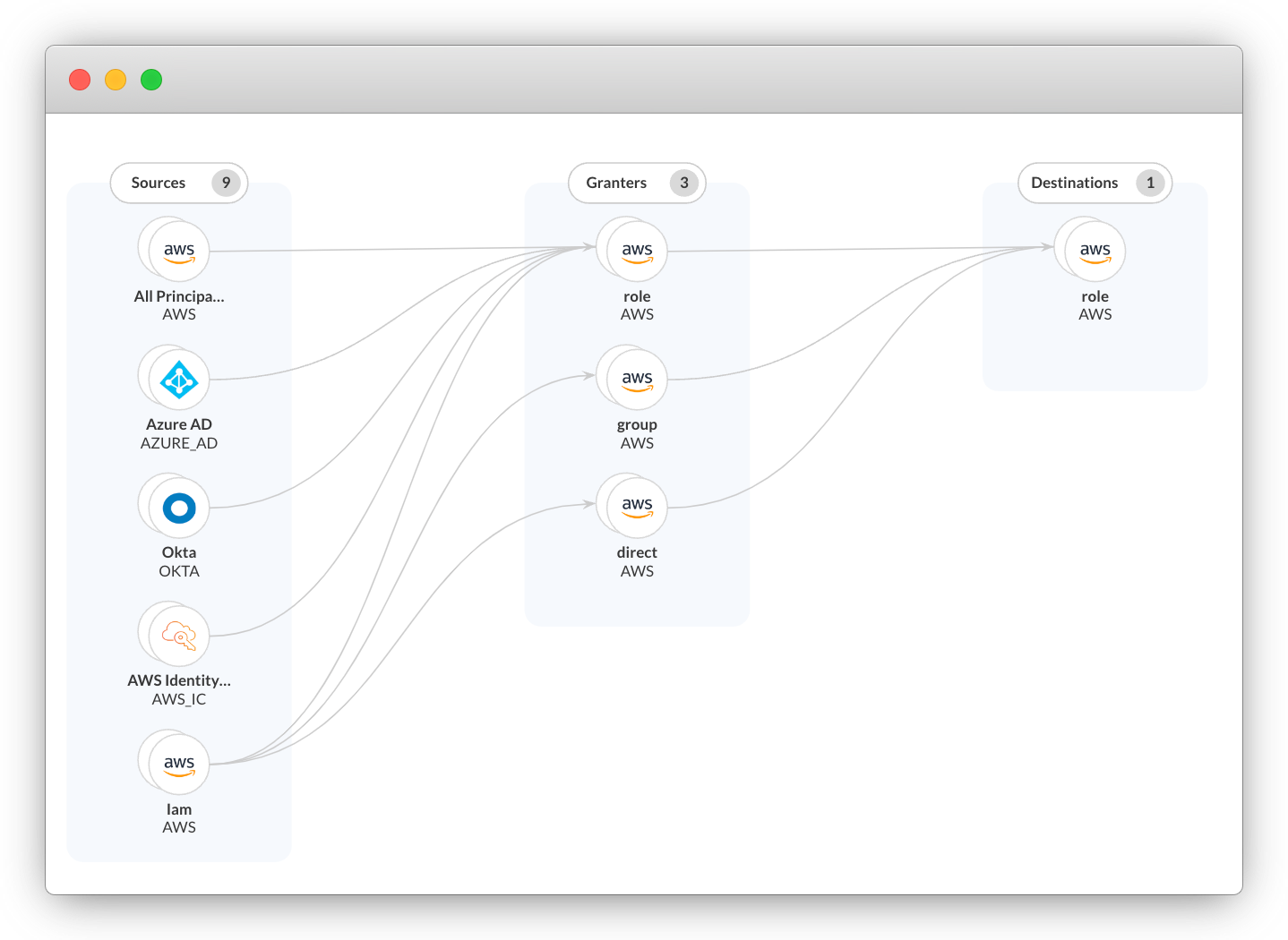
Principle of Least Privilege
Nearly all cyber breaches have one thing in common: adversaries taking advantage of excessive privileges for lateral movement. Perhaps that’s why applying the principle of least privilege (PoLP) is essential to any Zero Trust strategy.
According to the recommendations outlined in the NSA guidance, “Follow PoLP, ensuring users and applications receive only the minimum level of access required to perform their jobs.”
Applying least-privileged access isn’t always an easy task. Security teams are required to understand how users and applications function before enforcing policies. Otherwise, they could end up disrupting applications or hinder productivity. Identity and access management (IAM) complexity grows by an order of magnitude in the cloud, considering workloads (or machines) have identities and cloud infrastructure constantly changing.
Cloud infrastructure entitlement management (CIEM) technologies emerged to help security teams apply PoLP across multicloud infrastructure. CIEM tools provide visibility into identities and access, recommend new privileges based on learned access behavior and remediate excessive permissions.
Container Protection
As organizations modernize applications, they’re not just moving them to the cloud, they’re refactoring workloads through containerization. “By 2025, enterprises will have adopted multiple public cloud infrastructure as a service (IaaS) offerings — including multiple K8s offerings,” according to Gartner.
Like applications, container security requires full lifecycle security. As advised by the NSA, “When working with containerized workloads, ensure their security by regularly scanning container images for vulnerabilities, limiting container privileges, protecting container secrets, and implementing runtime security controls.”
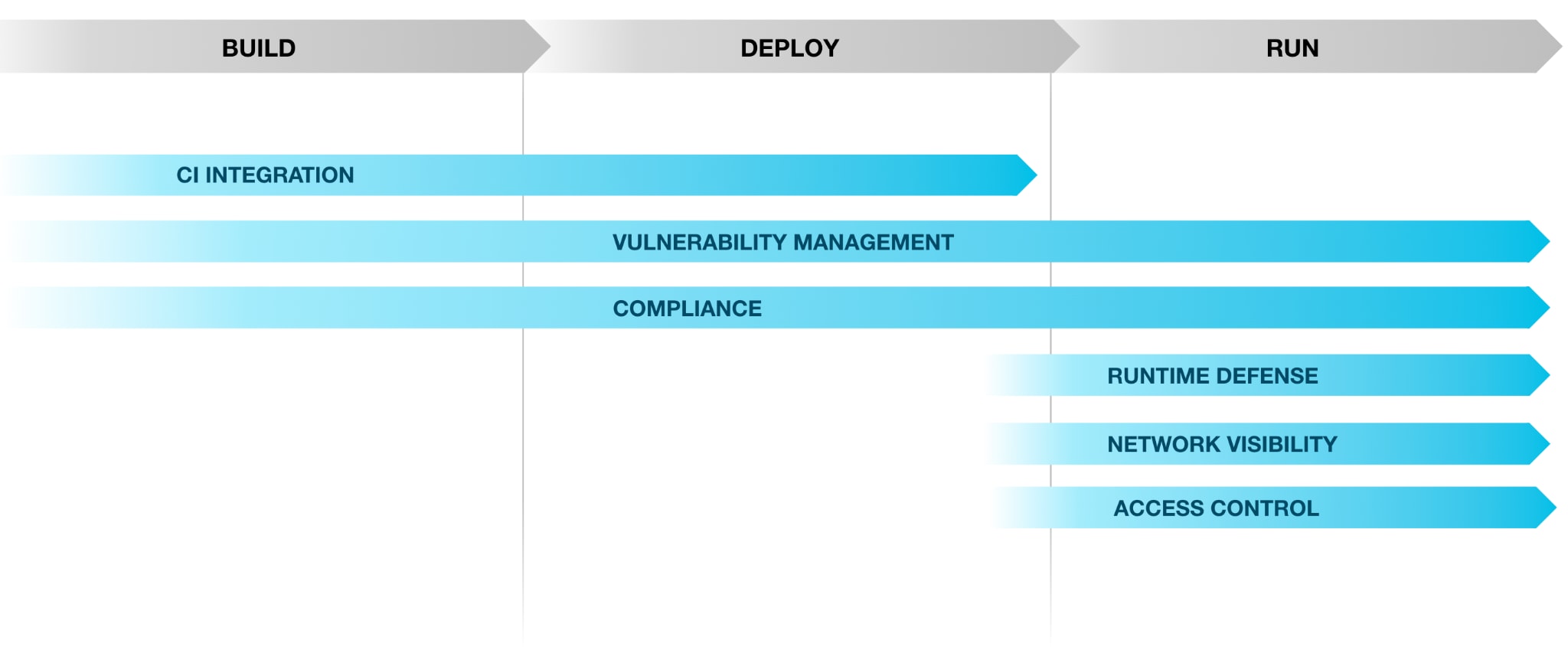
To take things a step further, a modern approach would visualize and manage risk from the lens of the software development lifecycle. This means detecting application vulnerabilities across clouds, container images, repos and software packages, and then automatically correlating them to understand the root cause of critical issues. By fixing issues at the source, or in code, security teams can prevent recurring mistakes in runtime.
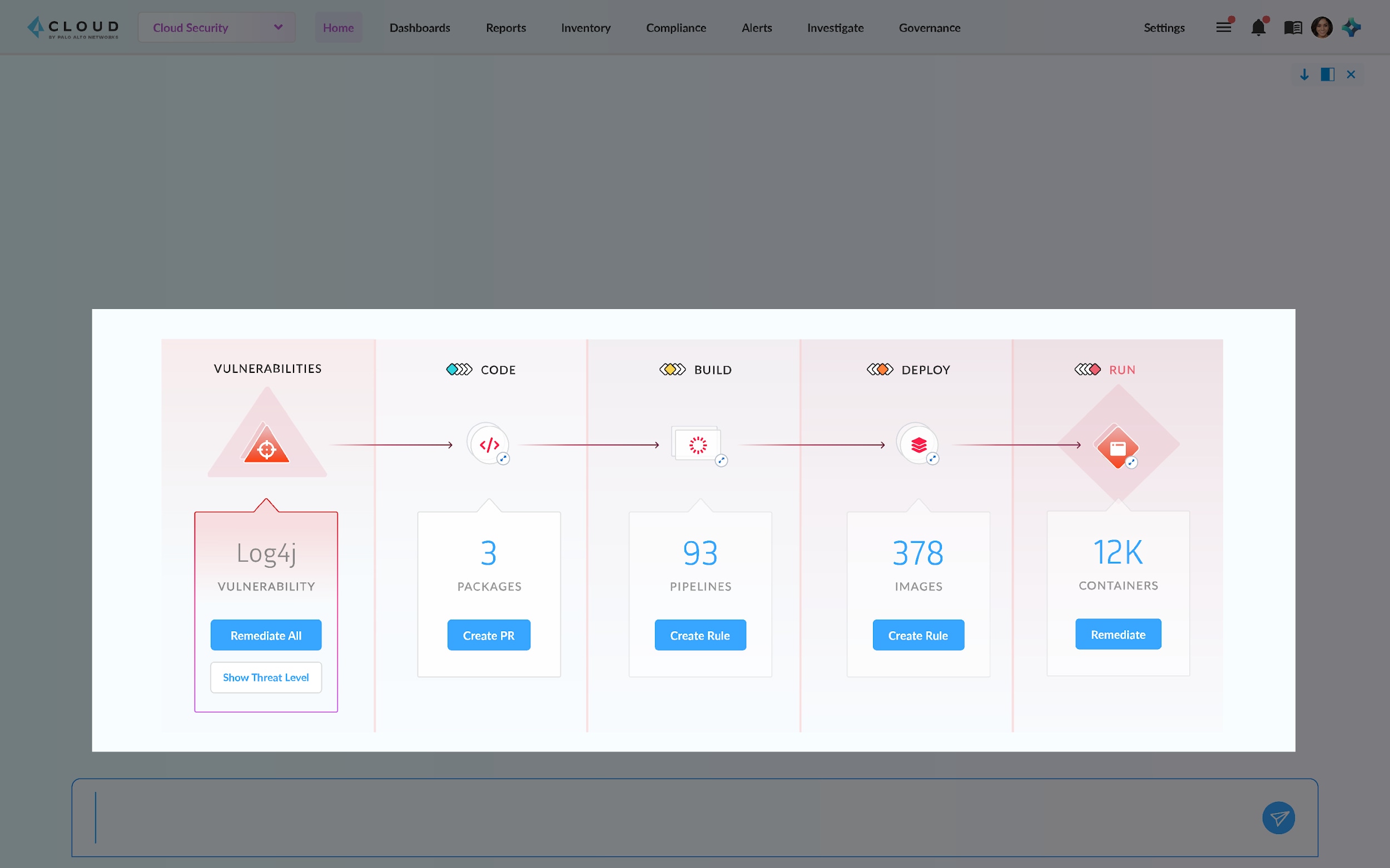
Acting on Guidance with Prisma Cloud
Prisma Cloud, a Palo Alto Networks platform, protects applications and workloads from code to cloud. The platform enables security and DevOps teams to better collaborate, ensuring that protections mirror the speed of software development. Offering full security coverage, Prisma Cloud protects code, pipelines, cloud infrastructure, workloads, data, web applications and APIs against modern threats.
To identify potential risks in your cloud, request a free cloud security health check. Alternatively, if you'd like to see Prisma Cloud address NSA guidance, book a personalized demo.