SD-WAN vs. VPN: Use Cases, Differences, & When You Need Both
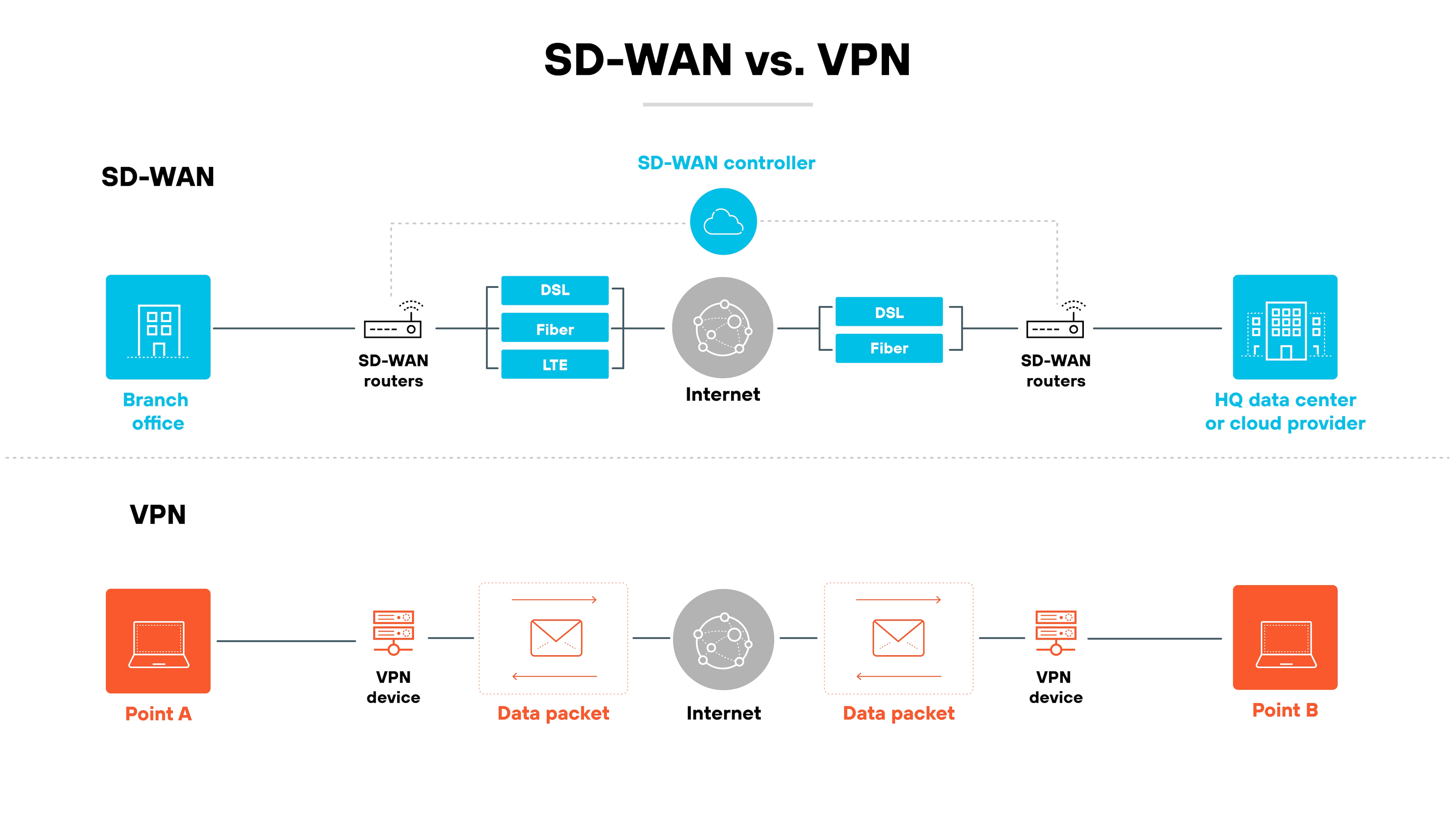
The difference between SD-WAN and VPN is that SD-WAN uses software-defined policies to manage and optimize traffic across multiple WAN links, while VPN creates encrypted tunnels to secure communication between two points.
SD-WAN provides centralized control and performance monitoring. VPN focuses only on securing traffic in transit.
What is a VPN?
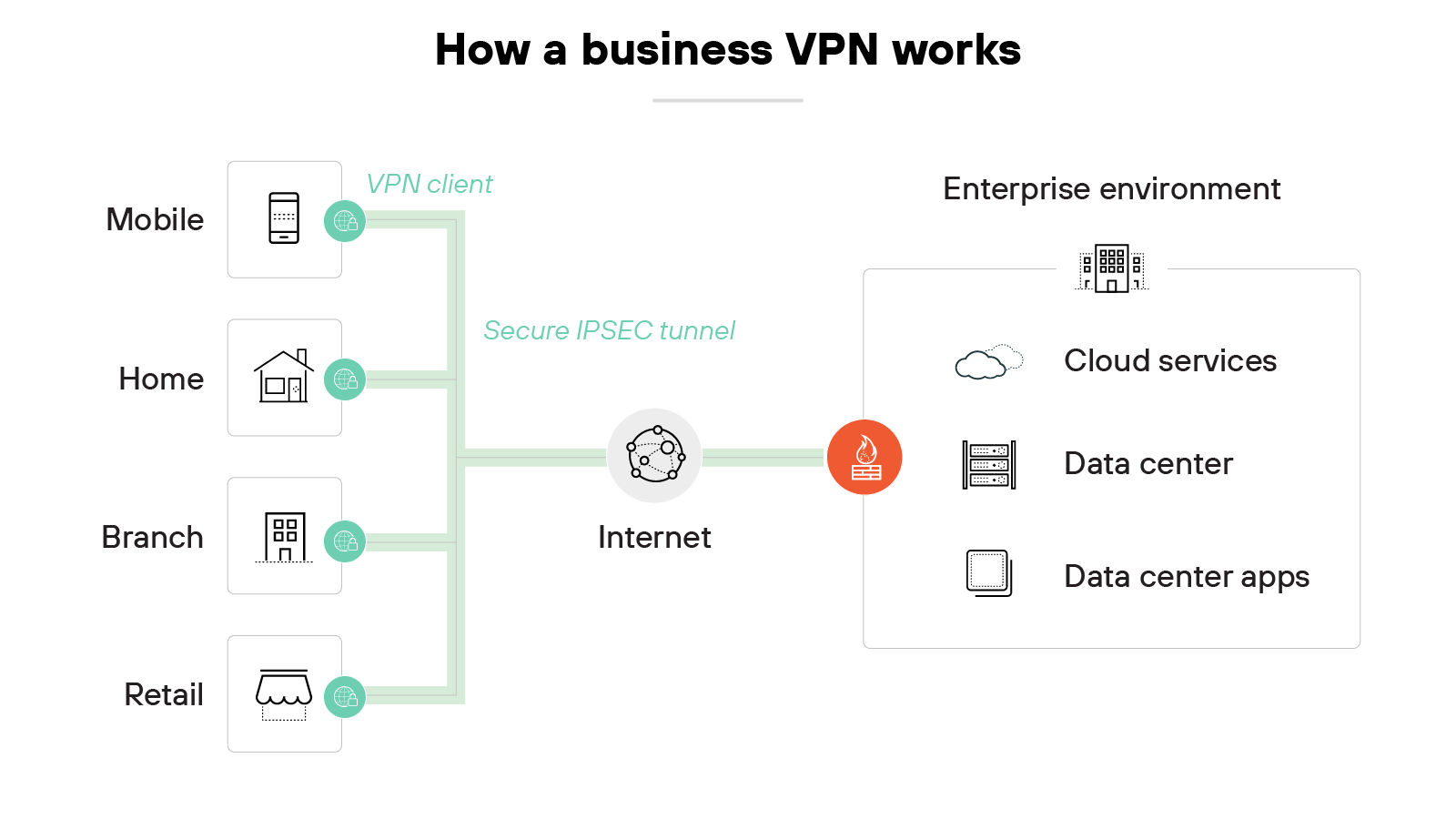
A virtual private network, or VPN, is a secure way to connect devices or networks over the internet.
It works by creating an encrypted tunnel between two points. All traffic that passes through the tunnel is scrambled so outsiders can't read it. The tunnel also hides the original source and destination of the traffic, which adds another layer of privacy.
Why is this useful?
On a public network, traffic is open to interception. A VPN prevents that by ensuring the connection behaves as if it were private. In other words, it extends a secure line from the user's device to the organization's network.
At a high level, there are two main types of VPNs. A remote access VPN allows individual users to connect securely from anywhere, whether at home, on the road, or in a coffee shop. A site-to-site VPN links entire office networks together, so branch locations can operate as if they're part of the same corporate network.
Protocols like IPsec and SSL/TLS are commonly used to build these tunnels. Each ensures traffic is encrypted and authenticated, though they differ in how they operate.
Important:
VPNs provide security for traffic. But they don't manage performance, optimize paths, or control how traffic is routed beyond encryption. That's why they're often paired with broader networking solutions that can address those needs.
What is SD-WAN?
A software-defined wide area network, or SD-WAN, is a modern way to manage and secure WAN traffic.
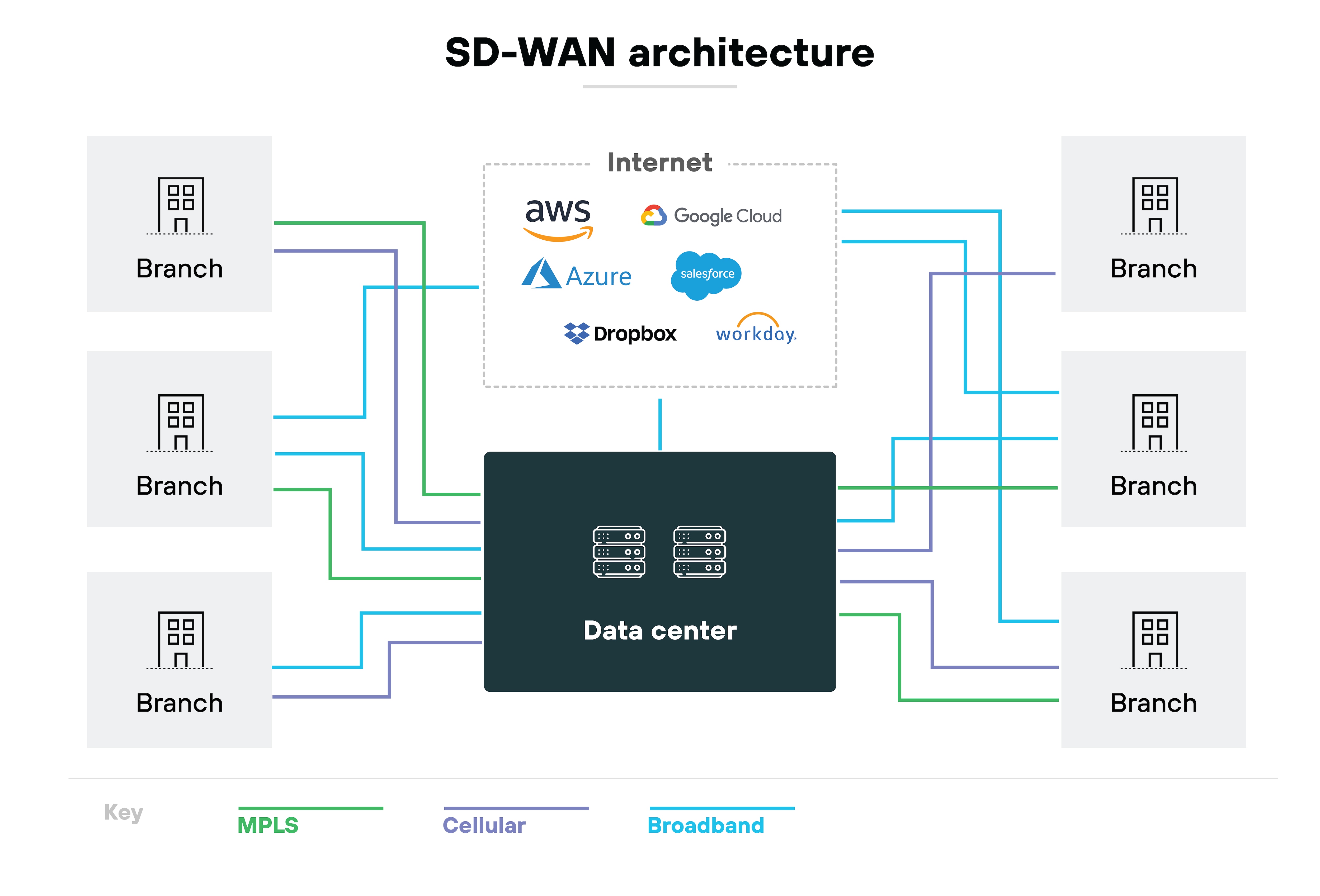
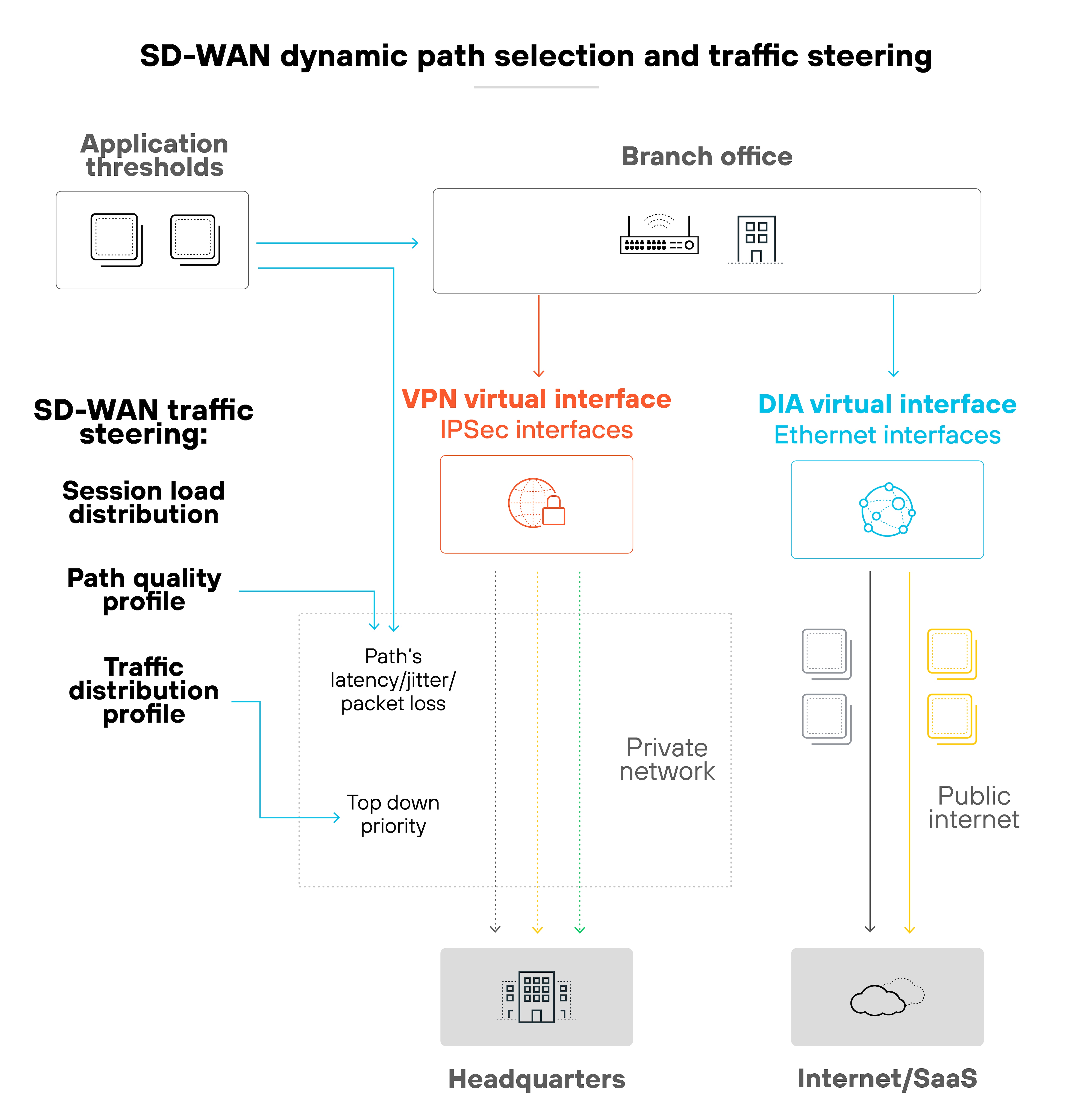
It uses software-defined policies to decide how traffic moves across available links. These links can include broadband, MPLS, or cellular. The software continuously monitors link performance and steers traffic along the best available path.
Essentially:
It adapts in real time. And ensures critical applications get the reliability they need.
Why does this matter?
Traditional WANs depend on static routing and fixed circuits. That model works–but struggles with cloud applications and distributed users.
SD-WAN was designed to solve that. It centralizes control, so administrators can set policies once and apply them everywhere. Which means changes roll out faster and more consistently across all sites.
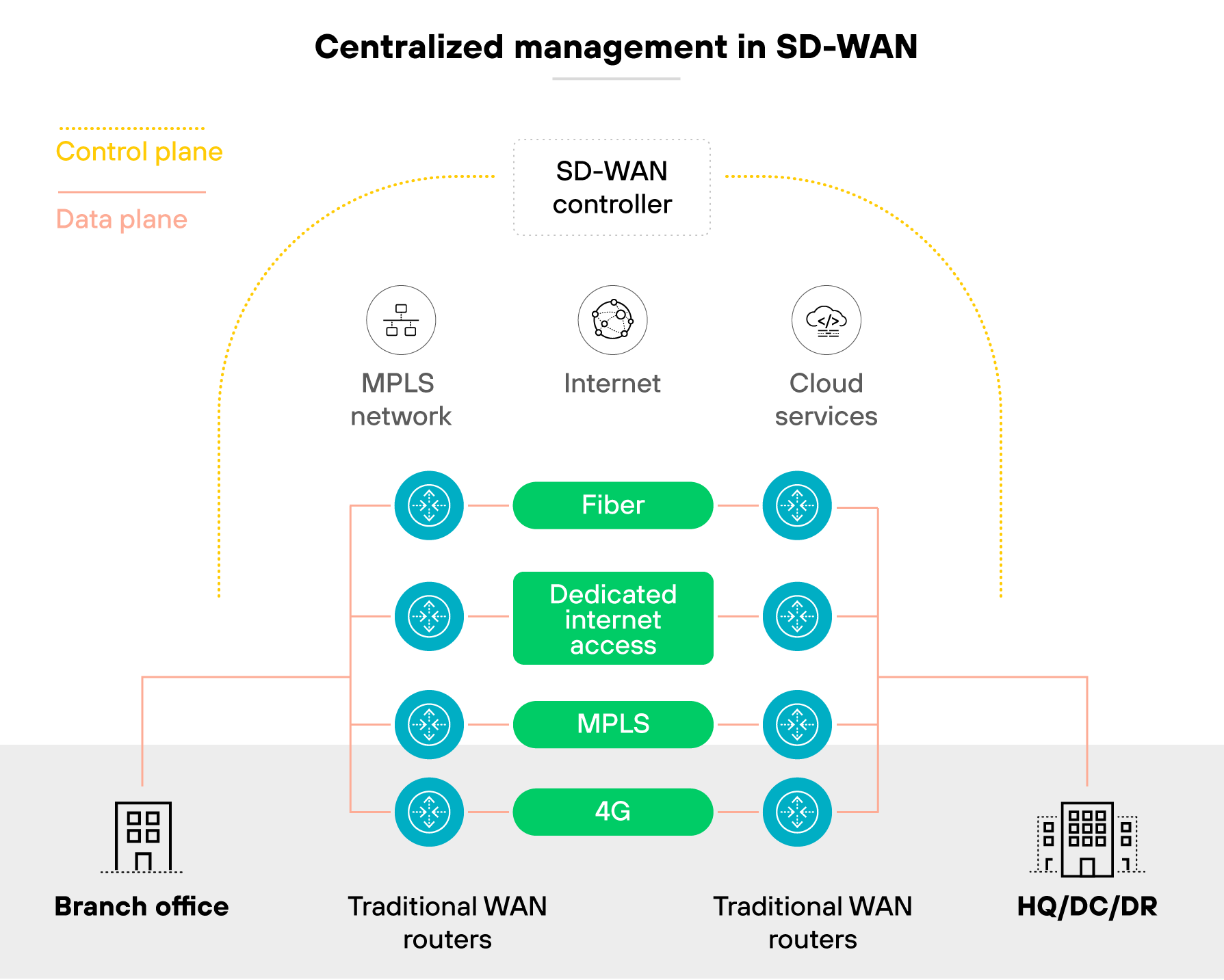
It also incorporates security into its overlay. SD-WAN often uses VPN tunnels to encrypt data between sites. It can integrate additional controls such as firewalls, segmentation, and traffic inspection.
The goal is straightforward. Provide flexible, policy-driven connectivity that supports branch offices, cloud workloads, and remote sites. Unlike a VPN, which is focused on secure tunnels, SD-WAN manages the entire WAN fabric. It delivers not just encryption but also visibility, control, and performance optimization across the network.
How are SD-WAN and VPN different?
A VPN and an SD-WAN both secure traffic. But they do so in very different ways.
| Comparison: SD-WAN vs. VPN |
|---|
| Feature | SD-WAN | VPN |
|---|---|---|
| Scope | Manages and secures traffic across the entire WAN | Secures traffic between two endpoints |
| Primary function | Uses software-defined policies to optimize traffic | Provides encrypted tunnels for confidentiality |
| Control | Centralized visibility, policy, and orchestration | Point-to-point, little centralized management |
| Performance | Dynamically selects best path based on performance | Does not manage path or performance |
| Typical use case | Multi-site networks, cloud workloads, large enterprises | Remote access or connecting a few sites |
| Integration | Often incorporates VPN tunnels within its overlay | Works as a standalone tool |
A VPN focuses on confidentiality between two points. SD-WAN provides centralized visibility and control across the WAN.
Put simply:
VPN is a tool. SD-WAN is a traffic management strategy, with varying levels of security features depending on the solution.
Think of it like this. A VPN is a lock on the front door. It protects the entry point. SD-WAN is the entire building's security and traffic system. It not only locks doors but also directs visitors, reroutes them if a hallway is blocked, and keeps track of who goes where.
That's the key difference.
VPN handles secure connectivity in isolation. SD-WAN orchestrates the entire WAN, often using VPN tunnels inside its fabric to secure branch-to-branch or branch-to-cloud connections.
Can SD-WAN and VPN work together?
Yes. SD-WAN and VPN aren't mutually exclusive.
As explained, SD-WAN often relies on encrypted tunnels that resemble VPN connections. These tunnels secure the overlay fabric between sites, branches, and data centers.
In practice, the underlying mechanism for this encryption is frequently IPsec—the same protocol used in traditional VPNs. Which means SD-WAN incorporates VPN-like functionality as part of its design.
On the other hand, organizations may still need VPN outside of the SD-WAN fabric. For instance, a remote access VPN lets individual users connect securely from laptops or mobile devices.
SD-WAN can then treat that traffic like any other flow, applying policies and steering it over the best available path. Site-to-site VPNs also fit naturally within SD-WAN overlays, adding encryption while benefiting from centralized orchestration.
Keep in mind: integration is common. Many enterprises run SD-WAN for branch and cloud connectivity while continuing to use VPN for mobile users. The two technologies complement each other instead of competing.
Is SD-WAN replacing VPN?
Not exactly. VPN is still widely used.
A VPN remains a common way for remote workers to connect securely to corporate networks. That capability is still essential when employees need point-to-point secure access.
On the other hand, SD-WAN provides an expanded model. It can use VPN tunnels inside its overlay, but it adds intelligence: path selection, performance monitoring, and orchestration across multiple transport types.
The takeaway: VPN is still part of the toolbox. But SD-WAN integrates it into a larger design for branch, cloud, and data center connectivity.
The reality is that VPN's role is shifting. With more applications in the cloud, the hub-and-spoke model of traditional remote access VPN is less efficient. SD-WAN, and increasingly SASE, address these limitations by steering traffic directly and enforcing consistent security.
The trend points to VPN becoming less central. But not disappearing. It continues to serve remote access and site-to-site use cases while SD-WAN takes the lead in overall WAN architecture.
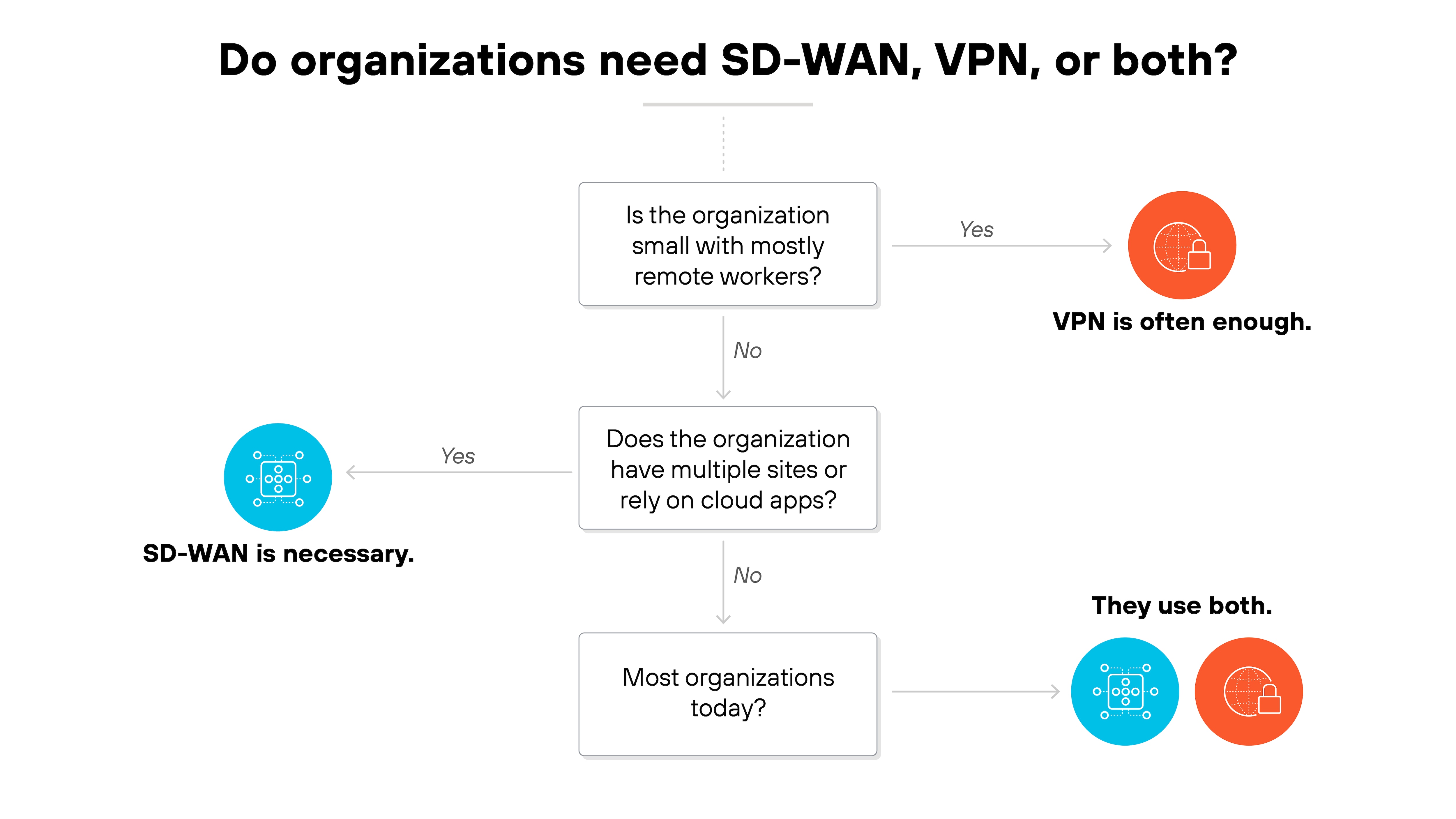
When is VPN enough, when is SD-WAN necessary, and do you usually need both?
A VPN and SD-WAN serve different purposes. So the real question is not which is better, but which is appropriate for the situation.
When is VPN enough?
VPN is often sufficient in smaller environments. If the primary need is secure remote access, a VPN can handle it. For organizations with only a few sites and minimal reliance on cloud applications, it may provide all the connectivity required.
When is SD-WAN necessary?
SD-WAN becomes important as networks grow more complex. Multiple branch offices, widespread SaaS adoption, and hybrid or multi-cloud environments create demands that exceed what simple VPN links can handle. In these cases, network-wide policy enforcement and dynamic traffic control make SD-WAN the more effective choice.
Do you usually need both?
Yes. Most enterprises use them together. VPN covers remote access for individual users, while SD-WAN manages connectivity and performance across sites and cloud resources. The combination balances security, scalability, and consistency.
