What Is SD-WAN Architecture? Components, Types, & Impacts
SD-WAN architecture is the logical design of a software-defined wide area network that separates the control plane from the data plane.
It defines how network components like controllers, orchestrators, and edge appliances interact to create secure, efficient connections across diverse transport links.
The architecture provides the framework for applying policies, steering traffic, and integrating with cloud or data center environments.
What are the main components of SD-WAN architecture?
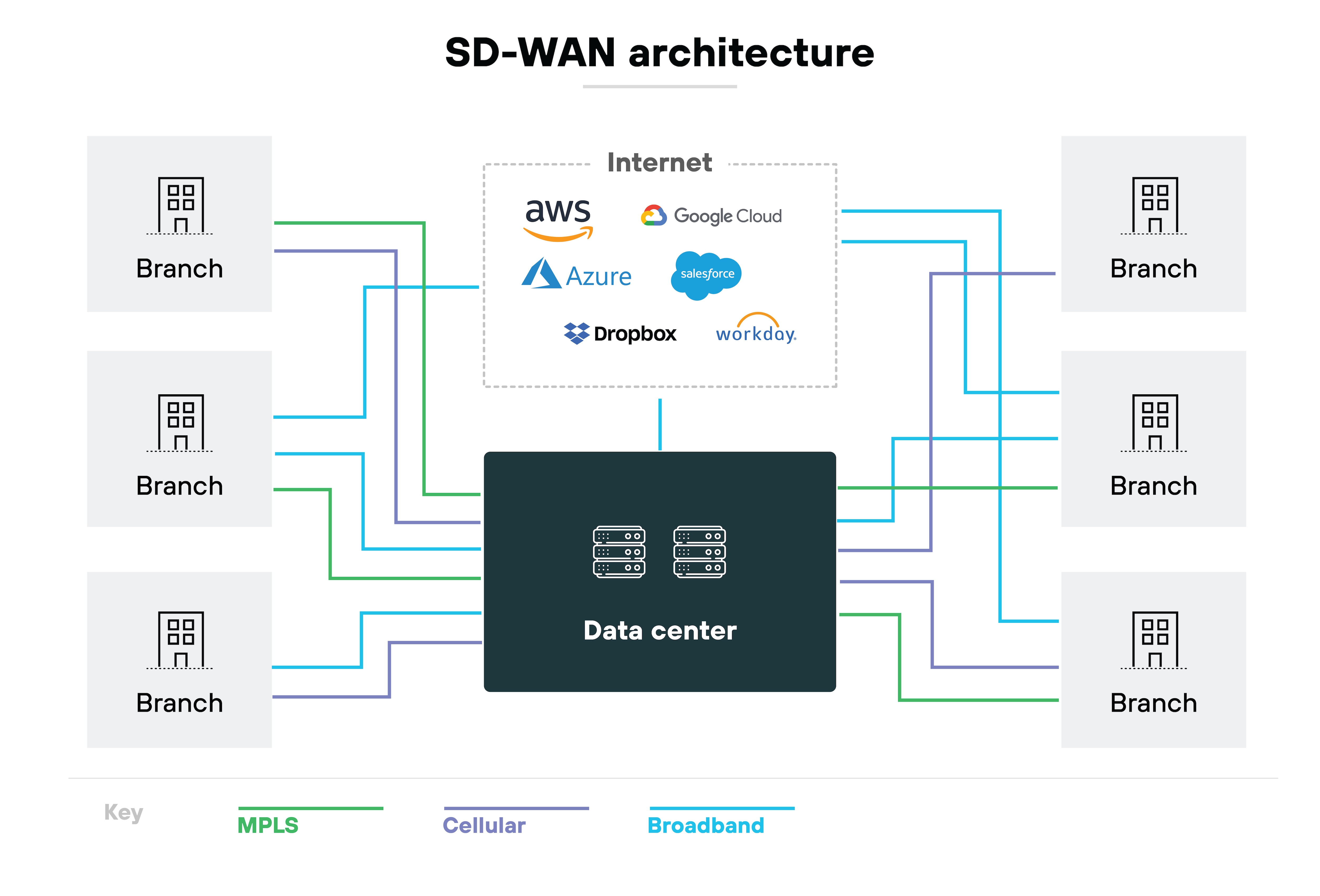
The main components of SD-WAN architecture are the data plane and the control plane. Functional components include the edge, controller, orchestrator, and optional gateways or points of presence (PoPs).
Here's how it works.
SD-WAN architecture is built around the separation of planes.
The data plane is where traffic is forwarded. It moves packets across the network based on rules already in place.

The control plane is where those rules are defined. It centralizes decision-making and pushes instructions down to the devices that handle the actual traffic.
In other words: The control plane decides, the data plane delivers.
Now to the specific roles these components play in the architecture:
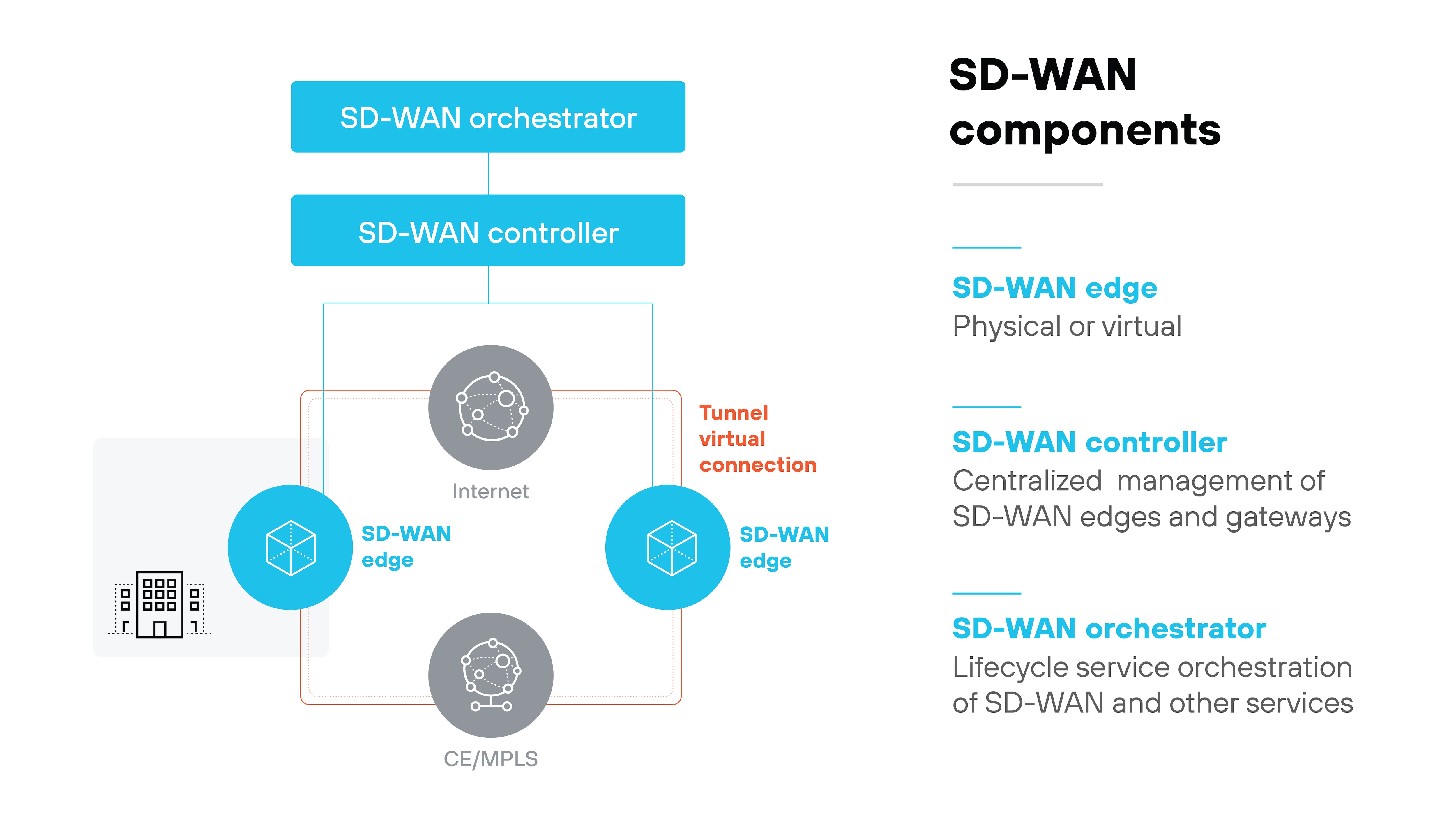
- The SD-WAN edge is the point where the network connects to a branch, a data center, or a cloud location. Edge devices handle policy enforcement and forwarding for the traffic that enters or leaves.
- The controller provides centralized visibility and policy definition. It's the administrative hub. Operators use it to describe how applications and traffic should be treated across the WAN.
- The orchestrator focuses on lifecycle management. It applies configurations, distributes updates, and keeps the environment consistent. Important: Controller and orchestrator are often described as separate logical roles, but in practice vendors may combine them into a single function.
- Points of presence (PoPs) or gateways are optional nodes that extend the network, improve routing, or connect branches to a backbone. For example: A PoP can take branch traffic off the public internet and route it through a private backbone for lower latency. But not all SD-WAN architectures include them.
Each of these elements ties back to the SDN principle of separating logic from forwarding. The edges enforce. The controller defines. The orchestrator maintains. Optional gateways expand reach.
Together, they form a framework that makes SD-WAN flexible, centrally managed, and cloud-ready.
- What Is an SD-WAN Appliance? | SD-WAN Hardware & Equipment
- What Is an SD-WAN Gateway? | Definition, Explanation, Use Cases
- What Are the Differences Between SD-WAN and SDN?
What are the different types of SD-WAN architecture?
SD-WAN architecture can be deployed in different ways depending on where key functions reside, primarily:
- On-premises
- Cloud-enabled
- Cloud-enabled with a backbone
Let's dig into the details of each.
On-premises SD-WAN
The first model is on-premises SD-WAN.
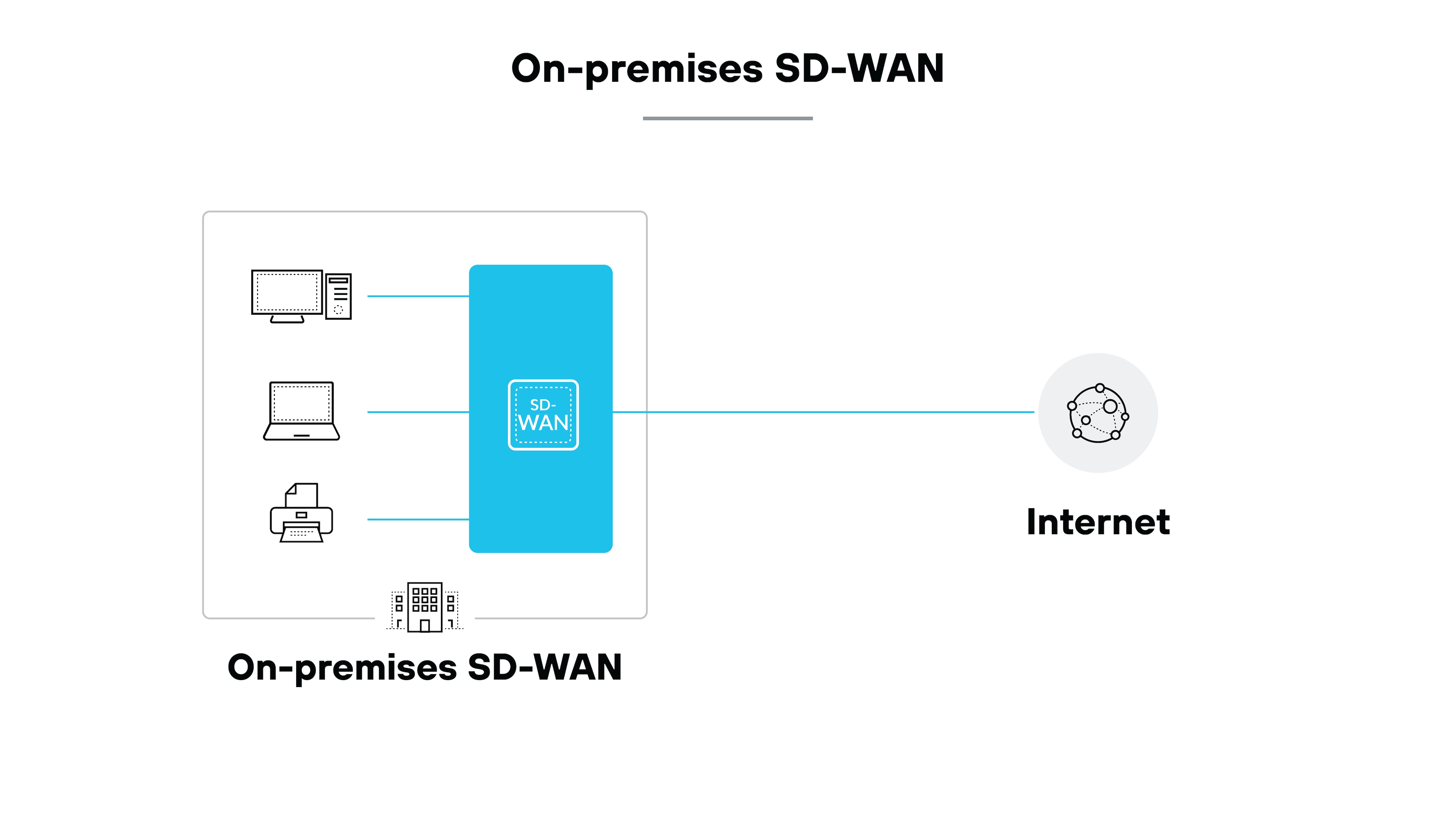
In this setup, the SD-WAN appliance sits directly at the site. It handles routing, policy enforcement, and control locally.
The advantage is direct oversight of data paths. Which means traffic stays within the organization's boundary before reaching the broader network.
However, because control is localized, this model can limit efficiency when workloads are heavily cloud-based or geographically distributed.
Cloud-enabled SD-WAN
The next approach is cloud-enabled SD-WAN.
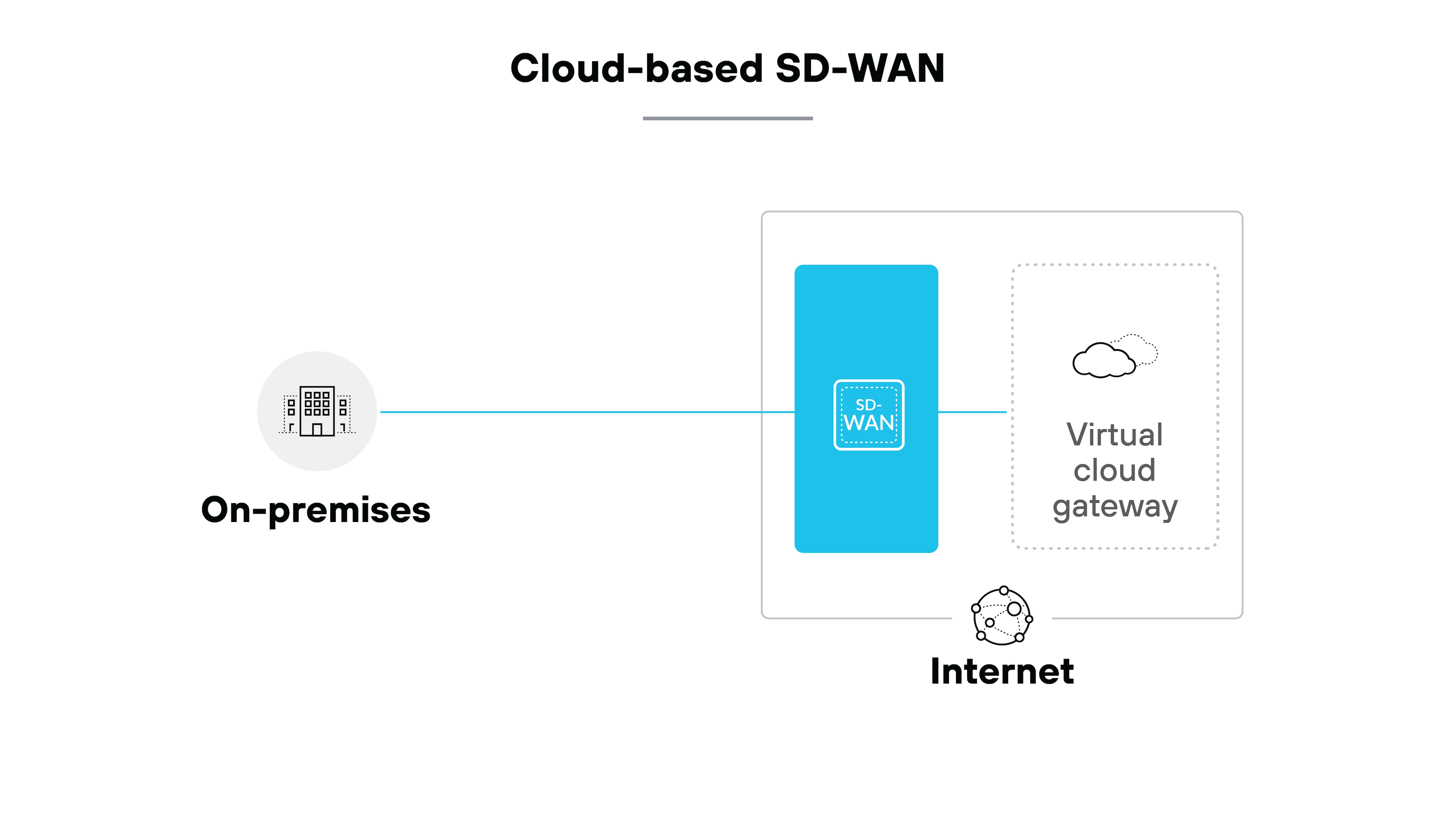
Here, traffic is directed through a virtual gateway hosted in the cloud. This allows branch locations to connect to SaaS or cloud workloads more efficiently.
The control plane can reside in the cloud as well, which provides centralized oversight across sites. The main trade-off is that traffic to cloud services is optimized, but traffic between on-premises sites may not benefit in the same way.
Cloud-enabled SD-WAN with a backbone
Finally, there's cloud-enabled SD-WAN with a backbone.
This model introduces points of presence (PoPs) that connect branches into a private backbone.
PoPs let traffic exit the public internet earlier and ride a more predictable, lower-latency path. For example: a branch can forward traffic to the nearest PoP, which then uses the backbone to reach another region.
This reduces jitter and improves performance for time-sensitive applications. The trade-off is dependency on the backbone provider's coverage.
In summary: Each deployment type reflects where control and data paths intersect—locally on-premises, in the cloud, or through PoPs with a backbone. The right choice depends on whether traffic is primarily site-to-site, cloud-focused, or global in scope.
How does SD-WAN architecture affect performance and connectivity?
SD-WAN architecture directly shapes how traffic moves and how applications perform. The design choices behind the architecture determine latency, reliability, and user experience.
Let's start with the underlay and overlay.
The underlay is the physical transport such as MPLS, broadband, or LTE. The overlay is the virtual fabric SD-WAN builds on top.
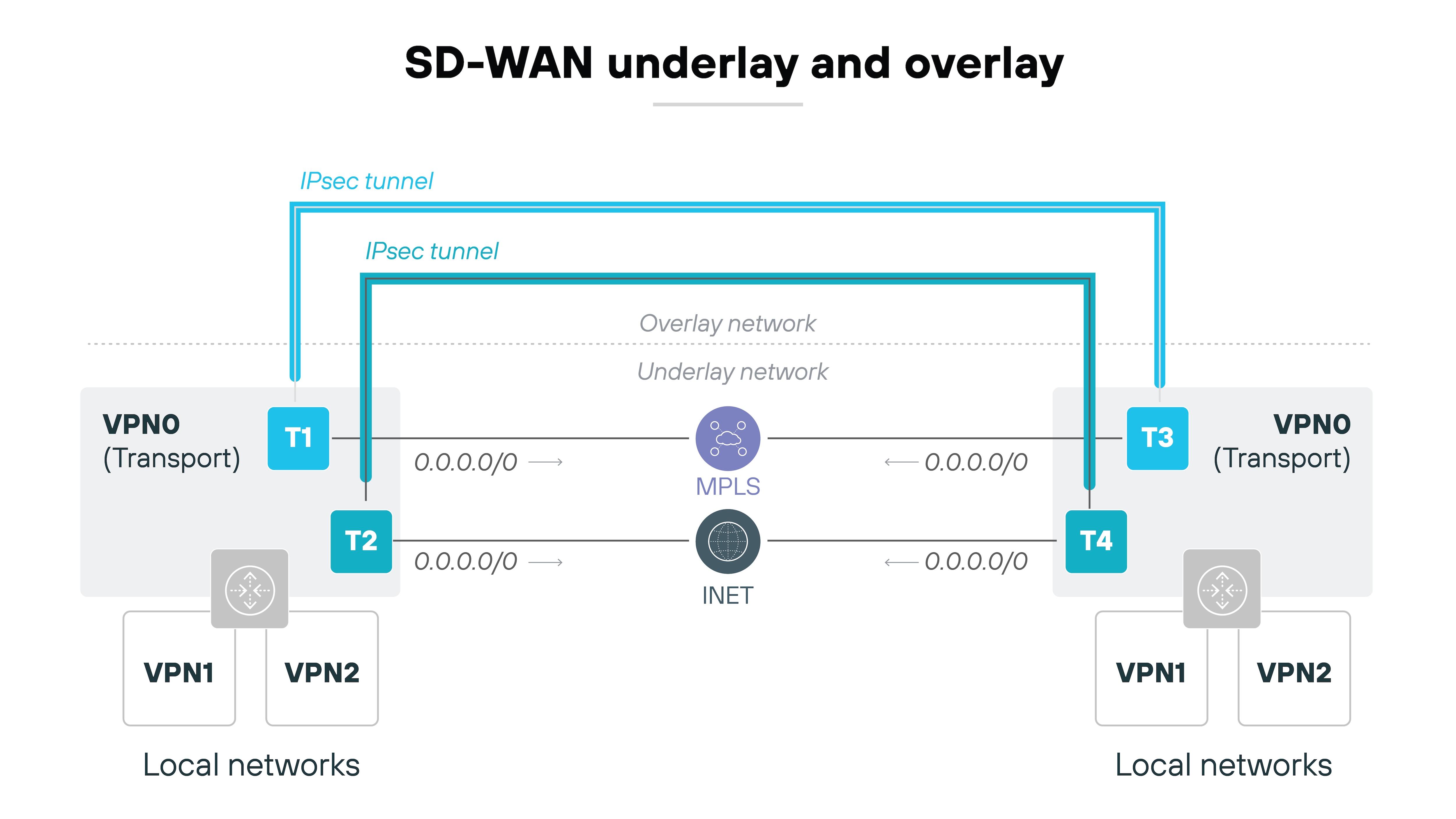
Why does this matter?
Because the overlay can steer traffic across multiple underlay links and shift flows when conditions change. That flexibility is a core reason SD-WAN can maintain performance during congestion or loss.
Here's how it works:

Now let's consider the path to applications.
Traditional WANs often backhauled traffic to a central data center before sending it to the cloud. But SD-WAN can instead support direct-to-cloud paths. So latency drops, bandwidth use improves, and SaaS access becomes more predictable.

It's worth noting: The extent of these improvements depends on where the control plane resides and how policies are written.
Points of presence and private backbones add another layer.
If the architecture includes PoPs, branch traffic can exit the public internet earlier. From there, it may traverse a provider's backbone with lower jitter and packet loss. The outcome is a smoother experience for voice, video, and other real-time applications.
However, performance varies depending on the coverage of those PoPs.
Policies tie it all together.
Application-aware routing lets the controller steer flows based on metrics like loss or delay. For example: Business-critical voice may be sent over the lowest-latency link, while bulk file transfers use cheaper bandwidth.
Meanwhile, zero-touch provisioning ensures these policies are deployed consistently, reducing the risk of misconfiguration across sites.
In short: SD-WAN architecture affects performance and connectivity by defining how paths are selected, how traffic is prioritized, and how consistently those rules are applied. The architecture is what turns a mix of underlay transports into a coherent, application-aware network.