What Is the Difference Between IoT and OT Security?
IoT security focuses on protecting connected devices and their data, while OT security safeguards systems controlling physical industrial processes.
IoT security is tasked with ensuring the integrity and confidentiality of data across internet-connected devices, emphasizing strong authentication and encryption. OT security prioritizes the availability and safety of systems that monitor and control physical operations.
What Is IoT Security?
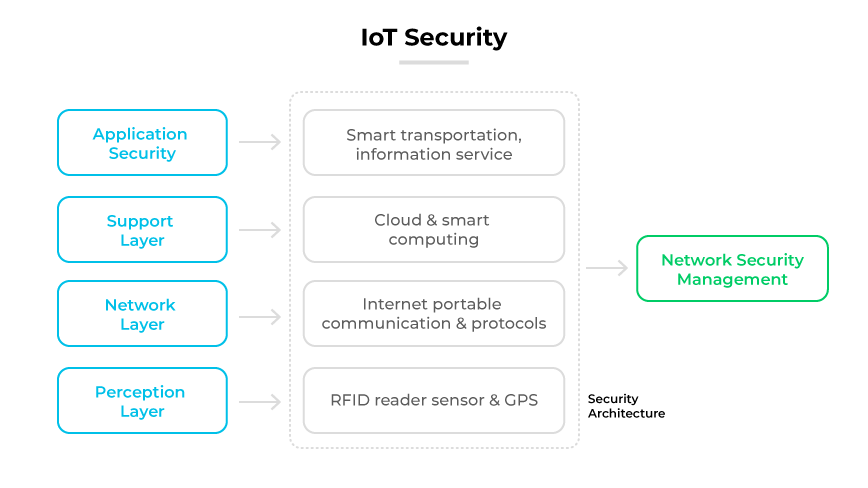
IoT security encompasses measures designed to protect internet-connected devices and the networks they inhabit. These safeguards are critical because devices ranging from consumer electronics to industrial sensors often lack built-in security features. IoT devices generate and process significant amounts of data. Consequently, these devices can become vulnerability points within broader network infrastructures.
The nature of IoT device connectivity increases the risk of cyber threats like data breaches, unauthorized access, and denial of service attacks. Using robust security protocols mitigates these risks. Effective IoT security incorporates encryption, strong authentication mechanisms, and real-time monitoring to ensure the confidentiality, integrity, and availability of data.
Adapting to and countering emerging threats is an integral aspect of IoT security. As the IoT ecosystem expands, so does the potential attack surface for cyber threats. IoT security focuses on advancing and implementing technologies that address existing challenges but also are adaptable to the evolving landscape of threats and vulnerabilities.
What Is OT Security?
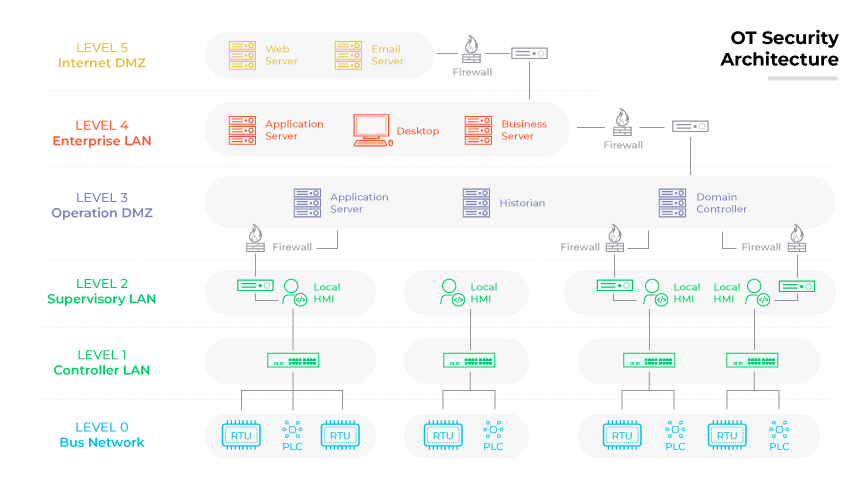
OT security involves safeguarding operational technology (OT) systems, including Supervisory Control and Data Acquisition (SCADA) systems and Industrial Control Systems (ICS), that are vital in sectors like manufacturing, utilities, and transportation. These systems control and monitor industrial processes operations. With the rise of connectivity, ensuring the safety and integrity of OT assets systems has become paramount. Robust security protocols are necessary to guard against an array of cyber threats and vulnerabilities.
OT security implementation addresses specific challenges inherent in the industrial environment. Unlike IT systems, OT systems prioritize operational efficiency and safety. OT security focuses on safeguarding physical systems that monitor and control operations, ensuring they are resistant to unauthorized access and cyber threats while maintaining operational continuity.
The future of OT security will be influenced by continuous adaptation to the dynamic landscape of threats, with a focus on minimizing risks while maximizing operational efficiency. Strategies are expected to include real-time monitoring of the operational processes, implementing multi-layered security protocols, and ensuring compliance with industry standards and regulations. As the integration between IT and OT continues to deepen, OT security tools and tactics should aim to be resilient, adaptable, and comprehensive to safeguard the critical infrastructure and operations it supports.
The Role of IoT in OT
The intersection of the Internet of Things (IoT) and Operational Technology (OT) represents a significant shift in the industrial landscape. IoT introduces networking capabilities to traditional OT systems, transforming them into intelligent units capable of collecting, transmitting, and analyzing data. Unlike conventional OT equipment, IoT-enabled devices enhance data mobility and accessibility, offering real-time insights that can be used to improve operational efficiency and decision-making.
In the context of industrial operations, the infusion of IoT into OT is evident in the enhanced functionality of sensors and other data collection units. Smart sensors, equipped with advanced data processing and communication capabilities, collect and relay operational data seamlessly across networks. This interconnectivity facilitates an integrated ecosystem where data flows unimpeded from the operational frontlines to analytics and decision-making platforms. Seamless data transmission aids in predictive maintenance, real-time monitoring, and other operational enhancements that contribute to optimized performance and reduced downtimes.
The fusion of IoT and OT is instrumental in the propagation of edge computing in industrial settings. IoT devices equipped with edge computing capabilities analyze and process data on-site, negating the need for data transmission to centralized processing hubs. This not only reduces latency but ensures that real-time data is utilized promptly for immediate operational adjustments
What Are the Differences Between OT and IoT Security?

Operational Technology (OT) and Internet of Things (IoT) security, though intertwined, possess distinct characteristics and challenges. OT security safeguards industrial and critical infrastructure. It focuses on the specialized hardware and software designed to monitor and control physical devices and processes. The pivotal concern is maintaining systems availability and safety. OT security is especially imperative in OT environments where system interruption or failure could lead to catastrophic outcomes.
IoT security, on the other hand, concentrates on the vast array of connected devices that collect, transmit, and analyze data. These devices, often consumer-oriented, are networked and internet-enabled, amplifying the attack surface for potential cyber threats. Security for IoT involves safeguarding the integrity and confidentiality of data. While OT is primarily concerned with system availability, IoT security grapples with the myriad of devices, each with unique vulnerabilities, enhancing the complexity of securing them against cyber threats.
In terms of remediation and defense strategies, OT and IoT also exhibit variations. OT systems, often being older and embedded in critical infrastructures, may be challenging to update or patch, making anomaly detection and OT network segmentation crucial. IoT devices, conversely, benefit from more flexibility in updates but are often less secure by design. Consequently, changing default credentials and regular software updates are common practices in IoT security. Although distinct, the convergence of OT and IoT is inevitable, underscoring the need for comprehensive security approaches that encapsulate the intricacies of both domains.
