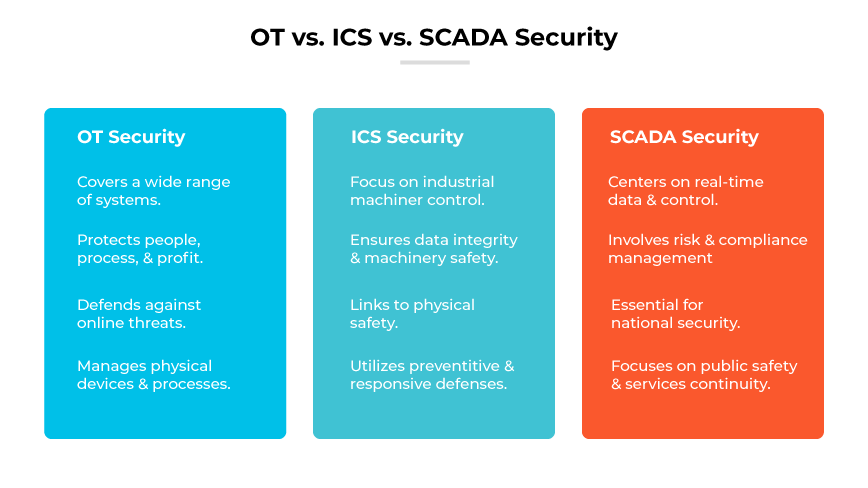
What Are the Differences Between OT, ICS, & SCADA Security?
OT security guards systems, ICS security ensures machinery and data safety, and SCADA security emphasizes real-time control and public safety.
OT, ICS, and SCADA security collectively ensure the integrity, safety, and real-time control of operational, industrial, and public service systems.
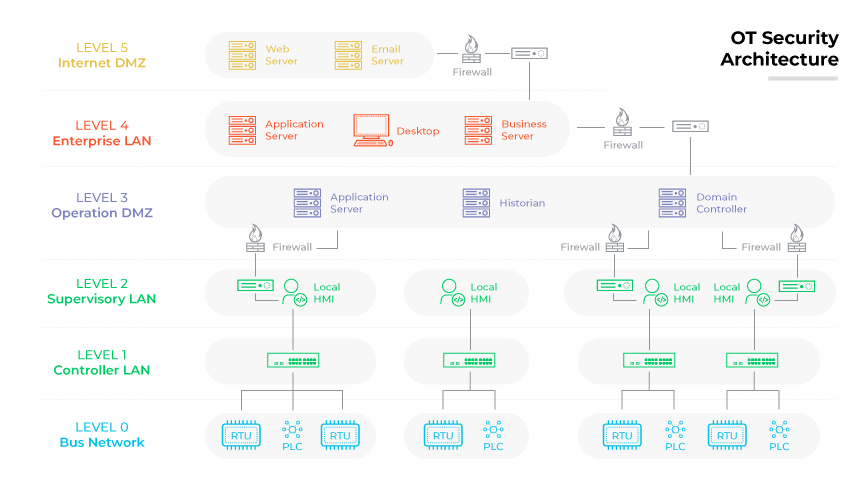
OT security involves the implementation of measures and controls to safeguard operational technology (OT) systems from cybersecurity threats. These systems automate and manage industrial processes equipped with specialized software. OT systems play a crucial role in critical infrastructure management.
IT and OT convergence has increased the need for OT security. Operational technology systems were once isolated and immune to online threats. The integration has resulted in enhanced automation, but also increased vulnerability to cyber threats. OT assets are now part of complex networks, exposing them to threats like malware and ransomware attacks. Security in this domain is complicated by OT systems diversity, including industrial control systems (ICS) like supervisory control and data acquisition (SCADA) systems and distributed control systems (DCS). Breaches can lead to disastrous consequences, including operational downtime, physical damage, and safety risks to personnel and the surrounding environment or community. System compromise can severely impact an organization’s operations and revenue.
Security for OT encompasses technologies and practices that protect assets and information, monitor and control physical OT devices, and manage processes and events. This includes various security technologies and functions, including next-generation firewalls, security information and event management systems, and access control, for example.
Despite the complexities introduced by the convergence of IT and OT networks, effective OT security is possible with comprehensive visibility across the attack surface and implementing security policies tailored to the unique OT environment requirements. The goal of OT security remains protecting processes, people, and profit while minimizing security vulnerabilities and incidents.
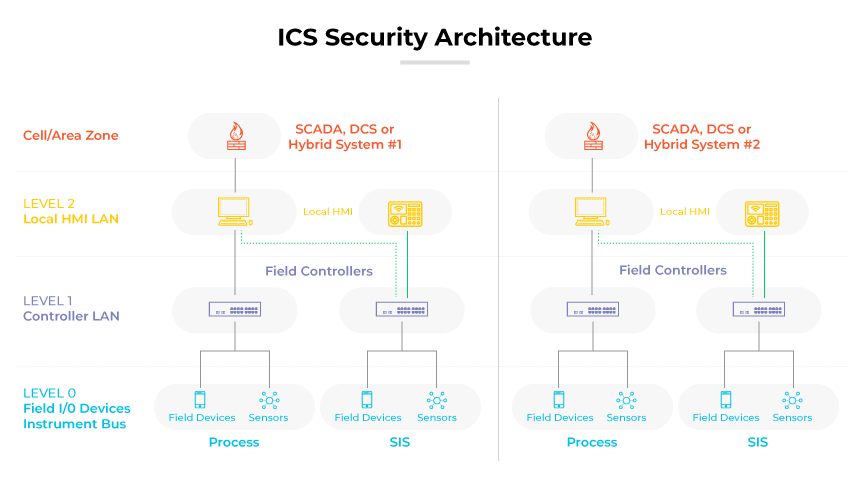
ICS security pertains to the protection of industrial control systems. ICS environments include a combination of hardware and software engineered to oversee and manage machinery and processes across a diverse range of industries. ICS systems are intrinsic to the operation of power plants, manufacturing facilities, and other critical infrastructure. Security measures instituted are designed to guard these complex systems against cyber threats, ensuring the integrity of data and the safety and continuous operation of the machinery they control.
The core of ICS security is embedded in safeguarding the systems and networks that are integral to industrial operations. Given that ICS environments and control systems are intricately linked with the machinery they manage, security is not just digital. ICS security includes ensuring the physical safety of the operational environment.
With the advent of networking and the integration of these systems into broader IT ecosystems, the need for robust security protocols has intensified. Each component, from Programmable Logic Controllers (PLC) to Human-Machine Interfaces (HMIs), requires specific security measures to mitigate the risks of unauthorized access, data breaches, and system malfunctions.
A compromise in ICS security doesn’t just risk data integrity but can lead to the disruption of industrial processes, leading to operational downtime, financial losses, and at its extreme, poses threats to human safety. The defense mechanisms and cyber security solutions in place are designed to be both preventive and responsive. This approach ensures potential threats are identified and mitigated before they can impact the system. Responsive measures remain at the ready to contain and neutralize threats that breach initial security perimeters.
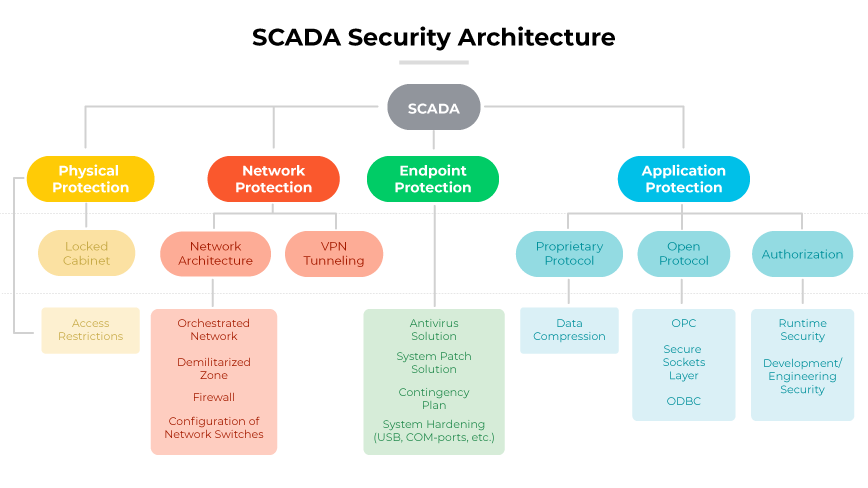
SCADA security is centered on protecting Supervisory Control and Data Acquisition systems, essential for automating and managing complex industrial processes. These networks are instrumental in utilities, manufacturing, and transportation. SCADA systems are designed for real-time data collection, process monitoring, and operational control. With the adoption of open architectures and IP-based communications, the vulnerability of SCADA systems to cyber threats has increased. This makes security protocols crucial for safeguarding operational integrity and public safety.
A complete SCADA security framework integrates governance, risk management, and compliance controls alongside specific SCADA and data application security measures. It ensures the resilience and adaptability of defenses to counter evolving cyber threats while upholding system availability and process integrity. Third-party vendors are often responsible for developing and maintaining SCADA systems. They are also held to stringent security standards, reinforcing the overall defense architecture.
The potential consequences of SCADA breaches are like those associated with OT and ICS systems. Consequences include operational disruptions, financial losses, and public safety risks. These systems control and monitor essential services such as water, electricity, and transportation. Consequently, SCADA security extends beyond data and system protection, linking directly to the uninterrupted provision of critical services and the physical safety of the population.
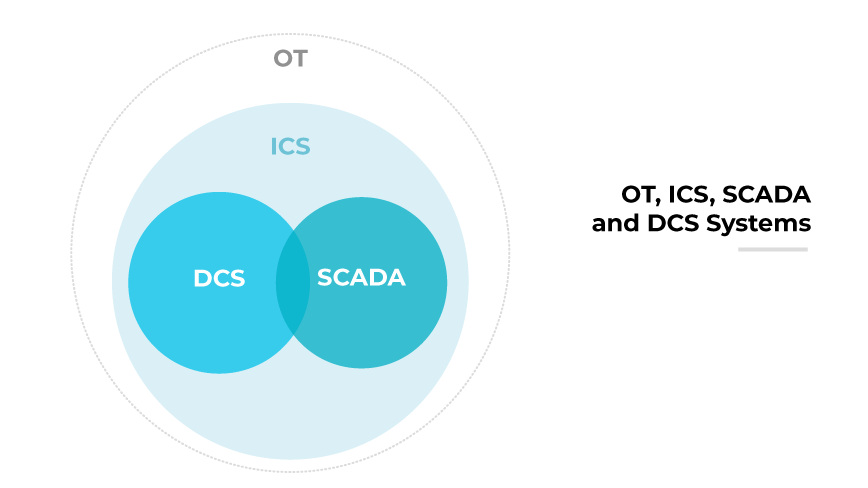
Operational Technology (OT), Industrial Control System (ICS), and Supervisory Control and Data Acquisition (SCADA) security each serve distinct but overlapping roles in safeguarding industrial operations and critical infrastructure.
OT security focuses on securing the systems that manage, monitor, and control industrial operations, particularly in the context of increased connectivity and integration with information technology systems. It encompasses a wide range of systems, including ICS and SCADA, and is concerned with protecting people, processes, and profit from cybersecurity threats.
ICS security, on the other hand, is more specialized. It specifically focuses on the systems that directly control industrial processes and machinery. These systems are essential to the operation of various sectors, from power generation to manufacturing. The security of ICS is paramount because the consequences of breaches are severe. Each component within an ICS network, from PLCs to HMIs, needs tailored security measures to counteract the unique threats they face due to their operational and network integration.
SCADA security is a subset of ICS security, focusing particularly on the systems used for real-time data acquisition, process control, and monitoring in various industrial settings. The security of SCADA is accentuated by its real-time operational needs and the critical services it supports. It is inherently connected to public safety and service continuity, demanding a multi-faceted approach that integrates governance, risk management, and compliance controls alongside technical and physical security measures.