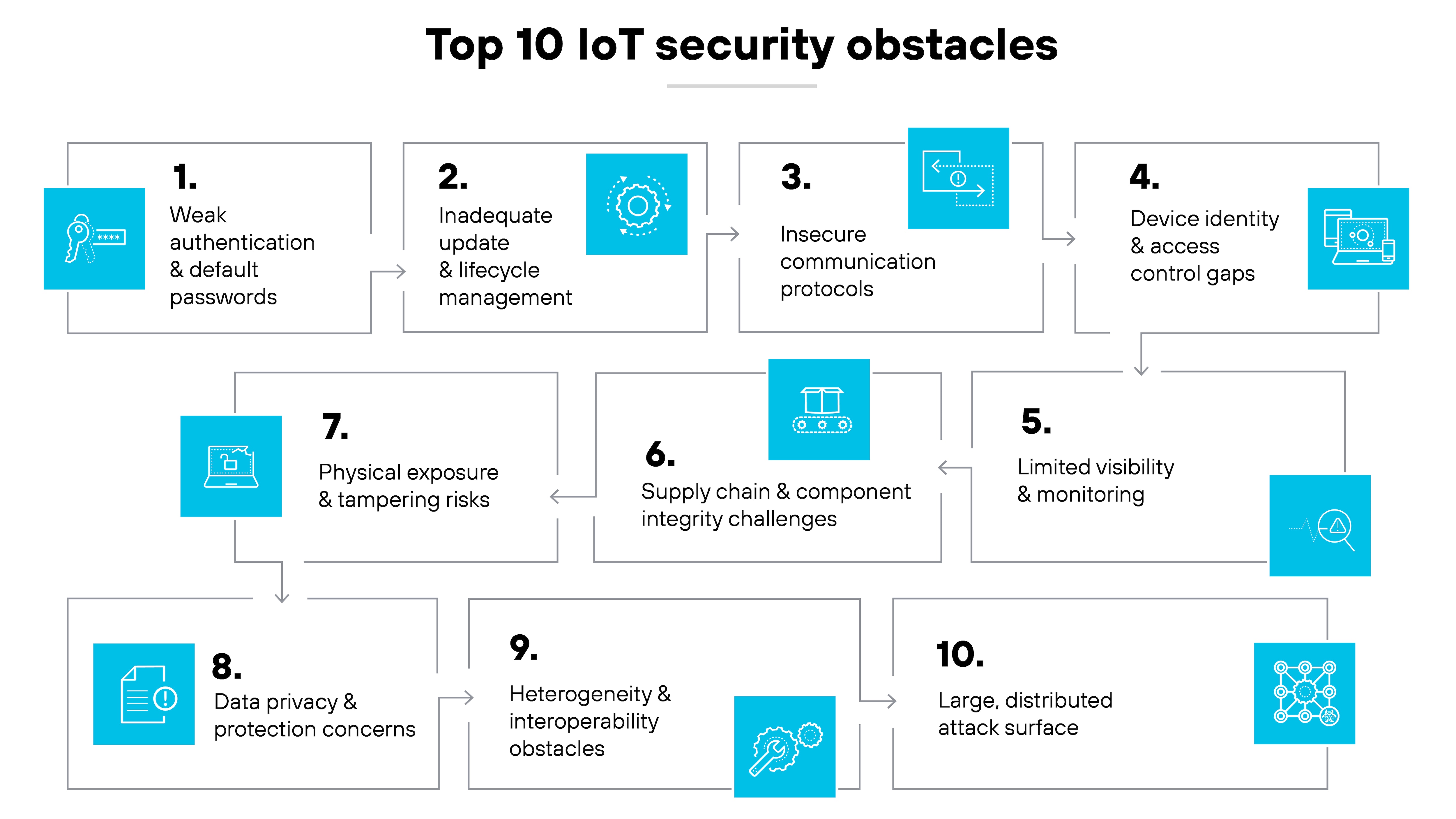
- 1. Why is IoT so difficult to secure?
- 2. 1. Weak authentication and default passwords
- 3. 2. Inadequate update and lifecycle management
- 4. 3. Insecure communication protocols
- 5. 4. Device identity and access control gaps
- 6. 5. Limited visibility and monitoring
- 7. 6. Supply chain and component integrity challenges
- 8. 7. Physical exposure and tampering risks
- 9. 8. Data privacy and protection concerns
- 10. 9. Heterogeneity and interoperability obstacles
- 11. 10. Large, distributed attack surface
- 12. IoT security issues FAQs
- Why is IoT so difficult to secure?
- 1. Weak authentication and default passwords
- 2. Inadequate update and lifecycle management
- 3. Insecure communication protocols
- 4. Device identity and access control gaps
- 5. Limited visibility and monitoring
- 6. Supply chain and component integrity challenges
- 7. Physical exposure and tampering risks
- 8. Data privacy and protection concerns
- 9. Heterogeneity and interoperability obstacles
- 10. Large, distributed attack surface
- IoT security issues FAQs
Top 10 IoT Security Issues: Challenges & Solutions
- Why is IoT so difficult to secure?
- 1. Weak authentication and default passwords
- 2. Inadequate update and lifecycle management
- 3. Insecure communication protocols
- 4. Device identity and access control gaps
- 5. Limited visibility and monitoring
- 6. Supply chain and component integrity challenges
- 7. Physical exposure and tampering risks
- 8. Data privacy and protection concerns
- 9. Heterogeneity and interoperability obstacles
- 10. Large, distributed attack surface
- IoT security issues FAQs
The primary IoT security issues and challenges include:
- Weak authentication and default passwords
- Inadequate update and lifecycle management
- Insecure communication protocols
- Device identity and access control gaps
- Limited visibility and monitoring
- Supply chain and component integrity challenges
- Physical exposure and tampering risks
- Data privacy and protection concerns
- Heterogeneity and interoperability obstacles
- Large, distributed attack surface
Each of these challenges represents a core obstacle to securing IoT—and each requires its own practical solution.
Why is IoT so difficult to secure?
Securing IoT is harder than securing traditional IT systems.
Why?
Because IoT changes the rules.
In fact, most IT leaders regard IoT as the most vulnerable component of their security frameworks. "
There are billions of devices, spread across homes, factories, hospitals, and cities. Each one adds another point that needs protection. Scale alone makes oversight a challenge.
Then there's the diversity. Devices come from thousands of vendors, with different hardware, software, and communication protocols. Which means consistent security practices are difficult to enforce.
IoT devices are also resource-constrained. Many run on limited power and processing, leaving little room for strong cryptography or advanced monitoring. And unlike laptops or phones, IoT devices often stay in service for a decade or more. Support rarely lasts that long.
Together, these realities explain why securing IoT is uniquely challenging—and why the following issues demand focused attention, along with practical solutions.
- What Is Industrial Internet of Things (IIoT) Security?
- What Is Internet of Medical Things (IoMT) Security? Overview
1. Weak authentication and default passwords
Many IoT devices still rely on weak authentication. Some come with simple numeric PINs. Others ship with the same factory-set password across thousands of units. The result is predictable. Attackers know the defaults and can find devices that never had their settings changed.
Why does this keep happening?
Convenience. Manufacturers want setup to be fast and easy. Which means devices often skip forcing users to create unique credentials. In practice, that tradeoff leaves a long-term vulnerability in place.
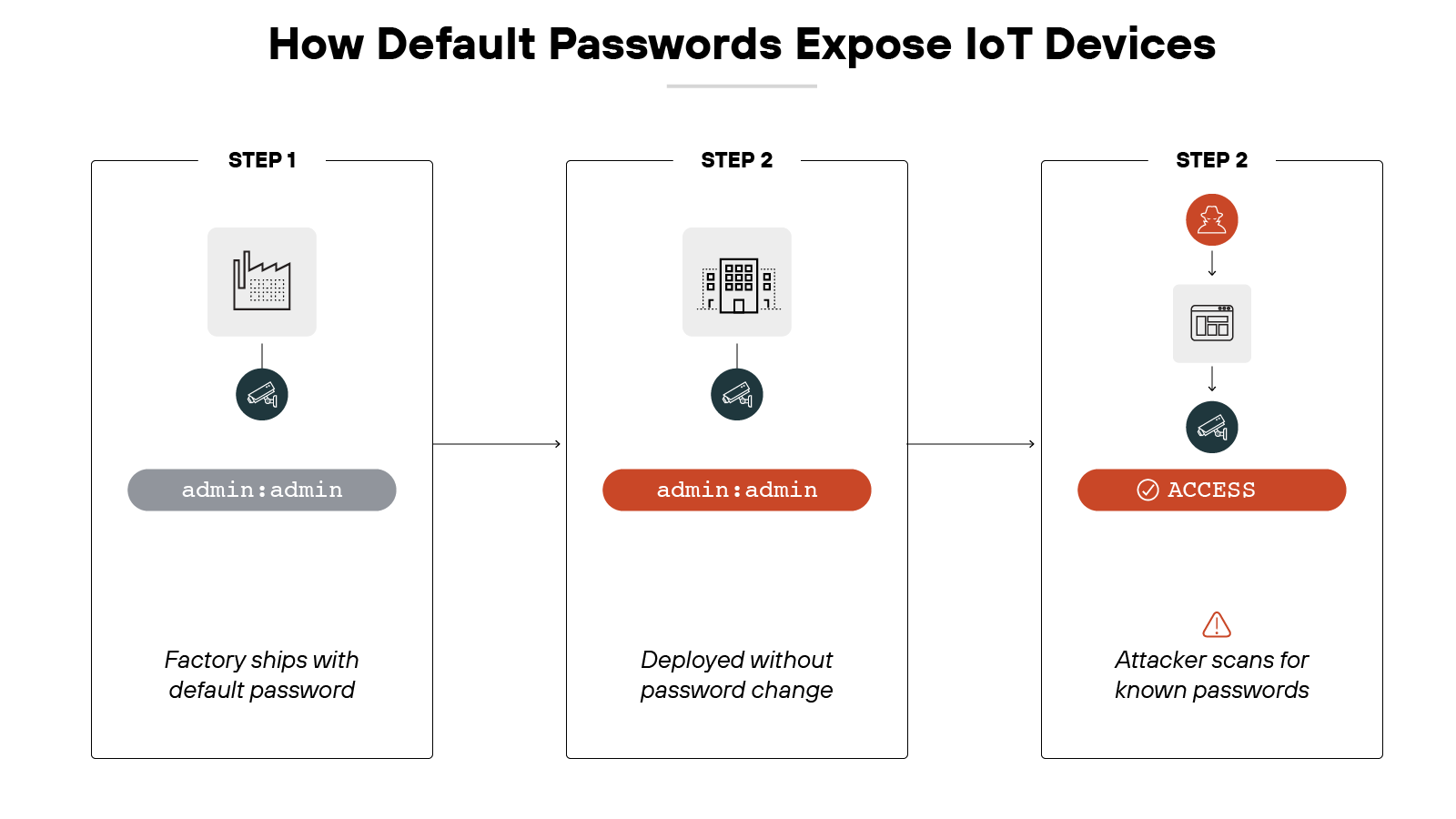
Weak authentication also shows up in other ways. Devices may not support multifactor authentication. They may lack the ability to assign strong, unique identities to each unit. Or they may fail to limit who can change security settings. Without these safeguards, it's much easier for an attacker to take control.
The problem isn't just poor design. It's also inertia. Once deployed, devices can run for years without anyone revisiting their authentication settings. A door lock, a sensor, or a smart appliance might stay online with its original credentials indefinitely.
In short: authentication is the first line of defense. If it's weak—or worse, universal—then every other layer of security is undermined before it even starts.
The fix starts with unique, strong credentials for every device. Setup should require users to change defaults before deployment. Support for multifactor authentication and stronger identity management can further reduce risk. And access to device settings should be restricted so that only authorized users can make changes.
2. Inadequate update and lifecycle management
IoT devices often lack reliable mechanisms for updates. Some ship with no patching process at all. Others require manual intervention that never happens in practice. That leaves many devices running outdated software long after vulnerabilities are known.
Support timelines are another issue. Vendors may stop providing updates after only a short period. Yet the devices themselves often remain in service for years. That mismatch means organizations end up with hardware still in use but no longer supported.
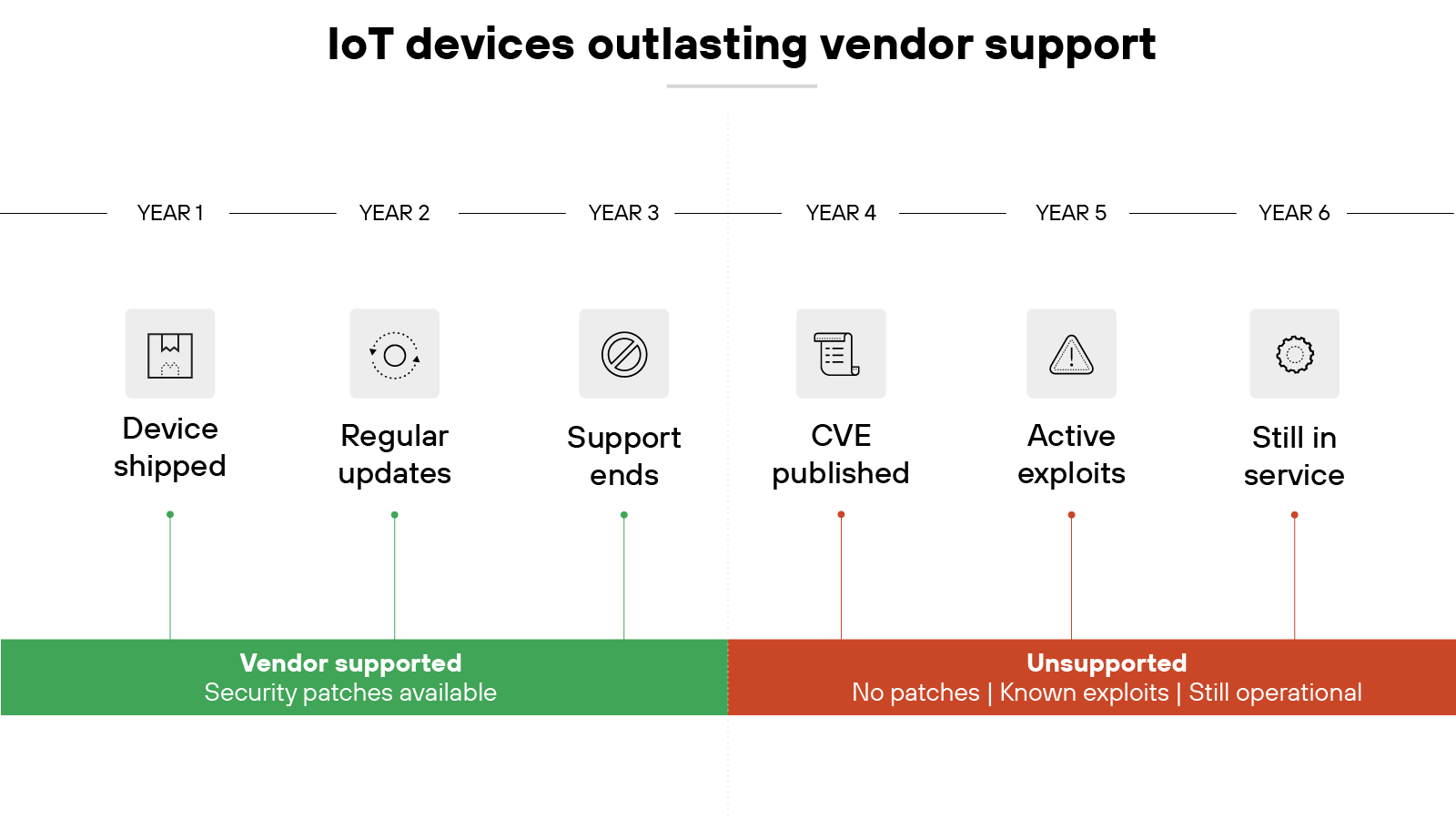
And the problem compounds over time. Devices can outlast the company that built them. Or their cloud-based services may be retired while the hardware keeps operating. In either case, security fixes stop arriving, but the device stays online and exposed.
Why does this matter?
Because without updates, even basic flaws remain exploitable. Attackers can take advantage of well-documented issues because they know many IoT systems will never receive a patch.
Organizations should prioritize devices with clear update policies and transparent support lifecycles. Procurement teams can require vendors to state how long patches will be delivered and how updates are applied. Network segmentation can further reduce exposure when support ends. And devices that no longer receive fixes should be retired or isolated before they become an unmanaged liability.
3. Insecure communication protocols
IoT devices often transmit data over the network without strong protections. In some cases, traffic is sent in plain text. That means anyone intercepting it can read sensitive information. In some situations, encryption is used but relies on outdated or weak algorithms. Either way, the data in transit is vulnerable.
Authentication between devices is another weak spot. Many protocols allow one-sided checks, where a device verifies the server but the server does not verify the device—or the other way around. The result is: attackers can impersonate a trusted system and insert themselves into the conversation.
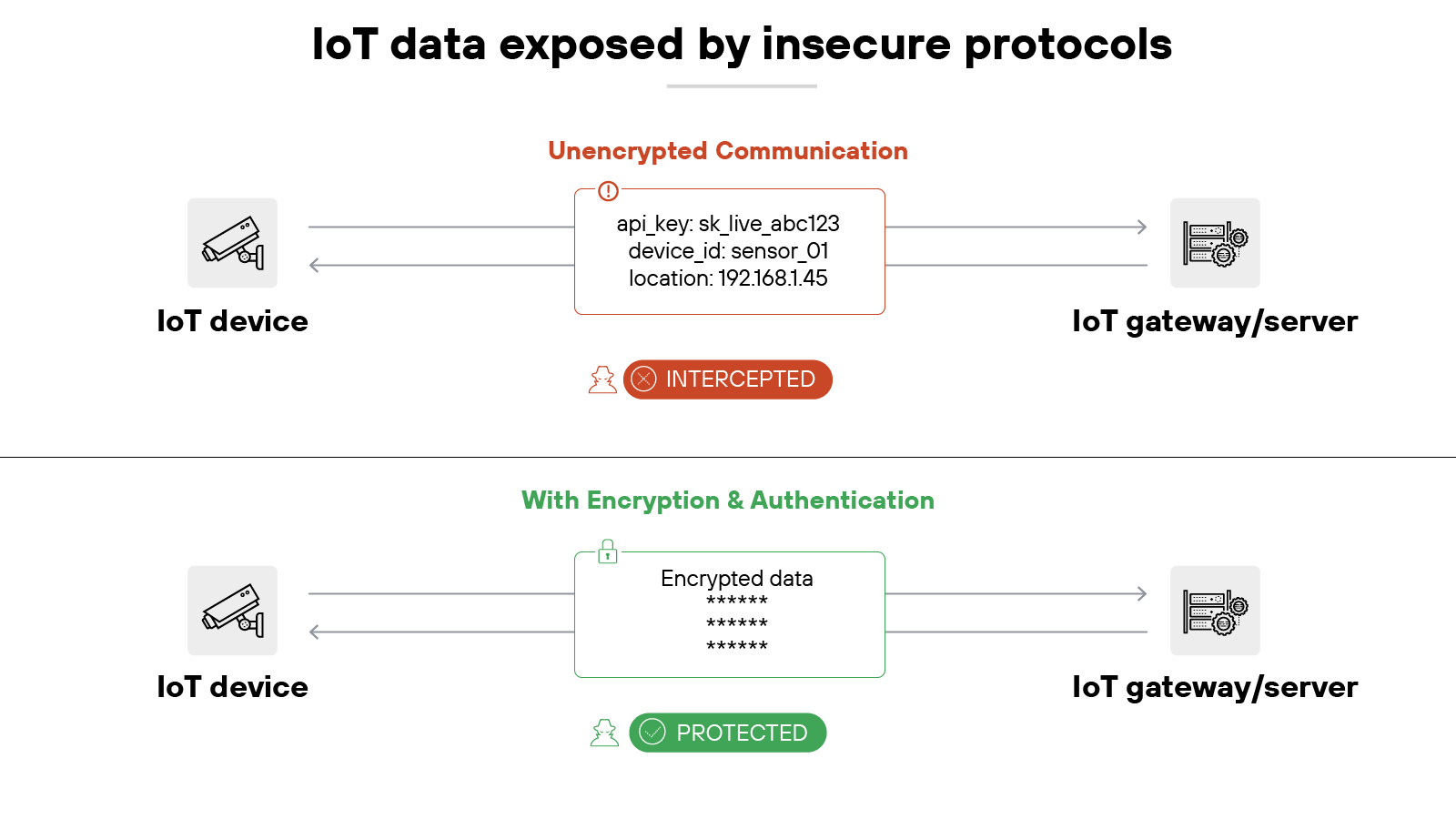
These gaps create opportunities for eavesdropping, tampering, or hijacking of sessions. For organizations, the result can be exposure of personal data, unauthorized control of devices, or use of compromised endpoints as footholds into the wider network.
To address this, organizations should favor IoT devices that support secure, modern communication standards. Protocols should enforce encryption by default, using strong algorithms that are regularly updated. Mutual authentication should be required so that both sides of the connection are verified. Where insecure protocols can't be avoided, segmenting those devices onto isolated networks can help reduce the impact of compromise.
4. Device identity and access control gaps
Every IoT device needs a way to be identified. In practice, many devices lack strong, unique identifiers. They may share generic IDs, rely on easily guessable values, or allow changes that break consistency over time. Without reliable identification, it becomes difficult to track, monitor, or secure devices at scale.
Access control is another challenge. Many IoT systems only support broad, all-or-nothing permissions. Which means: users or processes with access often have more privileges than they should. The absence of fine-grained controls makes it hard to enforce the principle of least privilege.
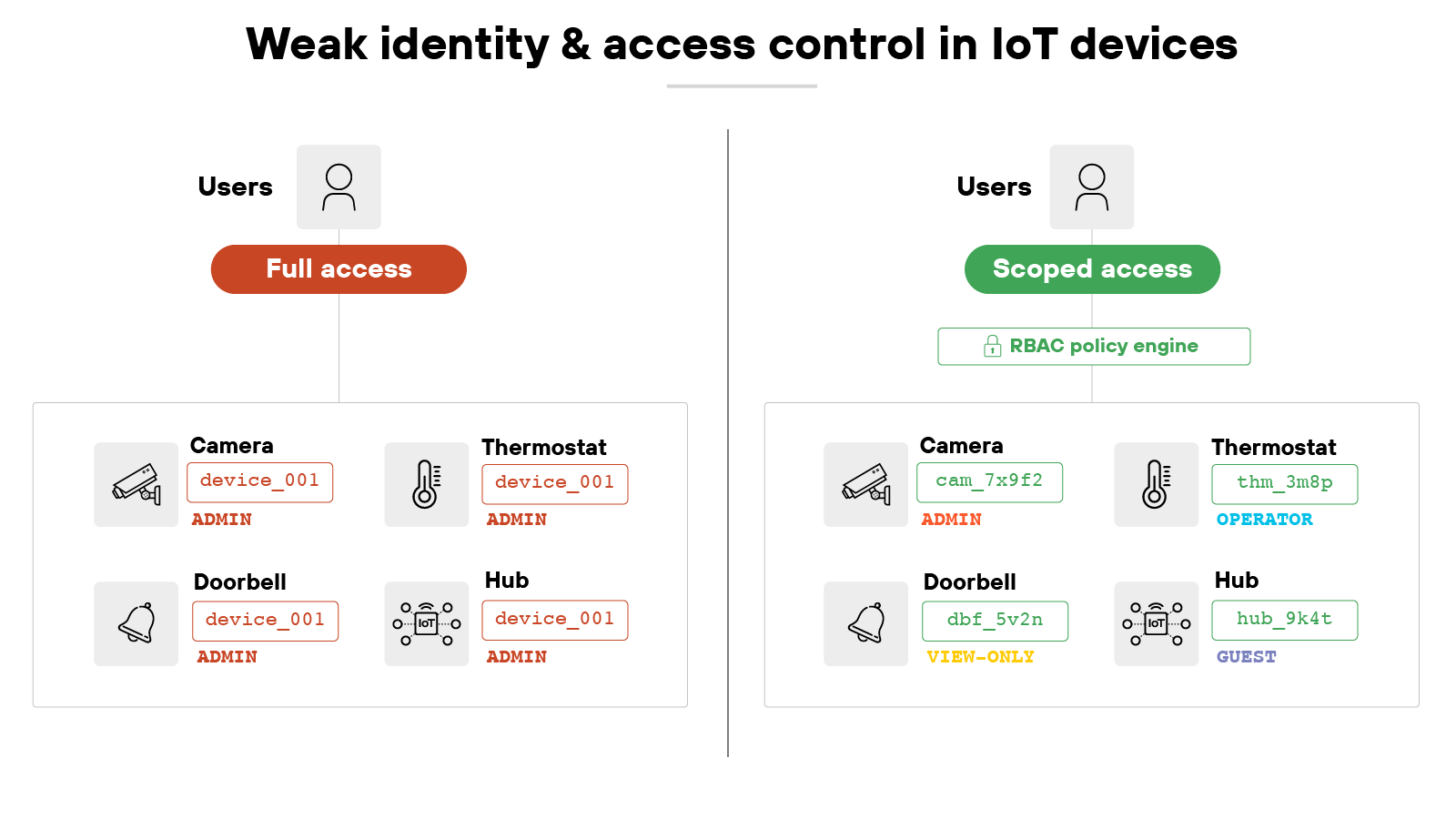
Together, these gaps create weak points in device management. An organization may struggle to know which device is which, or to limit who can alter security settings. Attackers can exploit this uncertainty to move laterally, impersonate devices, or escalate access once inside the network.
Organizations should deploy devices that support unique, immutable identifiers and integrate with centralized inventory systems. Access controls should be granular, with clear separation of administrative and operational roles. Network and identity management policies should ensure that only authorized entities can modify device configurations. And where devices lack these capabilities, network segmentation and compensating controls can help contain the risk.
5. Limited visibility and monitoring
Most IoT devices are deployed with little to no built-in monitoring. They may not generate logs. They may not support telemetry that gives operators insight into performance or security status. Without those data points, organizations are left blind to what's happening on their own networks.
Here's why that's important.
Because detection depends on visibility. If a device is compromised, but nothing records abnormal behavior, the compromise may go unnoticed. That gap delays response and makes it easier for attackers to persist.
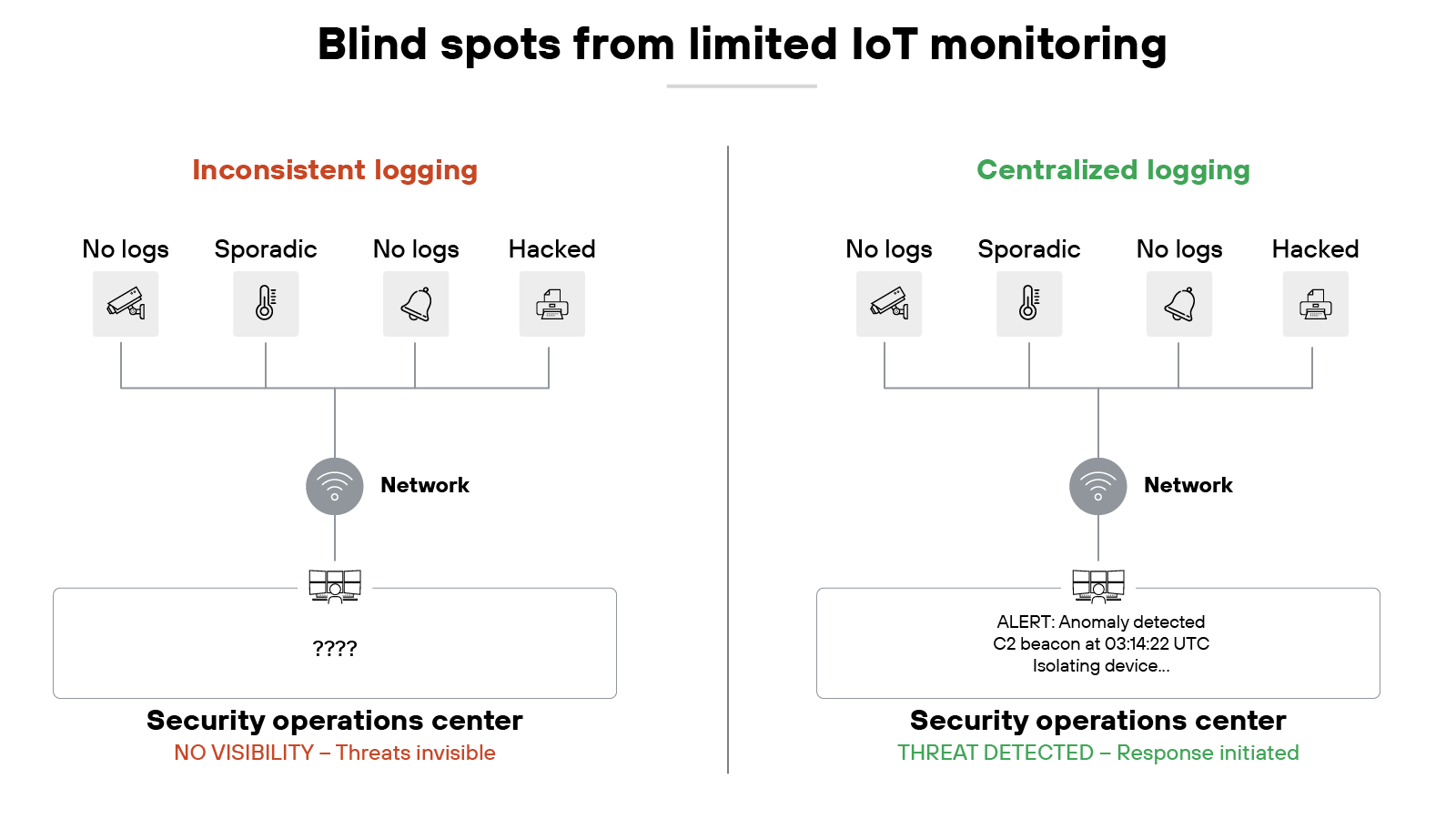
The problem grows with scale. Thousands of devices across different locations make it difficult to centralize oversight. Even when some logs exist, they may use inconsistent formats or be inaccessible without specialized tools. The effect is: organizations struggle to collect, normalize, and act on the information in time.
Organizations should prioritize devices that provide robust logging, telemetry, and integration with centralized monitoring systems. Data should be standardized and accessible through secure interfaces for aggregation. Where devices lack native capabilities, external monitoring—such as network-level anomaly detection or gateway-based logging—can help fill the gap. The goal is simple: ensure that every device leaves a trace that can be tracked, analyzed, and acted upon.
6. Supply chain and component integrity challenges
IoT devices rarely come from a single source. Hardware, firmware, and software components are often assembled from multiple vendors. Each link in that chain can introduce weaknesses. For example, insecure firmware or unverified third-party libraries can create entry points before the device is even deployed.
Manufacturing adds another layer of uncertainty. Components may be produced in facilities that lack strict oversight. So malicious modifications or counterfeit parts can slip into the supply chain. These changes are often invisible until after devices are already in use.
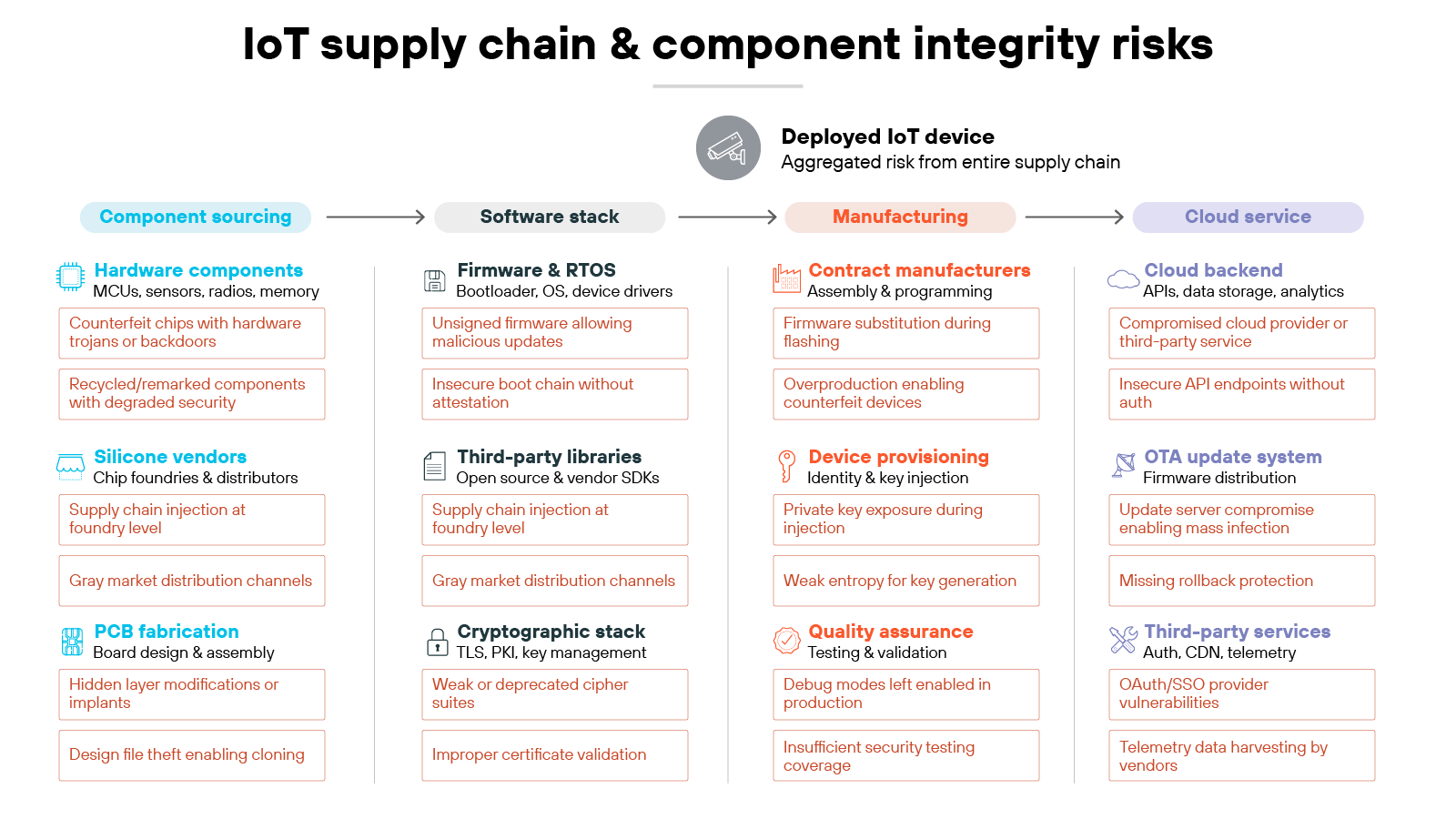
Even when the device itself is sound, the ecosystem around it may not be. Cloud services that manage updates, third-party drivers, or companion applications can all introduce dependencies outside the direct control of the organization. If any of those pieces are compromised, the security of the entire device suffers.
Organizations should evaluate supply chain integrity as part of procurement. That includes requiring vendors to document component sources, security practices, and update processes. Where possible, independent testing and certification can validate device integrity before deployment. And once in operation, organizations should monitor for unusual behavior that might indicate tampering at the component level.
7. Physical exposure and tampering risks
Many IoT devices operate in places where they can't be physically secured. Think of smart meters on the side of a building, sensors in a factory, or cameras in public areas. These devices are often accessible to anyone who walks by. And that means tampering is a realistic concern.
Physical access can expose internal components. Attackers may connect directly to debug ports, extract firmware, or reset devices to bypass safeguards. Even simple actions—like pressing a hidden reset button—can return a device to its default, insecure state.
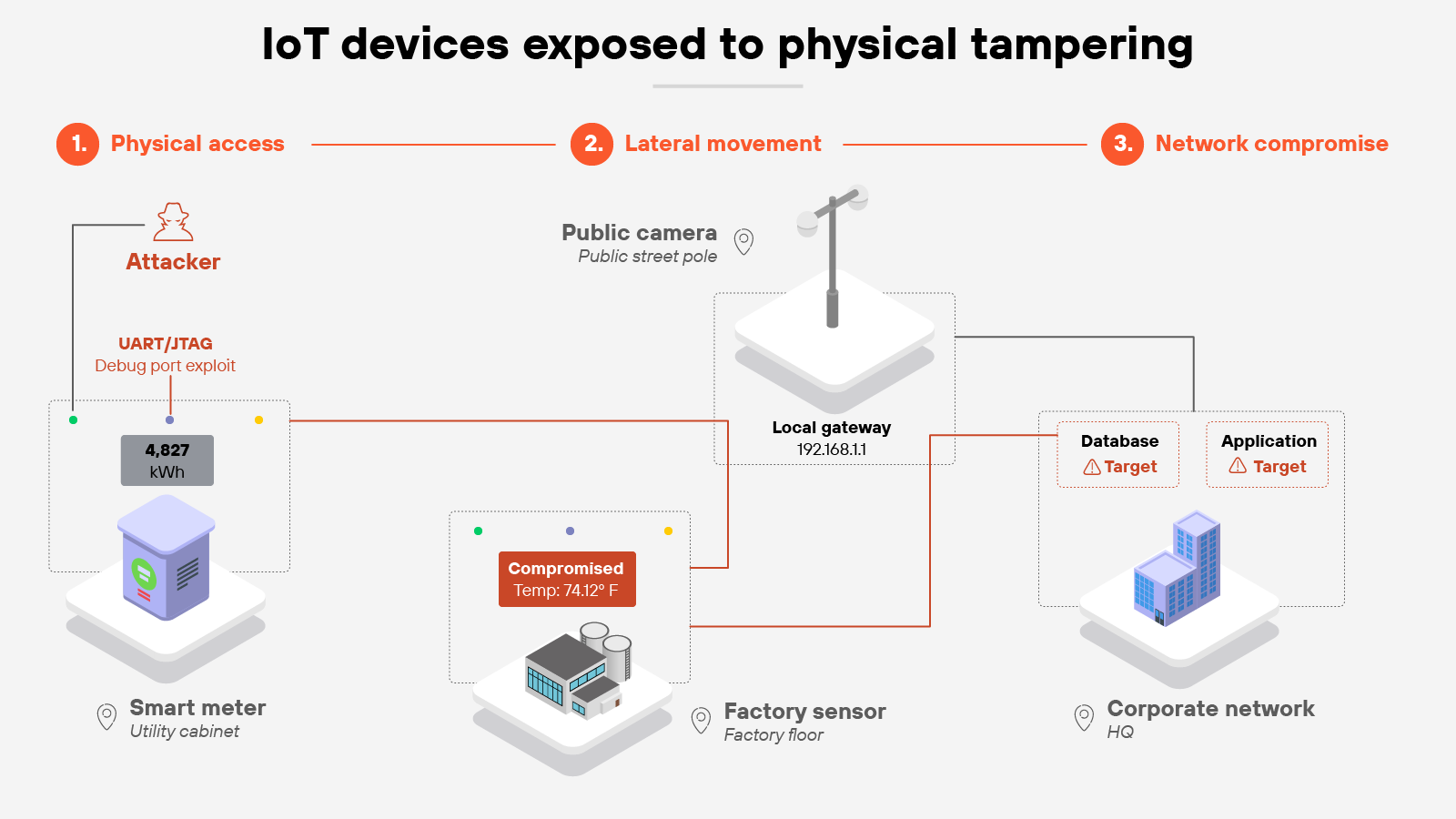
The challenge grows when devices are deployed at scale. An organization may have thousands of units spread across cities or facilities. Monitoring all of them for tampering is difficult, and a single compromised unit can be used to probe the wider network.
Organizations should evaluate the physical security of IoT devices before deployment. That can include tamper-resistant enclosures, disabled debug interfaces, and clear policies for handling resets or repairs. Where exposure cannot be avoided, compensating measures like network segmentation and monitoring for unexpected device behavior can help reduce the impact of physical compromise.
8. Data privacy and protection concerns
IoT devices collect large volumes of data. Some of it is personal, like health metrics or location information. Some of it is operational, like equipment status or environmental readings. Either way, if that data isn't properly safeguarded, it becomes a liability.
Why? Because many IoT devices transmit or store data without strong protections. Information may be sent in plain text, logged without controls, or stored on devices with little or no encryption. The consequence is that sensitive details can be exposed to anyone with access—authorized or not.
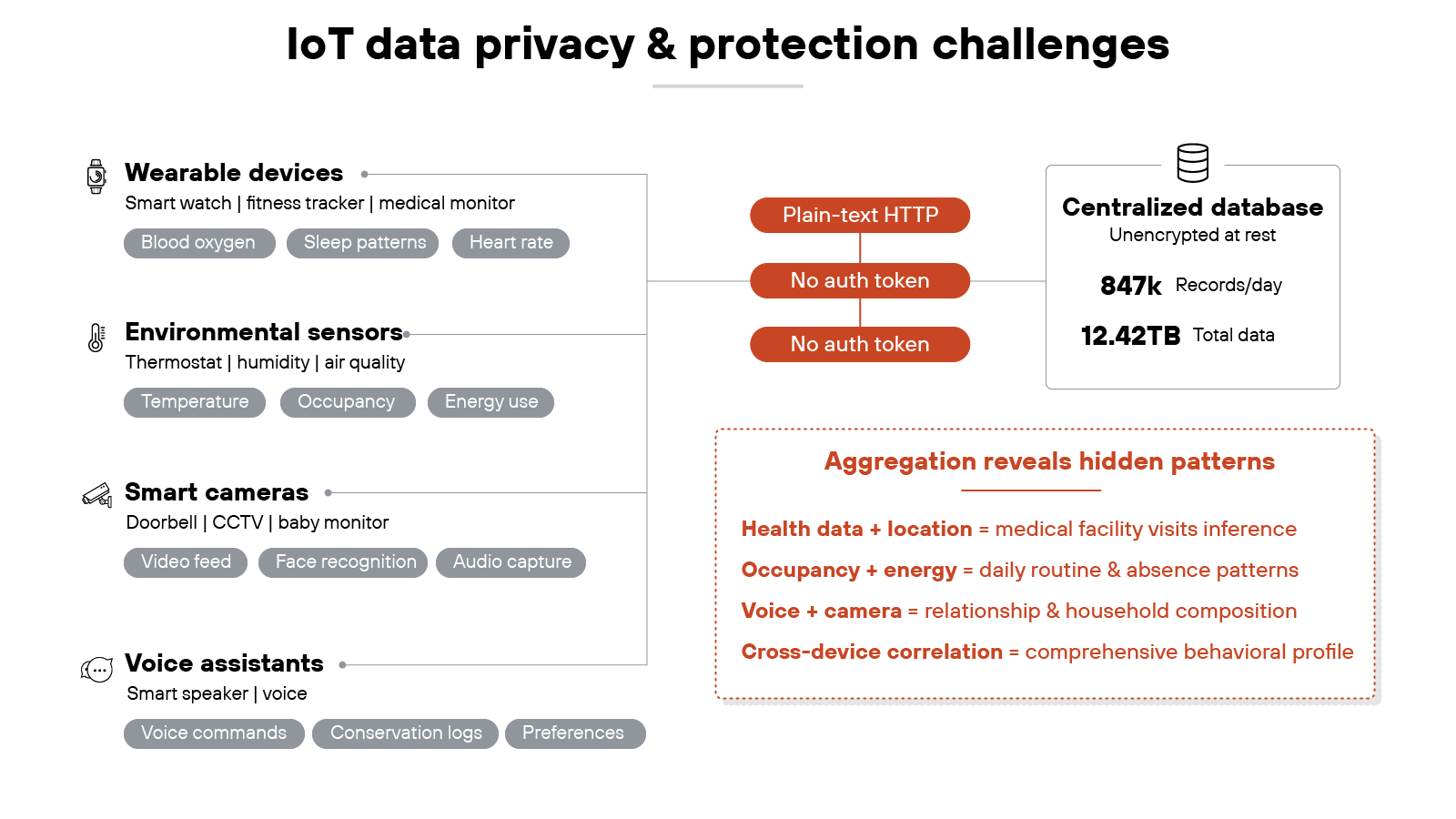
The challenge grows with data aggregation. A single device might only reveal a small piece of information. But when hundreds or thousands of devices are combined, the resulting dataset can reveal patterns, behaviors, or business intelligence that organizations didn't intend to share.
Organizations should treat IoT data as sensitive by default. That includes requiring encryption for data at rest and in transit, limiting retention to what is necessary, and enforcing strict access controls. Procurement teams should also consider whether vendors provide clear data handling policies. And where privacy can't be guaranteed by the device itself, external safeguards like secure gateways or anonymization can help protect the information collected.
9. Heterogeneity and interoperability obstacles
The IoT ecosystem is built from devices made by thousands of vendors. Each uses its own hardware designs, software stacks, and communication protocols. That leads to very little consistency in how they handle security.
For instance, one vendor may support strong authentication and encryption, while another uses weak defaults. Devices may speak entirely different protocols that can't be monitored or secured in the same way. This patchwork environment makes it nearly impossible to enforce uniform policies across an entire deployment.
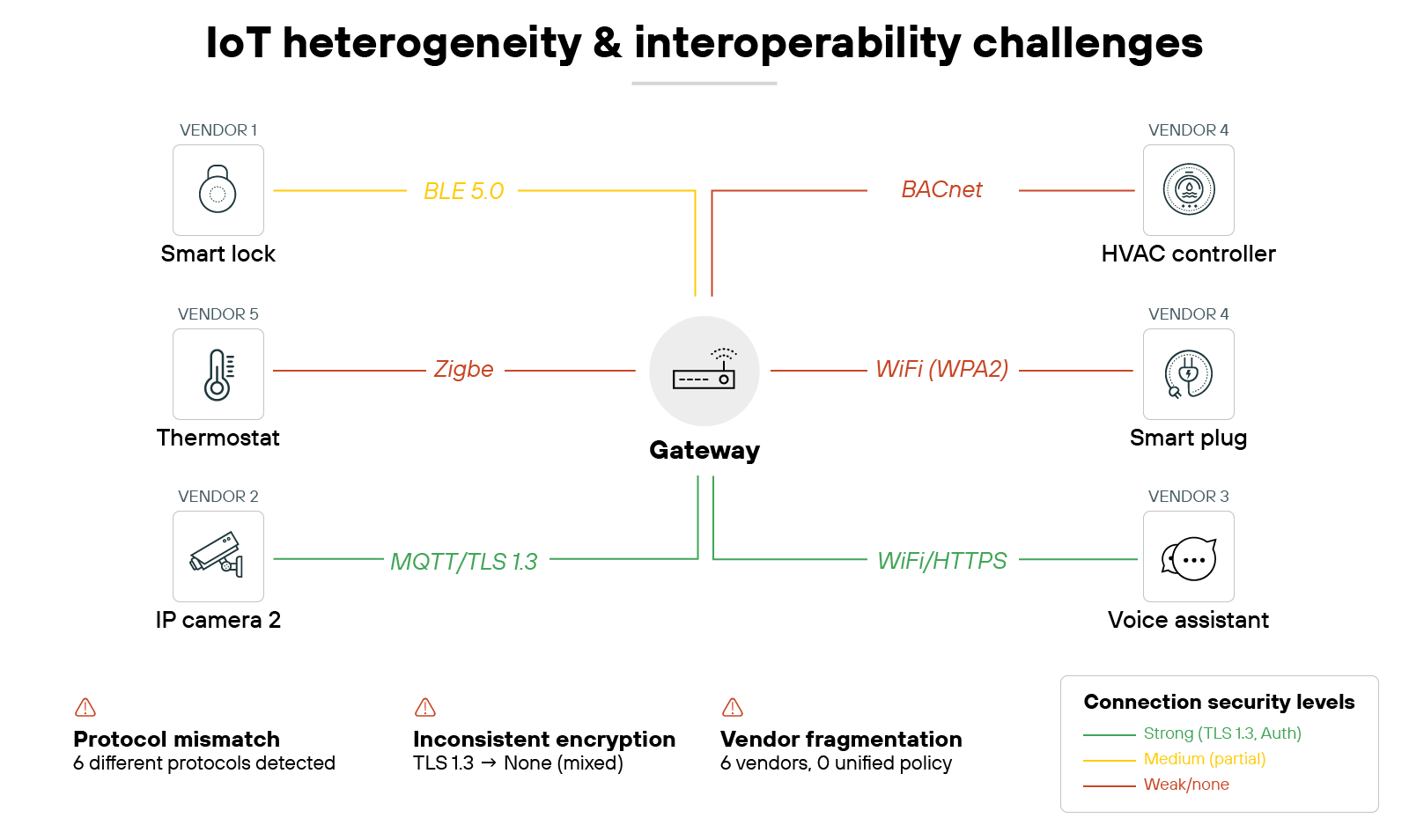
The problem doesn't stop at technical differences. Standards for IoT security exist, but adoption is uneven. Some devices are built to align with them. Others are not. Interoperability issues show up when systems need to integrate, but security features don't align. The result is inconsistent protections and more attack surfaces to manage.
Organizations should establish baseline security requirements that all IoT devices must meet before procurement. Favor vendors that adhere to recognized standards and use protocols that can integrate with centralized monitoring. Where heterogeneity cannot be avoided, compensating controls such as network segmentation and protocol gateways can help unify oversight and reduce exposure.
10. Large, distributed attack surface
IoT deployments can involve thousands—or even millions—of devices. Each one connects to a network. Each one becomes a potential entry point. Which means the attack surface expands dramatically as more devices come online.
The challenge isn't just the number of devices. It's also where they're located. Devices may sit in homes, factories, offices, or public spaces. Many operate outside the traditional security perimeter, which makes consistent protection harder to achieve.
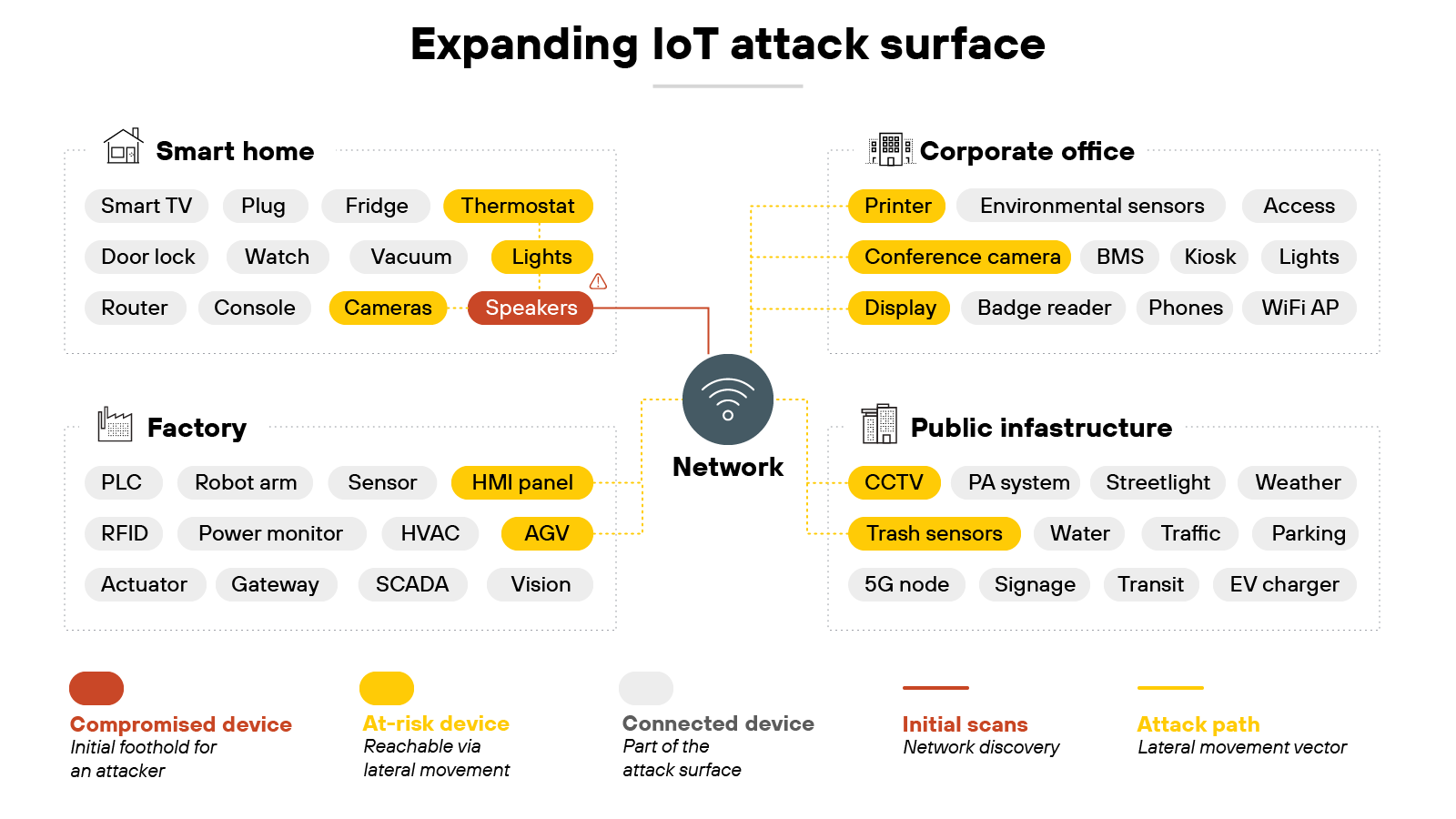
Managing this sprawl requires visibility, patching, and enforcement at scale. But the diversity of hardware and protocols makes that difficult. An attacker only needs to compromise one weak device to gain a foothold. From there, they can pivot across the environment.
Organizations should assume that IoT increases their attack surface by design. The practical response is layered defense. That means network segmentation, strong authentication, and centralized monitoring to reduce exposure. Regular audits can help identify weak points, while procurement policies can limit the addition of insecure devices. The goal is not to shrink the surface, but to make it harder to exploit.