-
What Is Endpoint Protection for Enterprises?
- Why Endpoint Protection Is Essential
- How Endpoint Protection Operates
- The Evolution of Endpoint Protection
- Defining Endpoint Protection Platform
- How Endpoint Protection Differs From Endpoint Detection and Response (EDR)
- Threats Endpoint Protection Defends Against
- Components of Endpoint Protection
- Endpoint Protection Use Cases
- What to Look for in an Endpoint Protection Platform
- Endpoint Protection FAQs
- What are Endpoint Security Management Challenges?
- What Is the Impact of Endpoint Security on System Performance?
- What are the Requirements for Securing Endpoints?
- What is the Role of AI in Endpoint Security?
- 3 Ways to Prevent Evasive Threats
- Why Endpoints Shouldn't Rely Entirely On Scanning?
- How Do I Measure Endpoint Security Effectiveness?
-
Extending Zero Trust To The Endpoint
- 5 Ways Endpoint Security and Network Security Work Together
What Is Endpoint Scanning?
Endpoint scanning is a critical cybersecurity process designed to identify vulnerabilities, misconfigurations, and malicious activities across all network-connected devices. This includes a wide array of endpoints such as:
- Laptops
- Desktops
- Servers
- Mobile devices
- IoT devices
- Virtual machines
By continuously assessing an endpoint's security posture, scanning proactively detects security risks and ensures compliance with organizational and regulatory mandates.
Key Points
-
Proactive Security
Identifies device vulnerabilities and misconfigurations before they can be exploited, significantly reducing an organization's attack surface. -
Comprehensive Assessment
Encompasses endpoint discovery, vulnerability assessments, policy compliance, and threat detection, leveraging both agent-based and agentless methods for a holistic view. -
Tailored Methodologies
Employs various scan types—vulnerability, malware, configuration baseline, data loss prevention (DLP), and compliance scans—each addressing specific security objectives. -
Adaptability
Overcomes challenges like performance impact and zero-day exploits through integration with advanced solutions like EDR and XDR, enhancing protective capabilities. -
Continuous Optimization
Requires regular automation, diligent prioritization of findings, integration with other security tools, and ongoing adaptation to the evolving threat landscape for sustained effectiveness.
Endpoint Scanning Explained
Endpoint scanning is a fundamental component of an effective cybersecurity strategy, moving beyond a simple point-in-time check to encompass a proactive and continuous assessment of an organization's digital perimeter. It involves a systematic examination of every endpoint connected to the network, from employee workstations and mobile devices to servers, IoT devices, and virtual machines.
This comprehensive analysis aims to:
- Identify potential software and system vulnerabilities.
- Detect existing malware, anomalies, or indicators of compromise (IoCs).
- Ensure compliance with internal security policies and external regulatory frameworks.
The significance of endpoint scanning in modern cybersecurity cannot be overstated. Endpoints frequently serve as initial entry points for cyber threats, often targeted through vectors like phishing, drive-by downloads, or unpatched software vulnerabilities. By regularly scanning these devices, organizations can uncover:
- Misconfigured settings (e.g., open ports, weak administrative credentials)
- Unpatched or end-of-life software
- Weak credentials or unauthorized software installations
These are all common avenues adversaries leverage for initial access or lateral movement within a network. This proactive approach helps security teams gain a comprehensive understanding of their attack surface, prioritize remediation efforts based on risk, and significantly reduce the likelihood and impact of a breach.
Ultimately, endpoint scanning acts as an essential defensive layer, fortifying the entire enterprise against evolving cyber threats and ensuring the integrity of critical data and systems.
Real-World Scenario: Preventing a Supply Chain Attack
Consider a manufacturing firm that recently integrated a new IoT sensor network into its production line. An initial security audit revealed several unpatched legacy operating systems on a segment of these sensors, which, while isolated, still communicated with the broader network.
Without regular endpoint scanning, these vulnerabilities might have gone unnoticed, creating a critical blind spot. A diligent security team, however, implemented a comprehensive endpoint scanning program. Their weekly vulnerability scans flagged these specific IoT devices as high-risk due to known CVEs associated with their outdated OS versions.
This allowed the team to:
- Isolate Affected Devices: Temporarily segment the vulnerable IoT network.
- Prioritize Patching: Expedite the application of security patches, or implement compensating controls where patching wasn't immediately feasible.
- Validate Remediation: Subsequent scans confirmed the vulnerabilities were successfully addressed.
Just weeks later, a well-publicized supply chain attack vector emerged, specifically targeting these types of unpatched legacy IoT devices for initial network infiltration.
Because the manufacturing firm had proactively leveraged endpoint scanning, they were already protected, averting a potentially catastrophic disruption to their operations and data integrity. This scenario underscores how continuous endpoint scanning transforms theoretical risks into actionable intelligence, demonstrably enhancing an organization's resilience.
Why Endpoint Scanning Is Crucial for Modern Cybersecurity
Endpoint scanning forms the bedrock of an organization's defense against a constantly evolving threat landscape, directly addressing fundamental vulnerabilities inherent in diverse digital environments. By proactively assessing devices, enterprises significantly reduce their exposure to cyber attacks.
Mitigating the Expanding Attack Surface
The proliferation of devices—laptops, smartphones, IoT gadgets, and cloud instances—creates a vast and complex attack surface. Each new endpoint introduces a potential entry point for attackers seeking to breach an organization's network.
Endpoint scanning systematically inspects these diverse devices, identifying weak points that could otherwise remain unnoticed. This effectively shrinks the exploitable surface for malicious actors, moving beyond perimeter-centric defenses to granular endpoint protection.
Proactive Threat Detection and Prevention
Traditional security measures often react to threats after they have manifested. Endpoint scanning, conversely, focuses on uncovering vulnerabilities and misconfigurations before they can be exploited.
This preemptive approach enables security teams to patch systems, update software, and adjust settings before an attacker can exploit them for initial access or to spread malware. It shifts the defense from reactive incident response to preventive security posture management.
Ensuring Regulatory Compliance and Data Governance
Many industry regulations and data protection laws mandate stringent security controls for sensitive information. Endpoint scanning plays a vital role in demonstrating compliance with these standards, such as GDPR, HIPAA, or PCI DSS. It helps organizations maintain an auditable record of their security posture by regularly checking for adherence to established policies and configurations. This ensures data governance requirements are met and helps avoid costly penalties associated with non-compliance.
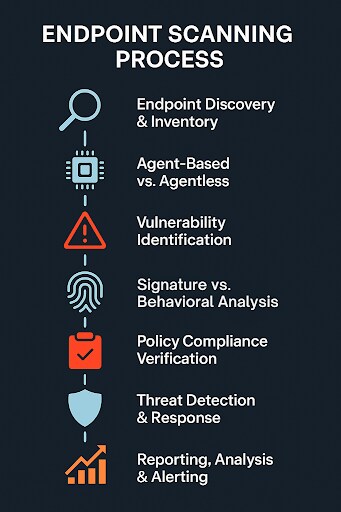
How Endpoint Scanning Works: A Multi-Faceted Process
Before any analysis can occur, the scanning process must first identify all active devices connected to the network. This discovery phase creates a comprehensive inventory of every endpoint, ensuring no device remains unmonitored.
It often leverages network protocols like ARP, ICMP, SNMP, or NMAP scans to identify IP addresses and open ports, providing a foundational view of the organization's digital assets. An accurate and continuously updated asset inventory is crucial; without it, some endpoints may be missed, resulting in significant security gaps.
Agent-Based vs. Agentless Scanning
Endpoint discovery and subsequent scanning can be performed using two primary methodologies:
- Agent-based scanning involves installing a small software client, or "agent," directly onto each endpoint. This agent collects detailed local data—such as installed software, running processes, system configurations, and patch levels—and communicates it back to a central server for analysis. This method provides deep visibility, continuous real-time monitoring, and often enables local remediation actions.
- Agentless scanning leverages existing network protocols and remote access capabilities to inspect devices without requiring software installation on the endpoint itself. Common protocols used include Windows Management Instrumentation (WMI) for Windows systems, SSH for Linux/Unix, or PowerShell remoting. While easier to deploy across diverse systems without endpoint disruption, agentless methods may offer less granular control or real-time insight compared to agent-based approaches.
Each approach has distinct advantages in terms of deployment, network impact, and data collection granularity. Hybrid approaches, combining both methods, are also common for comprehensive coverage.
Vulnerability Identification and Assessment
Once endpoints are identified, the core of the scanning process begins—identifying security weaknesses. This involves systematically checking for known vulnerabilities in operating systems, applications, and network services.
The scanner compares current software versions, patch levels, and configurations against extensive, frequently updated databases of publicly disclosed flaws, such as the Common Vulnerabilities and Exposures (CVE) database and vendor advisories. This process highlights potential entry points for attackers, informing proactive patching and risk reduction strategies.
Signature-Based vs. Behavioral Analysis
Vulnerability and threat detection within endpoint scanning often employs a combination of techniques.
- Signature-based Analysis: Relies on databases of known malware signatures, vulnerability patterns, and IoCs. It quickly identifies previously documented threats by matching unique digital fingerprints. While efficient for known threats, it's less effective against novel attacks.
- Behavioral Analysis: Monitors endpoint activities for suspicious patterns or deviations from normal behavior. This includes observing process execution, file system changes, network connections, and API calls. By establishing a baseline of "normal," behavioral analysis, often powered by machine learning (ML) algorithms, can detect new or unknown threats, including sophisticated zero-day exploits, even without a predefined signature.
Policy Compliance Verification
Beyond technical vulnerabilities, endpoint scanning also assesses adherence to an organization’s internal security policies and external regulatory mandates. This includes verifying the presence of required software installations, checking for disabled features, ensuring proper password policies are enforced, and configuring firewalls for optimal security. It ensures that every endpoint aligns with the defined security baseline, which is crucial for maintaining a consistent and strong security posture.
Threat Detection and Response Capabilities
Modern endpoint scanning extends beyond mere identification; it incorporates mechanisms for detecting active threats. This includes identifying:
- Malware infections
- Unauthorized processes
- Unusual network connections
- Attempted privilege escalations
Upon detection, some advanced scanners or integrated EDR/XDR solutions can initiate automated response actions, such as isolating affected devices from the network, terminating malicious processes, or quarantining suspicious files to contain the threat and prevent its spread.
Reporting, Analysis, and Alerting
The final phase involves consolidating all collected data into actionable reports. These reports highlight:
- Identified vulnerabilities (often categorized by severity and exploitability)
- Compliance deviations
- Detected threats and indicators of compromise
Security teams receive alerts for critical findings, enabling them to prioritize remediation efforts using risk-based approaches and respond swiftly to emerging risks. Continuous analysis of these reports also helps refine security strategies over time, identify trends, and measure the effectiveness of security controls.
Types of Endpoint Scans
Different scenarios and security objectives necessitate various approaches to endpoint scanning. Understanding the distinct types of scans available allows organizations to precisely tailor their security strategies, ensuring each aspect of an endpoint's security posture is adequately addressed.
| Scan Type | Purpose/Focus |
|---|---|
| Vulnerability Scans | Identifies known security weaknesses in operating systems, applications, and configurations by comparing them against vulnerability databases. |
| Malware and Threat Scans | Detects malicious software, including viruses, worms, and ransomware, using signature-based, heuristic, and behavioral analysis. |
| Configuration Baseline Scans | Assesses adherence to predefined internal security policies and configurations, ensuring consistent security posture across endpoints. |
| Data Loss Prevention (DLP) Scans | Identifies and monitors sensitive data on endpoints to prevent unauthorized exfiltration and ensure compliance with data governance. |
| Compliance Scans | Evaluates an endpoint's adherence to specific regulatory standards and industry mandates, providing auditable proof of compliance. |
Vulnerability Scans
Vulnerability scans systematically identify known security weaknesses in operating systems, applications, and network configurations present on an endpoint. These scans leverage continually updated databases, such as the Common Vulnerabilities and Exposures (CVE) list and vendor-specific advisories, to compare the device's software versions and patch levels against documented flaws.
They highlight potential entry points that attackers could exploit, making them crucial for proactive patching, prioritizing remediation efforts, and significantly reducing an organization's overall risk exposure.
Malware and Threat Scans
Malware and threat scans specifically look for malicious software residing on an endpoint. This includes a wide range of threats such as viruses, worms, Trojans, ransomware, and spyware. These scans employ a combination of techniques:
- Signature-based detection: Matches file hashes or code patterns against a database of known malware signatures.
- Heuristics: Analyzes suspicious file characteristics or behaviors (e.g., attempts to modify system files) that might indicate new or polymorphic malware.
- Behavioral analysis: Monitors real-time process activity for malicious patterns.
These capabilities are essential for both preventing new infections and remediating active compromises by identifying and often quarantining or removing detected threats.
Configuration Baseline Scans
Configuration baseline scans verify whether an endpoint adheres to a predefined set of security configurations and internal security policies. This includes checking for compliance with:
- Mandated password complexity rules.
- Enabled security features like firewalls and anti-malware software.
- Disabled unnecessary services or open ports.
- Proper access controls and administrative privileges.
Deviations from the established baseline indicate potential security gaps or policy violations. These scans are critical for maintaining a consistent, hardened operating environment across the entire endpoint fleet, preventing configuration drift that can expose systems to risk.
They often align with security frameworks like the Center for Internet Security (CIS) Benchmarks or Security Content Automation Protocol (SCAP).
Data Loss Prevention (DLP) Scans
DLP scans focus on identifying and monitoring sensitive data—such as personally identifiable information (PII), financial records, intellectual property, or classified documents—stored or transmitted on endpoints.
These scans employ techniques such as regular expressions (regex), keyword matching, and document fingerprinting to identify patterns indicative of confidential information. Their primary purpose is to prevent unauthorized exfiltration of sensitive data, enforce data governance policies, and ensure compliance with privacy regulations such as GDPR or CCPA, thereby protecting critical business assets from insider threats and accidental disclosures.
Compliance Scans
Compliance scans are specifically designed to evaluate an endpoint's adherence to a range of external regulatory standards and industry mandates, such as HIPAA (for healthcare), PCI DSS (for payment card industry), NIST SP 800-53 (for federal agencies), or ISO 27001.
These scans verify that security controls, configurations, and data handling practices meet the precise requirements set by these frameworks. They are vital for organizations operating in regulated industries, providing objective, auditable proof of compliance to auditors and preventing costly penalties associated with non-compliance.
Key Steps for Effective Endpoint Scanning
Implementing an effective endpoint scanning program requires a structured approach that moves beyond mere tool deployment. Each step builds upon the last, ensuring comprehensive coverage and actionable insights. Following these key stages helps organizations maximize the benefits derived from their scanning efforts.
1. Planning and Scope Definition
The initial phase involves clearly defining the objectives of the scanning initiative and identifying the scope of devices to be included. This entails understanding which endpoints are critical, the types of data they handle, and the applicable internal policies or external regulatory requirements.
A well-defined plan ensures scanning efforts are targeted, efficient, and aligned with overall organizational risk management strategies.
2. Endpoint Discovery and Asset Management
An accurate and up-to-date inventory of all network-connected endpoints is crucial. This step involves continuously discovering new devices (e.g., through network sweeps, integration with DHCP/DNS, or CMDBs) and maintaining a comprehensive, often automated, database of assets.
Without a continuous and comprehensive understanding of all assets, "shadow IT" or unmanaged endpoints can easily be missed during scanning, resulting in significant and exploitable security gaps.
3. Implementing Scanning Methodologies
Organizations must select and deploy appropriate scanning methodologies, including agent-based, agentless, or hybrid approaches, based on their environment and specific security requirements. This involves:
- Configuring scanning tools: Defining scan profiles, targets, and credentials for authenticated scans (which yield far more granular results than unauthenticated scans).
- Establishing scan schedules: Balancing thoroughness with operational impact, often leveraging staggered or incremental scans.
- Integrating with existing infrastructure: Ensuring the scanning solution can communicate effectively with endpoints and central management platforms.
Proper implementation ensures scans are thorough, minimally disruptive to operations, and provide accurate data.
4. Analyzing and Prioritizing Findings
Raw scan data, which can be voluminous, must be meticulously analyzed to identify actual vulnerabilities, misconfigurations, and threats. This step includes:
- Correlating findings: Cross-referencing data from multiple sources to gain a holistic view.
- Eliminating false positives: Distinguishing legitimate activities or benign configurations from true security risks.
- Assessing severity and potential impact: Utilizing frameworks like CVSS (Common Vulnerability Scoring System) to objectively rate risks.
Prioritization ensures that the most critical issues, those with high severity and exploitability on critical assets, are addressed first, optimizing remediation resource allocation.
5. Remediation and Mitigation Strategies
Once risks are prioritized, security teams must develop and execute strategies to remediate or mitigate them. This often involves:
- Applying patches and updates: Addressing known software vulnerabilities.
- Correcting misconfigurations: Hardening system settings to align with security baselines.
- Removing unauthorized software: Eliminating potential attack vectors.
- Isolating compromised devices: Containing active threats to prevent lateral movement.
A systematic approach to remediation closes identified security gaps, directly reducing the attack surface.
6. Continuous Monitoring and Validation
Endpoint scanning is not a one-time activity but an ongoing process. Continuous monitoring ensures that security postures remain strong as new threats emerge and the environment changes.
Regular re-scans and validation of fixes confirm that remediation efforts were successful and no new vulnerabilities have been introduced. This iterative process, often integrated into a Security Operations Center (SOC) workflow, is vital for maintaining an adaptive and resilient security defense, continuously tuning policies and scanning parameters based on the latest threat intelligence.
Challenges and Limitations in Endpoint Scanning
While endpoint scanning offers significant security benefits, its implementation and effectiveness are not without obstacles. Organizations must be aware of these challenges to develop more comprehensive and realistic cybersecurity strategies. Addressing these limitations often requires a multi-layered security approach that complements scanning.
Performance Impact on Endpoints
Intensive scanning processes, particularly full system scans or deep vulnerability scans, can consume significant CPU and memory resources on endpoints. This can lead to noticeable performance degradation for users, especially on older hardware or devices already under heavy load.
Striking a balance between scan thoroughness, frequency, and operational impact is a constant consideration for IT and security teams, often mitigated through scheduled off-peak scans or incremental scanning.
Evolving Threat Landscape and Zero-Day Exploits
The speed at which new threats emerge—especially sophisticated zero-day exploits—poses a significant challenge to traditional signature-based scanning. Such attacks exploit previously unknown vulnerabilities for which no patch or detection signature yet exists. This means they can bypass detection by scanners relying solely on known patterns.
While behavioral analysis helps, the continuous innovation by adversaries requires security solutions to adapt and integrate new detection methodologies continually.
Managing False Positives and Negatives
Endpoint scanning tools can sometimes generate a high volume of alerts, some of which may be false positives—identifying legitimate activity or benign configurations as malicious. Conversely, false negatives occur when an actual threat goes undetected.
Both scenarios can lead to alert fatigue among security analysts, wasted resources investigating non-issues, or, more dangerously, missed critical threats. Accurate tuning of scan policies, context-aware analysis, and continuous refinement of detection logic are necessary to minimize these occurrences.
Scalability Across Diverse Environments
Modern enterprise networks typically comprise thousands of diverse endpoints, encompassing various operating systems (Windows, macOS, Linux, mobile OS), device types, and network locations (on-premise, remote, cloud-based). Scaling endpoint scanning solutions to cover this vast and heterogeneous environment effectively can be complex.
Ensuring consistent coverage, managing agent deployment (if applicable), and consolidating data from such a wide array of devices presents a significant logistical and architectural challenge.
Reliance on Signature Databases
While essential for detecting known threats, a primary limitation of many traditional scanning methods is their reliance on signature databases. If these databases are not updated frequently, or if a new threat emerges for which no signature exists (e.g., polymorphic malware, fileless attacks), the scanner will be unable to identify it. This inherent reactive nature underscores the need for complementary security tools that employ advanced analytics beyond simple signature matching.
Enhancing Endpoint Scanning with Advanced Technologies
To overcome the inherent limitations of traditional methods, modern endpoint scanning is increasingly integrated with and augmented by advanced security technologies. These innovations provide deeper visibility, faster detection, and more intelligent response capabilities. They transform scanning from a periodic check into a dynamic defense mechanism.
Integration with Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions continuously monitor all endpoint activity, capturing granular telemetry such as process execution, file system changes, network connections, and user actions.
When integrated with endpoint scanning, EDR enriches scan findings with real-time behavioral context, allowing for:
- More Accurate Threat Hunting: Security analysts can correlate scan-identified vulnerabilities with active suspicious behaviors observed by EDR.
- Faster Incident Response: EDR's continuous monitoring allows for immediate detection of post-exploitation activities that traditional scans might miss, enabling rapid containment and remediation.
This combination moves beyond simple vulnerability identification to active threat management, providing a comprehensive understanding of an endpoint's security state at any given moment.
Leveraging Extended Detection and Response (XDR)
Extended Detection and Response (XDR) builds upon EDR by correlating security data across multiple domains, including endpoints, networks, cloud environments, identity providers, and email.
For endpoint scanning, XDR provides a significantly broader threat context, enabling the identification of sophisticated attacks that span multiple control points and might otherwise appear as isolated alerts. This unified visibility allows for:
- Holistic Attack Storyline: Tracing attack chains from initial compromise on an endpoint through lateral movement across the network or into cloud resources.
- Automated Cross-Domain Response: Orchestrating automated responses that can isolate an affected endpoint while simultaneously blocking malicious network traffic or revoking compromised user credentials.
XDR consolidates disparate security alerts, offering a clearer, more actionable view of complex threats.
Artificial Intelligence and Machine Learning in Scanning
Artificial intelligence (AI) and machine learning (ML) capabilities are revolutionizing endpoint scanning. These technologies analyze vast datasets of endpoint telemetry, threat intelligence, and historical attack patterns to:
- Identify Anomalous Behaviors: Detect deviations from baselines that indicate new or unknown threats (e.g., polymorphic malware, fileless attacks) which would elude signature-based detection.
- Improve Classification Accuracy: Reduce false positives by intelligently discerning malicious activity from legitimate system processes.
- Enable Predictive Analytics: In some advanced systems, AI can analyze trends to forecast potential attack vectors and anticipate new threats before they materialize, moving security from reactive detection to proactive prediction.
AI/ML empowers scanners to learn and adapt to new attack techniques, significantly enhancing the accuracy and speed of threat identification.
Cloud-Native Endpoint Security
The shift to cloud environments and distributed workforces has driven the evolution of cloud native endpoint security solutions. These solutions leverage the scalability, elasticity, and global reach of cloud infrastructure to deliver scanning capabilities without traditional on-premise overhead of managing physical servers. Cloud-native approaches offer:
- Continuous, Real-Time Monitoring: Consistent visibility across all endpoints, regardless of their physical location or network connection.
- Simplified Management: Centralized control and automated updates for distributed workforces and cloud-based assets.
- Reduced Infrastructure Costs: Eliminating the need for dedicated hardware and its associated maintenance.
This ensures a consistent and robust security posture, regardless of the endpoint's location or operating environment.
Best Practices for Optimizing Endpoint Scanning
Achieving maximum efficacy from endpoint scanning requires adherence to a set of strategic best practices. These guidelines ensure that scanning initiatives are not only thorough but also integrated, efficient, and responsive to evolving threats. Implementing them transforms scanning into a proactive and adaptive security discipline.
Regularity and Automation
Consistent and automated scanning is paramount. Scheduling regular scans—daily, weekly, or monthly, depending on asset criticality, compliance requirements, and the rate of environmental change—ensures continuous monitoring for new vulnerabilities and threats.
Automation, through scripting or integrated security orchestration, automation, and response (SOAR) platforms, reduces manual effort, minimizes the window of opportunity for attackers by ensuring no endpoint goes unchecked, and improves the efficiency of security operations.
Prioritization of Vulnerabilities
Not all vulnerabilities pose the same level of risk. Effective endpoint scanning programs prioritize remediation efforts based on a clear risk assessment model that considers:
- Severity: The inherent impact of the vulnerability (e.g., critical, high, medium, low, often using CVSS scores).
- Exploitability: How easily the vulnerability can be leveraged by an attacker.
- Asset Criticality: The business importance of the affected endpoint and the data it processes.
This allows security teams to focus resources where they will have the most significant impact on reducing organizational risk, rather than chasing every identified flaw equally.
Integration with Broader Security Tools
Endpoint scanning should not operate in isolation. Integrating scanning solutions with other security tools creates a unified security ecosystem, enhancing overall threat intelligence and streamlining workflows:
- Patch Management Systems: Automating the deployment of identified missing patches.
- Security Information and Event Management (SIEM) Platforms: Centralizing and correlating scan findings with other security logs for holistic threat detection and compliance reporting.
- Identity and Access Management (IAM) Systems: Tying endpoint security posture to user access privileges.
- Configuration Management Databases (CMDBs): Ensuring an accurate and up-to-date asset inventory for scanning targets.
This interoperability provides a holistic view of the security posture and enables more automated responses.
User Awareness and Training
While technology plays a crucial role, human factors remain a significant vulnerability. Educating users about common attack vectors, such as phishing and social engineering tactics, and the importance of secure browsing habits, can significantly reduce the risk of endpoint compromise.
Regular, mandatory security awareness training empowers users to be the first line of defense, recognizing and reporting suspicious activities that endpoint scanning might not inherently detect.
Continuous Improvement and Adaptability
The cybersecurity landscape is constantly changing, meaning endpoint scanning strategies must continuously adapt. This commitment to continuous improvement involves:
- Regularly reviewing scan results: Identifying trends and persistent issues.
- Tuning configurations: Optimizing scan policies to reduce false positives and improve accuracy.
- Updating threat intelligence feeds: Ensuring scanners are aware of the latest threats and vulnerabilities.
- Adopting new technologies: Integrating advanced solutions like EDR/XDR or AI/ML as the threat landscape evolves.
This iterative process ensures the scanning program remains effective against emerging threats and maintains alignment with evolving business needs.
Endpoint Scanning vs. Other Endpoint Security Solutions
Understanding the distinct roles of various endpoint security solutions is crucial for building a comprehensive defense against cyber threats. While endpoint scanning is a foundational element, it complements, rather than replaces, other specialized tools. Each solution contributes uniquely to the overall security posture.
Endpoint Scanning vs. Antivirus (AV)
Endpoint scanning focuses on identifying vulnerabilities, misconfigurations, and known threats across an endpoint's system and applications. It is a discovery and assessment tool.
Antivirus (AV) primarily focuses on detecting and preventing malware infections on a file-by-file or process-by-process basis, typically using signature matching. While AV is a component of endpoint protection, scanning provides a broader vulnerability assessment.
Endpoint Scanning vs. Endpoint Detection and Response (EDR)
Endpoint scanning provides a snapshot of an endpoint's security posture at a given time, primarily identifying known weaknesses. Endpoint Detection and Response (EDR), conversely, offers continuous, real-time monitoring of endpoint activity to detect suspicious behaviors and active threats.
EDR provides deeper visibility into ongoing incidents and facilitates rapid response, acting as a dynamic threat hunting and incident management tool that complements proactive scanning and assessment.
Endpoint Scanning vs. Next-Generation Antivirus (NGAV)
Endpoint scanning assesses the overall security hygiene and vulnerabilities. Next-Generation Antivirus (NGAV) surpasses traditional signature-based antivirus solutions by employing advanced techniques, such as machine learning, behavioral analysis, and artificial intelligence, to predict and prevent both known and unknown threats.
NGAV is a preventative layer against sophisticated malware, whereas scanning identifies a broader range of security flaws. NGAV enhances the preventative capabilities of an endpoint, which scanning can then verify.
Future Trends in Endpoint Scanning
The trajectory of endpoint scanning is heavily influenced by advancements in artificial intelligence, cloud computing, and the increasing complexity of cyber threats. These trends suggest a future where scanning is more intelligent, pervasive, and seamlessly integrated. Anticipating these shifts is essential for preparing future security architectures and maintaining a resilient defensive posture.
AI-Driven Predictive Analytics
Future endpoint scanning will increasingly leverage AI for predictive analytics. Instead of merely identifying existing vulnerabilities, AI will analyze historical data, current behaviors, and global threat intelligence to forecast potential attack vectors and anticipate new threats before they materialize.
This advanced capability shifts security from reactive detection to proactive prediction, enabling organizations to pre-emptively strengthen their defenses against likely future attacks.
Cloud-Native and Serverless Endpoint Scanning
As enterprises continue their mass migration to hybrid and cloud environments, endpoint scanning solutions will predominantly become cloud-native and serverless.
This eliminates the need for managing on-premise infrastructure for scanning, offering elastic scalability, global reach, and continuous, real-time assessment of cloud workloads, remote endpoints, and ephemeral assets (like containers or serverless functions). This approach ensures a consistent security posture, regardless of the endpoint's dynamic location or architectural model.
Emphasis on Identity and Access Context
Future scanning will place a greater emphasis on the identity and access context of an endpoint. It will assess not only the device's technical vulnerabilities but also how its associated users' identities, permissions, and access patterns contribute to the overall risk.
This convergence with IAM data will enable more granular, context-aware security policies and risk scoring, allowing for dynamic privilege adjustments or access restrictions based on an endpoint's detected security state.
Convergence with Attack Surface Management
Endpoint scanning will increasingly converge with broader Attack Surface Management (ASM) platforms. This integration will provide a unified, external and internal view of an organization's entire digital footprint, linking endpoint vulnerabilities with other exposed assets such as web applications, network devices, cloud services, and public-facing infrastructure.
This holistic approach offers more comprehensive risk assessment, prioritization, and continuous monitoring of the entire attack surface, not just individual endpoints.
Endpoint Scanning FAQs
Okay, here are 5 new FAQs about endpoint scanning that were not explicitly covered or detailed within the main article, tailored for your audience of IT and cybersecurity professionals:
Endpoint Scanning FAQs (Supplemental)
Common pitfalls include:
- Lack of continuous scanning: Treating scanning as a one-time or infrequent event, missing newly introduced vulnerabilities.
- Ignoring critical findings: Failing to prioritize and remediate high-severity vulnerabilities promptly, leading to unaddressed risks.
- Poor asset inventory: Not having a complete and accurate list of all endpoints, resulting in "blind spots" where devices go unscanned.
- Over-reliance on automated tools: Not complementing automated scans with manual review or deeper analysis for complex issues.
- Insufficient integration: Operating scanning solutions in silos, failing to integrate findings with other security tools like SIEM or patch management systems, which hinders holistic defense and automated response.
Beyond identifying traditional vulnerabilities (e.g., missing patches, misconfigurations), advanced endpoint scanning, especially when integrated with EDR/XDR, can provide insights into:
- User behavior analytics (UBA): Anomalous user activities that might indicate compromised accounts.
- Software inventory and licensing compliance: Identifying unauthorized or unlicensed software.
- Data sprawl: Locating sensitive data stored in unapproved or insecure locations on endpoints.
- Endpoint performance metrics: Correlating security issues with potential performance impacts.
- Shadow IT discovery: Identifying devices connected to the network without IT's knowledge or approval.