-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
Dark Web Leak Sites: Key Insights for Security Decision Makers
- Dark Web Leak Sites Explained
- Evolving Extortion Tactics
- The Role of Leak Sites in Ransomware Double Extortion
- Critical Risks Exposed by Data Leak Sites
- Anatomy of a Dark Web Leak Site
- Proactive Defense: How Organizations Can Mitigate Dark Web Leaks
- Dark Web Leak Site FAQs
- What to Do If Your Organization Appears on a Dark Web Leak Site
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What Is Phishing?
Phishing is a form of social engineering that uses deception to manipulate individuals into disclosing sensitive information or executing unauthorized transactions. It remains the most pervasive initial access vector in modern cyber attacks, often serving as the entry point for credential theft, account compromise, ransomware deployment, and supply chain infiltration.
At its core, phishing relies on psychological exploitation — urgency, fear, trust, curiosity — to provoke a response. The attacker masks malicious intent beneath a façade of legitimacy, often impersonating a trusted brand or colleague or authority figure. The delivery mechanism can be email, SMS, voice call, direct message, or even a QR code. As with most financially motivated cyber attacks, the endgame includes credential harvesting, session hijacking, malware execution, and manipulation of human workflows.
Phishing Explained
Phishing is a business model, a cornerstone of the global cybercrime economy. It enables everything from low-level fraud to state-sponsored espionage. Its low barrier to entry and high return on investment make it a preferred tool among adversaries of every sophistication level.
At the lowest tiers, phishing is commoditized. Kits and turnkey services let even novice attackers launch convincing campaigns with minimal effort. At the upper echelons, it becomes surgical — executed by well-resourced operators who perform reconnaissance, craft bespoke lures, and target individuals based on access or influence. In both cases, phishing serves as the bridge between deception and intrusion.
The Lead Play in Social Engineering Maneuvers
Phishing operates as a subset of social engineering, which encompasses any tactic that manipulates human behavior to bypass security. Pretexting, baiting, quid pro quo attacks all fall under the umbrella of social engineering. Because phishing scales — not only automating deception but also adapting to new communications mediums — it accounts for most socially engineered attacks.
Unlike traditional social engineering, which might require direct interaction and high investment per target, phishing can simultaneously hit thousands — or pivot to a one-on-one format. It retains the psychological manipulations central to social engineering but amplifies reach through technology. In that way, phishing merges the human layer with the digital attack surface, making it uniquely dangerous in hybrid work environments.
Human error becomes systemic compromise in a successful phishing attack. For this reason, phishing is the first move in an adversarial playbook that spans ransomware, financial fraud, intellectual property theft, and advanced persistent threats.
Beyond the Inbox
Phishing no longer lives solely in the email inbox. Attackers now target users across cloud collaboration tools, SaaS platforms, social media, and mobile applications. They exploit the fragmentation of digital trust — where a link in Slack, Teams, or LinkedIn feels safer than one in an email. They craft messages that align with the target’s context, sometimes using breached data or AI-generated pretexting to heighten believability.
Phishing attacks increasingly use layered techniques — a benign-looking link leading to a convincing replica of a login page, or a multistage redirect chain designed to circumvent link scanning tools. Some operations execute in real time, intercepting credentials and relaying them to login portals before multi-factor authentication can intervene.
The Persistent Threat
What makes phishing insidious is its adaptability. Attackers evolve their methods, bypassing technical controls and exploiting human trust. They understand how organizations work — who approves payments, who has access to privileged systems, who communicates with whom. Their tactics mirror the organization’s communications and culture.
No technology alone can solve phishing. Its power lies in its ability to exploit gaps between security controls and user behavior, between trust and verification. That’s what makes it a first-order cybersecurity problem — one that requires unified defenses across people, process, and technology.
Video 1: The Unit 42 threat research team covers current trends in phishing, modern evasion techniques, and real world attacks.
The Evolution of Phishing
Phishing has developed from broad, static campaigns into dynamic, evasive operations engineered to bypass traditional defenses and maximize success rates. Early phishing relied on simple techniques — mass emails containing links to obviously fraudulent websites, often hosted on compromised infrastructure and indexed in blacklists within hours. The attacker’s goal was scale over subtlety.
Phishing today prioritizes stealth, specificity, and adaptability. Campaigns are tailored to individual victims, often informed by a data breach, open-source intelligence, or AI-generated personalization. Emails mimic internal communications with uncanny accuracy. The payload — usually a URL — doesn’t always lead to a static phishing site. It may redirect through multiple legitimate domains, exploiting open redirects or content delivery platforms to avoid reputation filtering.
Here-and-Gone Infrastructure
Modern phishing infrastructure is designed to vanish before it’s caught. Threat actors now employ just-in-time delivery — sites go live for a few hours or only activate for a small pool of victims, and then disappear. Some use CAPTCHA walls or require email-based tokens to ensure that only the intended target can access the malicious content. These measures prevent automated scanners and web crawlers from retrieving the payload, leaving traditional URL-blocking tools blind.
The Phishing Kit
Phishing kits have become more modular and sophisticated. They often spoof multi-factor workflows or use real-time man-in-the-middle proxies to capture session tokens, not just credentials. This shifts the attacker’s objective from static credential theft to full account takeover and session hijacking, often bypassing MFA entirely.
Behind the scenes, operators distribute their infrastructure across bulletproof hosting providers, fast-flux DNS, and ephemeral domains registered with stolen identities. They automate the deployment of fresh phishing pages, often spinning up hundreds of unique domains in minutes using scripts. These domains rarely live long enough to get blacklisted, and when they are blacklisted, the kit simply rotates to the next preloaded address.
Emergence of the Phishing Supply Chain
Phishing has become a fluid threat — hard to detect, harder to block, and often invisible until the damage is done. It’s not just a user awareness problem anymore. It’s a systemic challenge that exploits the assumptions and delays built into most security stacks today. Addressing it requires a shift from passive detection to proactive disruption of the phishing supply chain.
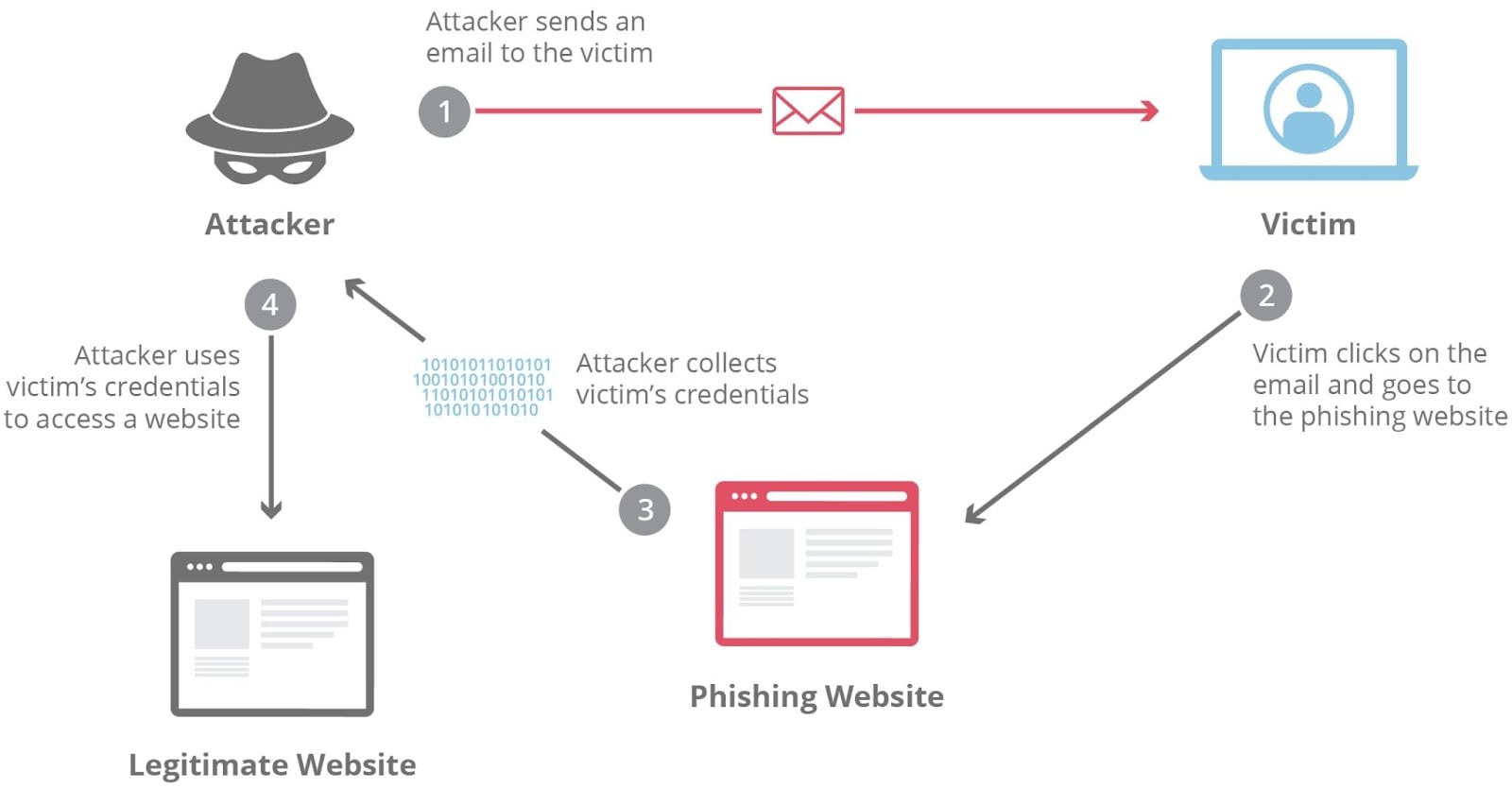
The Anatomy of a Phishing Attack
Phishing attacks unfold with the precision of a well-engineered campaign — planned, staged, and executed to manipulate human behavior and extract value. Understanding the lifecycle, from inception through exploitation, offers a first step to disrupting adversary operations.
Intelligence Gathering and Target Selection
Every phishing campaign begins with a decision — who to target and why. Adversaries perform reconnaissance using publicly available data, breach dumps, social media, and open-source intelligence. They map the organization, identify likely entry points, and choose targets based on value, access, or vulnerability.
For mass campaigns, attackers may select broad criteria such as recent buyers of a product, registered users of a service, or employees of a specific sector. For spear phishing, they zero in on individuals, maybe a finance director involved in M&A or a project lead with elevated GitHub access. The reconnaissance phase informs every decision that follows — especially crafting the bait.
Engineering the Hook
Phishing bait is an engineered psychological artifact designed to provoke trust, urgency, or fear. Attackers often replicate corporate templates, embed known logos, and use stolen email signatures to enhance authenticity. Language is phrased to match the tone and cadence of internal communications.
More advanced attackers generate dynamic content personalized to the recipient’s role, responsibilities, and behavioral profile. The bait might refer to a recent meeting, ongoing litigation, or a shared platform like Microsoft 365 or Workday. Payloads vary from links to fake login pages and weaponized attachments to QR codes and OAuth app authorization requests.
The effectiveness of the bait depends on two things — believability and context. If it feels like something the user expects to receive, it works.
Weaponizing the Communications Stack
The chosen delivery channel reflects both the target’s habits and the attacker’s evasion strategy. While email remains dominant, phishing campaigns increasingly exploit SMS (smishing), voice calls (vishing), collaboration platforms (Teams, Slack), social media, and even QR codes.
Sophisticated operations use infrastructure randomization — rotating domains, link shorteners, and content delivery networks to avoid static detection. Some rely on compromised accounts within the target’s own supply chain, using real email addresses to deliver malware-laced invoices or fraudulent business requests.
Every layer of delivery is built to bypass traditional controls: SPF/DKIM spoofing, SSL-encrypted phishing domains, benign-looking redirect chains, or custom-built payloads that trigger only under live-user conditions.
Gaining the Target’s Trust
Once the bait is opened, the deception phase begins. The goal is to keep the target engaged long enough to lower suspicion and follow instructions. On a spoofed login page, the visual design must mirror the original — logos, color schemes, fonts, even URL slugs.
Some phishing sites display real-time error validation, multistep authentication prompts, or CAPTCHA challenges to appear legitimate. Others proxy requests to the real service behind the scenes, capturing credentials while allowing login to proceed.
Adversaries build flow continuity. A user might click “download” and see a fake “scanning this file” screen. They feel reassured, not threatened. Each moment is engineered to look, sound, and behave like business as usual.
Triggering the Payload or Gaining Access
Once deception succeeds, exploitation begins. The mechanism depends on the phishing objective:
- Credential phishing leads to immediate access or delayed use, depending on the attacker’s intent.
- OAuth consent phishing grants persistent API access to calendars, email, and files — often without triggering MFA.
- Malware delivery exploits zero-day or known vulnerabilities to establish initial access for broader operations (ransomware, data exfiltration, lateral movement).
- Session hijacking allows attackers to bypass MFA and hijack authenticated sessions using stolen tokens or cookies.
Advanced actors don’t act immediately. They maintain stealth, move laterally, and create additional backdoors to preserve access long-term.
Monetization and Operational Use
Once inside, attackers begin extracting value. Credential sets are aggregated for resale or used for lateral compromise. Stolen session tokens can bypass authentication barriers for weeks. Data is filtered, tagged, and exfiltrated — sometimes slowly over encrypted channels, other times in large batches during a single session.
In financial fraud operations, the attacker may alter invoices, reroute payments, or submit unauthorized transactions within hours. In espionage scenarios, data is continuously siphoned — intellectual property, strategic plans, M&A details, or supply chain blueprints.
Harvested data may fuel new phishing campaigns, expand targeting, or support downstream operations by affiliates or buyers on dark web markets.
Why Phishing Is Difficult to Detect
Phishing thrives in the gaps between trust, technology, and timing. Despite years of investment in detection tools, many organizations still fail to stop phishing at the point of contact. Attacks bypass filters, evade analysis, and manipulate even well-trained users. The problem isn't just one of scale or sophistication. It's that phishing operates in real time, adapts to its target, and weaponizes legitimate infrastructure.
Evasion by Design
Phishing campaigns no longer rely on static payloads or crude impersonation. Modern attackers engineer campaigns to actively evade detection systems from the outset. Techniques like sandbox evasion ensure malicious content remains dormant until it reaches a live target. Pages may require mouse movements, keystrokes, or a delay before activating — signals that separate real users from automated scanners.
Cloaking allows attackers to deliver different content based on who’s visiting the page. Security vendors may receive a clean landing page while the victim sees a credential prompt. Cloaking often pairs with device fingerprinting, where attackers gather information like browser type, screen resolution, and geolocation to serve phishing pages only to intended targets. This ensures that bots, crawlers, and unfamiliar IP addresses are shut out.
Tokenization further strengthens this approach. Some campaigns generate one-time-use or victim-specific links. Without the right token — usually embedded in the email — the malicious site won’t load. Even if the link is forwarded to a SOC analyst, the payload has already expired or self-destructed.
Abuse of Trustworthy Platforms
Attackers increasingly host phishing content on legitimate services. SharePoint, OneDrive, Dropbox, Google Drive, Box, and even Adobe Creative Cloud have all been used to deliver phishing payloads. These platforms come with built-in domain trust, SSL encryption, and brand familiarity — factors that allow phishing links to sail past many email security gateways.
Using trusted infrastructure grants more than evasion. It also introduces speed and convenience. An attacker can spin up a fake login page inside a shared document or embed a link behind a cloud-hosted PDF. Security teams can't block access to these platforms without disrupting productivity, which gives attackers persistent reach into enterprise environments.
Trust Signals Are No Longer Reliable
The lock icon in the browser no longer means safety. Attackers register phishing domains with valid SSL certificates to make sites appear secure. They choose domains that visually mimic legitimate ones, often using Unicode characters or deliberate misspellings. Because the sites are hosted on fast infrastructure and rotate frequently, URL reputation systems fall behind.
Brand impersonation also plays a role. Logos, stylesheets, and icons are often copied directly from real websites, sometimes loaded from the original source to avoid detection. Users see the design language they expect — Microsoft 365, Okta, Zoom — and feel no need to scrutinize.
The Limits of Detection
URL filtering, domain reputation, and AI-based content scanning have value, but they were designed for a slower, more predictable threat landscape. URL databases are reactive. They rely on known indicators, reported incidents, and crawler-based analysis. Attackers know this and architect phishing infrastructure to stay a step ahead, using just-in-time activation, IP gating, and ephemeral lifespans that expire before a URL can be blacklisted.
AI and machine learning models offer more promise, especially those tuned to detect suspicious patterns in emails or webpages. But even these systems can be misled by highly customized campaigns, benign-looking redirects, or content loaded dynamically after page render. Adversaries train against the same detection models security teams use, probing inputs until they find what works.
Real-Time Phishing and Adversary-in-the-Browser
Some of the most dangerous phishing tactics happen live. Real-time phishing proxies act as intermediaries between the victim and a real login page. The user believes they’re logging into a legitimate service, but their credentials and session tokens are intercepted as they type. Many of these tools now support multi-factor authentication relay, capturing one-time codes and authenticating with the real service before the code expires.
Adversary-in-the-browser (AitB) attacks extend this further. Once a session is active, malware or browser-based scripts can hijack the session, manipulate web content, or initiate fraudulent transactions — all while the user remains logged in and unaware. These attacks bypass not only MFA, but also many of the behavioral cues users rely on to detect fraud.

Types of Phishing
Phishing permeates every digital touchpoint, from mobile phones to SaaS platforms. Each variation exploits a different attack surface, user behavior, or trust mechanism — which are tailored to the vector, victim, and environment.
Email Phishing: The Ubiquitous Entry Point
Email remains the primary delivery method for phishing campaigns. It’s abundant, inexpensive, and frictionless. Attackers impersonate brands, colleagues, and platforms with striking accuracy, often exploiting urgency, fear, or routine. A typical lure might reference an overdue invoice, a failed delivery, or an account alert — engineered to prompt a click before scrutiny sets in.
Despite years of awareness training and technological investment, email phishing continues to succeed because the deception occurs in milliseconds. Users don’t parse every detail. They react. Most email phishing bypasses technical controls not by sophistication, but by simplicity. It looks like something they expect to see.
Spear Phishing: Precision Over Volume
Spear phishing elevates the attack with tailored context. These campaigns begin with reconnaissance. Attackers scrape LinkedIn, breach data, public filings, and internal documents to craft messages that feel native to the organization. The email might reference an upcoming board meeting, a project code name, or a recent reorg.
The message is often indistinguishable from legitimate internal communication. Because it reflects real-world knowledge, it easily bypasses suspicion. The goal might be credential harvesting, malware delivery, or initiating wire transfers. Spear phishing doesn’t exploit email systems — it exploits trust and internal familiarity.
Whaling: Going After Executives
Whaling is spear phishing directed at the highest levels of the organization — CFOs, CEOs, general counsel, or board members. These individuals often possess elevated access and decision-making authority but may not be bound by the same IT controls or monitoring as the broader workforce.
The attacker crafts the communication to match the executive’s style and priorities. Messages might mimic regulators, journalists, or legal contacts. Successful whaling compromises not just systems, but strategic integrity. It often precedes large-scale financial fraud or insider access to sensitive acquisitions, partnerships, or internal crises.
Smishing and Vishing: Mobile-First Manipulation
Attackers now exploit the device closest to the user: the phone. Smishing uses SMS messages to deliver links or prompt replies. Messages often spoof banks, delivery services, or government agencies. They trigger action by implying urgency — a locked account, a pending payment, or a missed verification.
Vishing, or voice phishing, adds another layer of pressure. Attackers impersonate IT staff, law enforcement, or executives, using scripts to coax victims into sharing credentials, authorizing access, or executing financial transfers. Deepfake audio, spoofed caller IDs, and real-time manipulation have made vishing dangerously effective, especially against finance and customer service personnel.
Clone Phishing: Repackaged Deceit
In a clone phishing attack, the adversary duplicates a legitimate email — often one that the victim has already received — and resends it with a malicious link or attachment substituted in place of the original. The cloned message appears nearly identical to the original, reinforcing the illusion of safety.
Attackers often gain access to a compromised email account or internal system to execute the clone. The victim recognizes the message format, sender, and timing, which dramatically lowers suspicion. Clone phishing is particularly effective in long-term business correspondence or invoicing threads.
Pharming: Redirection at the Infrastructure Level
Pharming subverts DNS or endpoint configurations to redirect users to malicious websites — without their awareness. Instead of sending a phishing email with a suspicious link, the attacker compromises the system’s trust path. The victim types in a legitimate URL, but lands on a counterfeit site.
Pharming often occurs through malicious browser extensions, compromised routers, or manipulated DNS servers. It’s harder to detect the DNS attack because the user doesn't make a conscious decision to follow a suspicious link. They think they’re navigating as usual until credentials are harvested or malware is deployed.
HTTPS Phishing: The Illusion of Security
Many phishing sites now use HTTPS and display the lock icon, which once signified a trusted indicator of legitimacy. Today, attackers purchase SSL certificates for malicious domains, taking advantage of the widespread misunderstanding that HTTPS equals safe.
A phishing site can display a trusted padlock while spoofing login pages for Microsoft, Google, Salesforce, or internal portals. The psychological effect is strong and persuasive.
Social Media Phishing: Public Recon and Private Deceit
Adversaries use LinkedIn, X, Facebook, and other platforms to gather intelligence and launch attacks. Public profiles reveal org charts, project names, vendors, and internal lingo — ideal fuel for crafting convincing lures. Fake recruiter messages, partner inquiries, or support requests often serve as entry points.
Attackers might impersonate a trusted contact, gain initial rapport, and then pivot to email or chat platforms to escalate the attack. In some cases, social media phishing initiates malware delivery via direct messages or shared links.
Consent Phishing: Exploiting OAuth Trust
Consent phishing manipulates users into authorizing a rogue application rather than giving up their credentials directly. The attacker sends a link prompting the user to grant an app access to their account via OAuth. Once the victim consents, the attacker gains persistent access — without needing the password.
These attacks bypass MFA and leave minimal audit trails. OAuth abuse is especially dangerous in cloud-first environments where SSO and third-party integrations are ubiquitous.
Phishing Adversaries and Motives
Phishing isn’t the work of a lone opportunist with a fake email and a lucky click. It’s the operational front end of a global cybercrime economy — structured, scalable, and segmented by function. Adversaries range from low-skill actors running canned campaigns to state-aligned operators executing precision attacks that reshape geopolitical landscapes. Understanding these actors, their motivations, and the infrastructures that support them is critical to mounting an effective defense.
Phishing-as-a-Service
At the entry level, phishing has become a commoditized service. Phishing-as-a-service (PhaaS) platforms provide everything an attacker needs: ready-made phishing kits, domain obfuscation tools, real-time credential harvesting dashboards, and even customer support. A user with no technical skill can rent access to a hosted phishing panel for a monthly fee, often paying in cryptocurrency to maintain anonymity.
Operators of these platforms profit by volume. Their customers launch thousands of campaigns per day, targeting consumers, SMBs, or unprotected enterprise inboxes. The actors care less about whom they hit and more about how many accounts they compromise. They then sell stolen credentials in bulk on dark web markets where other criminals buy them for fraud, botnets, or resale.
Breach as Business
A more sophisticated tier of threat actor uses phishing as an initial access mechanism in coordinated, financially driven attacks. These groups don’t just harvest logins. They execute business email compromise (BEC), wire fraud, and ransomware deployment with a level of planning that mirrors legitimate enterprise operations.
Phishing emails may be crafted after days of internal reconnaissance. Once inside, attackers monitor email traffic, escalate privileges, and hijack financial workflows — intercepting invoices, altering wire instructions, or impersonating executives during high-stakes transactions. In ransomware campaigns, phishing delivers the payload or initial loader that pivots into lateral movement and domain-wide encryption.
Imagine monetization at scale. That’s the goal. Attackers often partner with access brokers, who specialize in obtaining footholds through phishing or malware and sell access to ransomware operators or fraud specialists. The division of labor creates resilience. If one part of the operation is disrupted, another continues. Phishing sits at the top of this supply chain, feeding access into a broader industrialized attack ecosystem.
Nation-State Operators
Not all phishing is driven by money. Nation-state actors use phishing to achieve strategic objectives — intellectual property theft, intelligence gathering, long-term access to supply chains, or disruption of critical infrastructure. Their targets include government agencies, defense contractors, research institutions, journalists, and politically exposed individuals.
Campaigns are precise and quiet. Attackers invest in pretext development, infrastructure hygiene, and evasion. A single campaign may remain active for months before detection, often using compromised legitimate email accounts and real-time interaction to build credibility.
The phishing may be indistinguishable from internal communication. In some cases, adversaries compromise trusted third parties — law firms, consultancies, etc. — to pivot into hardened environments through trusted channels. Their objective isn’t an isolated instance of credential theft. They’re after persistent access. And once inside, they blend into routine workflows, likely using multiple layers of obfuscation to remain under the radar.
Supply Chains and Black Markets
Phishing operates as a service economy. Like any business, it depends on specialization. Developers create phishing kits with interchangeable branding templates, fake login pages, and backend credential harvesters. These kits are sold on dark web forums, often with support packages, update schedules, and testimonials.
Initial access brokers use phishing to compromise endpoints, then monetize those footholds by selling RDP credentials, VPN logins, or SSO access tokens. Others run credential stuffing operations, feeding harvested usernames and passwords into automated bots that test login pages at scale. The access may be used for data theft, account takeover, or resale.
Cryptocurrency enables global monetization with near-total anonymity. Many operations use affiliate models, where operators recruit phishing “affiliates” to run campaigns and share profits. Like modern SaaS, the business scales horizontally — new affiliates launch new campaigns daily while core operators evolve infrastructure and tooling.
The Psychology of Exploitation
Phishing works — not because users are ignorant, but because adversaries understand how humans process information under pressure. Every attack is a psychological play to exploit the cognitive shortcuts we resort to when making decisions. Understanding the mechanisms reframes phishing from a training problem to a behavioral and environmental challenge. Users aren't the weak link. They're the attack surface.
Exploiting Cognitive Overload and Inattentional Blindness
Enterprise environments demand constant attention-switching. We’ve all experienced the vortex, that incessant tug between devices, platforms, and tasks. Multitasking introduces cognitive overload, which narrows working memory and diminishes critical analysis. In this state, we rely on heuristics — fast, intuitive judgments that prioritize efficiency over scrutiny.
Phishing thrives in these moments. The email looks familiar. The brand seems right. The language feels close enough. A decision is made before the logical brain engages. The term for this is inattentional blindness in action — where a user overlooks subtle anomalies because their mental model doesn’t expect deception in the moment.
Attackers know this. They structure their messages for skimming, not deep reading. Subject lines trigger action. Layouts mirror internal systems. Familiarity disarms suspicion. The deception isn’t buried — it’s unexamined.
Bias and Manipulation
Human cognition favors speed over precision in high-pressure situations. Phishing exploits that speed through psychological levers:
- Authority bias: Messages that appear to come from a superior or institution are more likely to be trusted without verification. Attackers exploit this by impersonating executives, HR, IT, or legal departments — roles that carry decision-making weight and limited contestability.
- Urgency triggers: Language that implies a deadline, a penalty, or a missed opportunity forces fast action. Users are less likely to scrutinize a link when a financial deadline or legal threat is implied.
- Familiarity exploitation: Most phishing emails feel routine rather than foreign. Attackers mimic the cadence and structure of workplace communication. They use names from inside the organization. They reference real events. The target isn’t tricked by something odd, but by something expected.
The Remote Work Effect
Remote and hybrid work environments amplify susceptibility. In the office, a strange request from the CFO might prompt a hallway confirmation or a quick Slack message to verify. In remote settings, those social guardrails break down. Users operate with more autonomy and fewer spontaneous interactions, making verification a step that feels optional rather than necessary.
Meanwhile, collaboration now spans more platforms — email, chat, cloud tools, browser apps — each with its own tone, interface, and trust signals. Users don’t always know what normal looks like across tools, which creates fertile ground for deception.
Alert Fatigue and the Dulling of Awareness
The more users are told to be vigilant, the more they normalize the presence of risk and deprioritize it. A well-crafted phishing email doesn’t compete with user knowledge. It competes with a user’s bandwidth.
When vigilance becomes background noise, even the best-trained employee will miss something. Not out of negligence, but because the modern work environment rewards speed, output, and responsiveness. Phishing wins because it mirrors those priorities better than security controls often do.
Lessons from Phishing Incidents
Recent events demonstrate how threat actors adapt their methods in response to seasonal opportunities, emerging technologies, and enterprise vulnerabilities. The following incidents reflect current adversarial tactics and expose gaps that remain in many organizational defenses.
Tax-Themed Phishing Scams Surge in Early 2024
Timeframe: February–April 2024
As the U.S. tax filing deadline approached, Microsoft tracked a wave of phishing campaigns using subject lines like “IRS Audit” and “Verify Tax Information.” Messages often embedded QR codes or short links leading to malware such as Latrodectus and GuLoader, loaders engineered to bypass email security and deploy credential stealers in memory.
Attackers took advantage of seasonal urgency and the familiarity of IRS-related correspondence to push malware undetected. GuLoader’s use of encrypted shellcode and reflective DLL injection made it particularly difficult to isolate and remediate.
Key Takeaway: Predictable seasonal events create high-conversion phishing windows. Organizations must align detection thresholds, communications reviews, and user education to calendar-based risk cycles.
Credential Stuffing Hits Australian Superannuation Funds
Timeframe: January 2024
Australian funds including AustralianSuper and Rest were breached through credential stuffing attacks that exploited password reuse and the absence of MFA. Tens of thousands of accounts were accessed using previously leaked credentials, leading to fraudulent withdrawals and sensitive data exposure.
In many cases, users had no visibility into the compromise until after funds were moved or personal information had been sold.
Key Takeaway: Password hygiene alone no longer suffices. Mandate multifactor authentication — especially in financial systems. Attackers will use old credentials as long as they continue to work.
AI Voice Cloning Powers High-Stakes Vishing
Timeframe: Late 2023–Early 2024
A growing number of vishing attacks now use AI-generated voice clones to impersonate senior leaders. In one case, attackers used an audio deepfake of a CFO to instruct a financial controller to initiate a seven-figure wire transfer. The tone, cadence, and phrasing were eerily accurate — drawn from publicly available earnings calls and internal meeting recordings.
Employees reported no immediate suspicion. The request matched prior workflows and carried the executive’s verbal authority.
Key Takeaway: Trust in voice is no longer a reliable control. Organizations must adopt redundant approval mechanisms for high-risk actions. “Voice verification” is now a vulnerability, not a safeguard.
QR Code Phishing (Quishing) Strikes at Conferences
Timeframe: November 2023 onward
At major industry events, attackers distributed printed materials embedded with malicious QR codes. Targets scanned the codes expecting access to event agendas or Wi-Fi credentials. Instead, they landed on cloned Microsoft login pages that harvested credentials and redirected victims to legitimate sites to avoid suspicion.
The attack bypassed email security entirely, leveraging the physical environment and mobile-centric behavior of attendees.
Key Takeaway: Physical trust vectors like QR codes have become phishing channels. Conference security, employee training, and endpoint protections must account for offline-to-online threat transitions.
Building a Modern Security Stack Against Phishing
Phishing breaks silos. So must your defenses. Organizations need a technical architecture purpose-built to detect, disrupt, and contain phishing across every stage of its lifecycle, from first contact to post-click exploitation. Defensive measures must employ a layered strategy that assumes compromise, detects early signals, limits blast radius, and closes the loop with automated response.
Email Security
Email remains the most exploited channel for phishing delivery, making email security foundational — but insufficient in isolation. Modern defenses must go far beyond basic spam filters or signature-based scanning.
- Advanced Threat Protection (ATP): Tools that perform real-time link analysis, attachment sandboxing, and behavioral scoring at the time of delivery and time-of-click. They must support dynamic analysis, detonation environments, and AI-trained models that detect polymorphic payloads.
- DMARC, SPF, DKIM Enforcement: These protocols are essential to validating sender authenticity, but they are often misconfigured or unenforced. Properly deployed, they can neutralize basic spoofing attacks and make domain impersonation significantly more difficult.
- Natural Language Processing (NLP): Emerging systems analyze tone, writing style, and context to flag anomalous language. NLP engines detect subtle phishing signals, such as urgency phrases or deviation from a known sender’s typical patterns.
- Inline User Warnings: Contextual banners that notify users when a message appears risky — especially when it originates from outside the organization, uses a new domain, or contains suspicious links — help reinforce user skepticism without overwhelming them.
No email security control guarantees protection. Phishing often bypasses filters through credential theft hosted on legitimate cloud services or by using social engineering with no malware at all. That’s why downstream defenses matter equally.
Browser Isolation
Browser isolation assumes that users will eventually click. Instead of relying on detection, it removes risk by executing web content in a remote container and streaming only safe visual output to the user’s browser.
- Cloud-based isolation platforms intercept web sessions and open links in secure containers. If a phishing page includes malicious scripts, credential fields, or malware payloads, they’re contained and can’t reach the user’s machine or network.
- Input control policies can disable form submission or file download when isolation is triggered — neutralizing credential theft and payload delivery at the moment of interaction.
- Granular policies allow high-risk categories (e.g., unknown domains, personal email, shortened links) to trigger isolation automatically, while known business traffic flows unimpeded.
Browser isolation turns phishing from a user decision into a controlled security event. It’s particularly valuable for high-risk roles, unmanaged endpoints, and BYOD scenarios.
Identity Protection
Identity has become the new control plane. Once attackers harvest credentials — especially through phishing — their goal is to move laterally, escalate privileges, and persist in silence. Strong identity protection breaks that chain.
- Phishing-Resistant MFA: Passwords and SMS-based codes are easily phished. Solutions like FIDO2 hardware keys, WebAuthn, and biometric-bound authenticators deliver true phishing resistance. These methods cryptographically bind access to the device and eliminate shared secrets entirely.
- Conditional Access Policies: Dynamic access decisions based on user context — location, device posture, risk signals — can block access or force step-up authentication when anomalies are detected.
- Impossible Travel and Behavioral Anomaly Detection: Identity protection platforms (e.g., Azure AD Identity Protection, Okta ThreatInsight) detect sign-in patterns that deviate from user norms — flagging or blocking access in near real time.
- OAuth App Governance: Consent phishing bypasses passwords altogether. Enterprises must audit and restrict third-party applications with API access to corporate data. Tools that map app usage and enforce granular scopes reduce overexposure.
Identity-first security assumes that credentials will be stolen. The question is whether attackers can do anything with them.
Endpoint Detection and Response (EDR)
When phishing leads to malware installation or session hijacking, the endpoint becomes the battleground. EDR platforms must detect abnormal behaviors — such as credential dumping, script execution, or lateral movement — before they escalate.
- Behavioral Detection Models: Between signature-based antivirus and EDRs, EDRs use machine learning and heuristics to detect tactics, techniques, and procedures (TTPs) used by phishing payloads and post-compromise actors.
- Automated Response Actions: High-confidence detections should trigger automatic remediation steps — such as killing processes, isolating hosts, or revoking tokens — without requiring SOC intervention.
- Session Integrity Controls: Detecting token theft and silent impersonation requires solutions that monitor browser session cookies and can detect adversary-in-the-browser behavior.
EDR is the final layer of defense when deception leads to execution. It must integrate tightly with identity platforms and SIEMs for full-spectrum response.
Related Case Study: Barrett Steel assures business continuity during pandemic and strengthens long-term competitive position
DNS Filtering and Domain Intelligence
Phishing campaigns often rely on new, obscure, or impersonating domains. DNS-layer defenses add another control point before a connection to a malicious site is ever established.
- Real-Time DNS Threat Intelligence: Platforms like Cisco Umbrella or Cloudflare Gateway inspect domain queries and block access to domains known for phishing, malware, or C2h infrastructure.
- New Domain Blocking: Blocking access to domains registered within the past 24–72 hours is an effective tactic, as phishing campaigns often use freshly minted domains to evade static blocklists.
- Typo and Homograph Detection: Many phishing domains rely on visual deception — e.g., rnicrosoft.com vs. microsoft.com. Advanced DNS and proxy tools can detect these variations using fuzzy logic or Unicode normalization.
DNS filtering complements browser isolation by preventing the request in the first place.
API and SaaS Layer Monitoring
In a cloud-first environment, phishing doesn’t end at the endpoint. API security is key, given that attackers use stolen credentials to interact directly with APIs and cloud consoles — bypassing devices entirely.
- CASBs (Cloud Access Security Brokers): These tools monitor cloud traffic for signs of abuse — impossible download volumes, mass sharing, anomalous login sources — and enforce DLP and compliance policies.
- API Threat Detection: Tools like web application firewalls and web application and API protection monitor API interactions to detect impersonation, session hijacking, and anomalous access to SaaS resources.
Phishing goals go beyond access. Attackers seek to move laterally through the cloud infrastructure, making visibility at the API layer imperative.
Defense Integration and Correlation
No single tool solves phishing. The real defense lies in integration — when email security triggers identity risk scoring, which informs access control policy enforcement, which drives browser isolation, which feeds threat intelligence back into detection models.
Security teams must orchestrate detection, containment, and response across domains. That means investing in:
- XDR platforms to correlate email, identity, endpoint, and network signals
- SOAR workflows to automate triage and response at scale
- Deception technologies to identify phishing-driven lateral movement using honeypots and decoy credentials
Building Organizational Immunity
Moving from a reactive response to organizational immunity requires an organizational mindset, one that treats phishing not as a risk to contain, but as a certainty to anticipate.
Phishing resilience is built at the intersection of human intuition, process integrity, and leadership accountability. Organizations that treat phishing as a solvable nuisance will continue to absorb risk. Organizations that build immunity, however, will see phishing as a persistent test of trust, as well as an opportunity to make security a core business function.
Executive Ownership
C-suite executives and board members aren’t only high-value targets, they’re high-leverage influencers. Resilience begins when leadership treats phishing as an operational risk with financial, legal, and reputational implications.
- Executive Training: Executives need focused, simulation-driven briefings that model real-world social engineering tailored to their roles — such as whaling attacks, deepfake voice phishing, and legal pretexts.
- Tabletop Exercises: Run executive-level incident simulations that expose decision-making bottlenecks, escalation confusion, and legal ambiguities. The objective isn’t technical remediation. It’s continuity of leadership under pressure.
- Board-Level Risk Framing: Phishing should be treated as a systemic risk in audit and risk committees, not merely as a subset of cybersecurity hygiene. Metrics should transcend incident counts and reflect resilience maturity.
If phishing is treated as a test of user vigilance, the organization remains reactive. Leadership sets the tone.
Operational Discipline
Resilience depends on structure. Phishing campaigns don’t just succeed because users click. They succeed because organizations lack the internal controls to catch, contain, or correct those clicks. Hardened processes limit how far deception can travel.
- Segregation of Duties: High-risk actions such as payment approvals, data exports, or system changes should require multiparty approval. No executive should be able to authorize a wire transfer via email alone.
- Out-of-Band Verification Protocols: Standardize how users confirm sensitive requests. That means no approvals over email or chat for wire transfers, password resets, or login link requests. Verification should use authenticated, independent channels.
- System Interaction Alerts: Notify users when sensitive actions occur on their accounts — OAuth consents, password changes, login attempts from new locations, etc.. Small friction points trigger early detection and user-initiated reporting.
- Phishing Simulations with Consequence: Effective simulations reflect real attacker techniques. Tailor simulations to business context and follow up with post-click coaching. Track outcomes by business unit and job function to target education where it’s most needed.
Organizations that embed these anti-phishing controls reduce both attack success rate and blast radius.
Incident Response
Many organizations treat phishing detection as a closed-loop event — the malicious email was blocked, the user reported it, or the message was deleted. But that mindset underestimates the sophistication of today’s campaigns. Instead, treat phishing as the start of a breach.
- Phishing Playbooks in the IR Plan: Define structured responses for different phishing types — credential harvesting, malware delivery, consent phishing, business email compromise. Each vector requires a tailored response path with predefined roles, containment steps, and recovery protocols.
- Credential and Session Revocation Workflows: When phishing involves credentials or tokens, automated playbooks should revoke sessions, reset passwords, and notify impacted users immediately.
- Cross-Platform Threat Correlation: Link phishing alerts with identity, endpoint, and cloud platform signals to determine if compromise occurred. A clicked email followed by a login from a new device is a red flag. Correlation closes the gap between detection and impact.
- User Reporting and Escalation Channels: Train users to report suspicious messages using integrated tools, and ensure those reports feed directly into SOC workflows. Rapid user reporting often outpaces technical detection.
Phishing defense isn't just about blocking the attack. It's about being ready when the block fails.
Culture as a Control Surface
Resilient organizations don’t just buy security. They practice it. Culture becomes a control surface when employees feel accountable, when verification is normalized and not seen as a blocker.
- Reward Reporting: Recognize users who report suspected phishing, even when they’ve already clicked. Treat reporting as a security asset.
- Embed Security in Communications Training: Help teams write and recognize secure communication. When every vendor invoice follows the same authenticated process, and every executive request uses the same language and format, deviations are easier to spot.
- Promote Curiosity, Not Suspicion: Suspicion isolates. Curiosity empowers. Teach users how phishing works, and graft them into the detection fabric.
Phishing FAQ
Phishing-as-a-service (PhaaS) is a cybercriminal business model that provides ready-made phishing toolkits and infrastructure to anyone willing to pay for access — no technical skill required. It commodifies phishing in the same way software-as-a-service leveraged scalability, ease of use, and automation to revolutionize legitimate tech.
PhaaS lowers the barrier to entry for attackers by offering:
- Prebuilt phishing kits with customizable templates for impersonating Microsoft, Google, banks, and other trusted brands
- User-friendly dashboards to track victim interaction in real time — such as who clicked, who entered credentials, and from where
- Built-in evasion features like IP filtering, anti-bot protections, and tokenized URLs
- Hosting services, domain registration, and even integrated bulletproof infrastructure
- Support communities and updates, often found in encrypted Telegram channels, dark web forums, or private marketplaces
Some PhaaS operations use a subscription model, while others operate on affiliate schemes where users run phishing campaigns and share a cut of any stolen data or monetized access with the platform owner.
A credential-based attack uses stolen or compromised login credentials (usernames and passwords) to gain unauthorized access to systems, networks, or accounts. These attacks often involve tactics such as:
- Phishing: Deceptive emails or messages trick users into providing their login details.
- Keylogging: Malware that records keystrokes to capture credentials as they are typed.
- Credential Stuffing: Using lists of stolen credentials from one breach to gain access to other systems, exploiting the fact that people often reuse passwords across multiple sites.
- Brute Force Attacks: Systematically trying all possible combinations of usernames and passwords until the correct one is found.
- Man-in-the-Middle Attacks: Intercepting communication between the user and the system to capture credentials.
The best protection against phishing attacks is understanding and identifying the common giveaways of a phishing email that may or may not look suspicious. The following are a few giveaways:
- Messages detailing problems with accounts, bank details, financial transactions, and shipments are prevalent during the holidays when most people are expecting a delivery.
- The language appears incorrect, and the message lacks fluency, which is typical of a native speaker. It features misspellings, poor grammar, and usage issues.
- The message looks like it is from a trusted brand, but it contains unfamiliar elements, such as not-quite-right colors, formats, or fonts.
- The message looks unprofessional, but it is presented as communication from an executive or other influential person.
- The sender is a U.S. federal government agency asking you to provide personally identifiable information (PII) via email or follow a link to a URL that does not end in .gov.
- The sender asks for your social security or tax identification number immediately.
- The sender's address, name, or email address looks strange.
- The message is from someone you don’t recognize asking for gift cards, money transfers, banking, or credit card information.
- The message contains a link to click or an attachment to download, but the address or filename seems unusual.
- Unexpected attachments or files with unusual or unfamiliar names are telltale signs they are malicious.
