What Is OpenVPN? | OpenVPN Defined and Explained
OpenVPN is an open-source VPN protocol designed to secure internet traffic by creating an encrypted connection between devices.
It offers a high level of security with strong encryption, authentication, and support for multiple network configurations. Developed for flexibility, it allows for various VPN setups, including site-to-site connections and remote client access.
How Does OpenVPN Work?
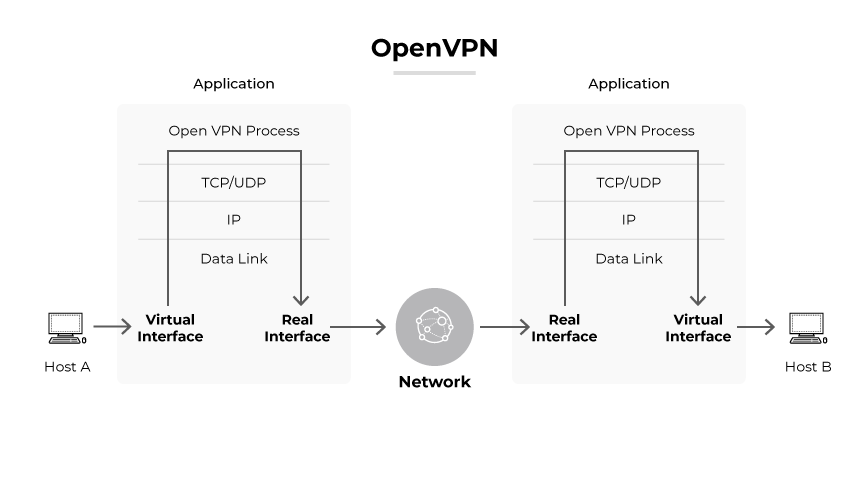
OpenVPN is an open-source software project, a VPN tunneling protocol, and the name of the company behind the protocol. It establishes secure network connections over the internet. OpenVPN functions by creating encrypted tunnels for data packets, ensuring secure transmission between client and server.
The protocol operates in two modes: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). TCP mode ensures data packets are delivered in the correct order and retransmits any lost packets. TCP mode provides reliability, though at the expense of speed. UDP mode is commonly the default. UDP is faster but doesn’t guarantee the order of packets, making it less reliable but more efficient for streaming and real-time communications.
OpenVPN supports IPv4 and IPv6, which can be used simultaneously. IPv4 and IPv6 are IP protocols that determine how IP addresses appear online.
OpenVPN uses the OpenSSL library to handle encryption and decryption, providing a secure channel for data traversal. It uses the SSL/TLS protocol for key exchange, allowing for strong encryption mechanisms that include up to 256-bit encryption with advanced cipher suites. This ensures that even if data packets are intercepted, they can’t be deciphered without the corresponding keys.
In its role as VPN software, OpenVPN enables the configuration and management of VPN connections. It provides the tools necessary for enterprises to establish VPN servers, manage user access, and control traffic flow. OpenVPN’s admin web interface simplifies the management of VPN servers and user access. The admin web interface provides a user-friendly interface for administrators to control network settings and monitor system performance.
The software is adaptable, supporting a range of operating systems. It offers features like network bridging, full tunneling, and split tunneling, which are crucial for complex enterprise network configurations.
The software's flexibility extends to its authentication methods, where it supports mutual authentication between VPN clients and servers using a variety of methods. Methods include pre-shared keys, certificate-based, and username/password authentication. The flexibility ensures enterprises can enforce security policies without being limited by the VPN software.
How Secure Is OpenVPN?
OpenVPN is generally considered secure because of its open-source model, strong encryption capabilities, and robust authentication and key exchange mechanisms. Its adaptability to both TCP and UDP protocols allows for flexibility in balancing the need for speed and data integrity, making it a potential option for enterprise VPN needs.
Being open source means code is available for audit by any third party, which is thought to encourage transparency and collaborative improvement. Security experts globally examine the code for vulnerabilities. The ongoing vetting process may help maintain the protocol’s robust defense against potential security threats.
OpenVPN’s technical makeup contributes significantly to its security posture. Since the OpenSSL library is frequently updated, the protocol can offer the latest in encryption standards. By default, the OpenVPN protocol uses AES-256 bit encryption, which is considered military grade and is often used by financial institutions for securing transactions.
The protocol offers several layers of connection security. It uses SSL/TLS for secure key exchange and supports perfect forward secrecy (PFS). PFS ensures that even if a key is compromised, only a small portion of data is at risk because keys are rotated and changed regularly.
OpenVPN Use Cases
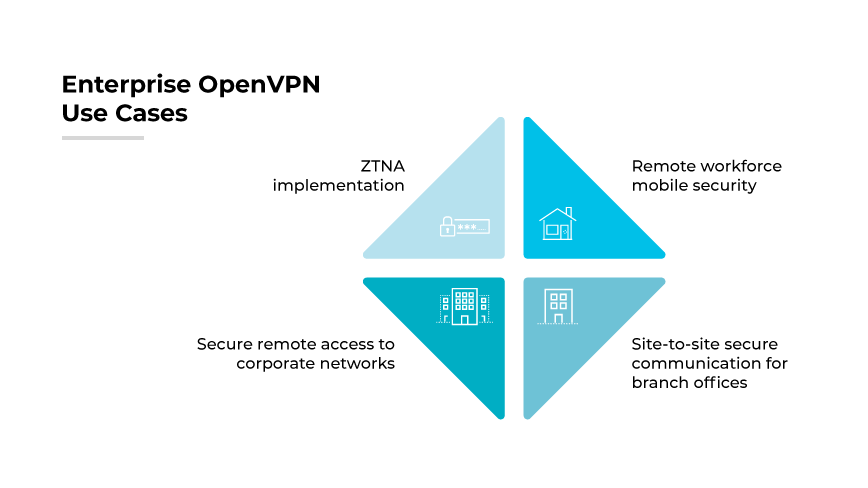
OpenVPN serves as a robust solution for securing corporate communications and ensuring data protection. Using OpenVPN, it is relatively easy for security teams to establish encrypted tunnels between a company’s headquarters and its various branches, facilitating secure and reliable remote access for employees. This is important when sensitive data must be shared across potentially insecure public networks. The protocol’s flexibility enables it to adapt to the unique security requirements of each enterprise.
It is also instrumental in enabling secure mobile access. With an increasing number of employees working remotely, the protocol ensures they can connect to corporate networks securely from any location. Secure access is critical for maintaining the confidentiality and integrity of company data on mobile devices. The protocol’s compatibility with various operating systems allows deployment across a range of devices, further enhancing its utility in a diverse enterprise environment.
OpenVPN configuration supports multifactor authentication. This capability is integral to implementing a Zero Trust security model, where trust in the network is never assumed, and verification is required from anyone trying to access resources.
OpenVPN Platform Support
OpenVPN's broad platform support makes it a versatile choice for diverse enterprise network environments.
OpenVPN is compatible with the following operating systems:
- Windows
- macOS
- Linux
- iOS
- Android
- FreeBSD
- OpenBSD
- NetBSD
- Solaris
- QNX
- Maemo
- Synology NAS devices
- ChromeOS
- Routers with firmware such as DD-WRT, OpenWrt, Tomato
- Network appliances using OPNSense and pfSense
The protocol’s web-based configuration options offer additional versatility, allowing administrators to manage VPN settings through a web browser, facilitating ease of deployment and maintenance.
It is important to note that while the OpenVPN protocol is compatible with these platforms, it often requires the installation of additional software to function. This may include third-party clients or configuration of network settings within the device’s operating system.
OpenVPN Ports
OpenVPN commonly uses two types of ports, depending on the underlying protocol chosen for the VPN connection. By default, OpenVPN runs over UDP port 1194.
When it operates over TCP, it often uses TCP port 443. This is the same port used by HTTPS traffic, which can help traffic to blend in with regular SSL traffic, making it more difficult for firewalls to block traffic.
Pros and Cons of OpenVPN
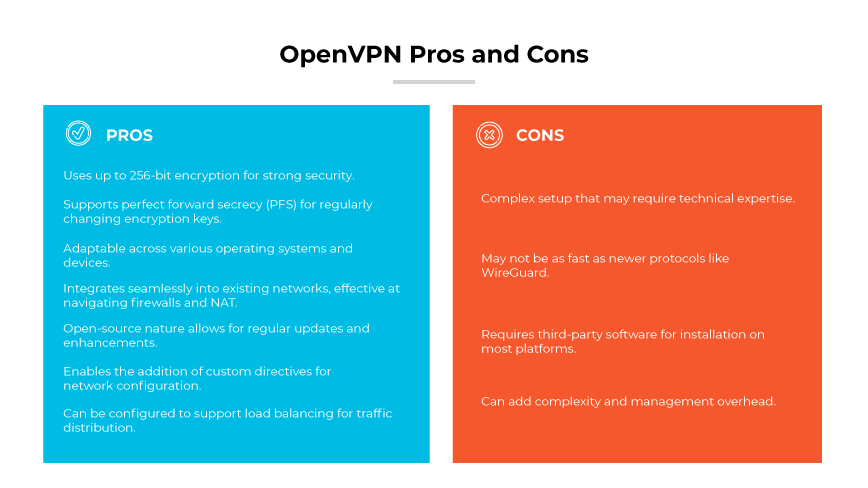
One of the primary benefits of OpenVPN is its strong security framework, which uses up to 256-bit encryption, ensuring sensitive data remains protected. Its support for perfect forward secrecy (PFS) means encryption keys are frequently changed, reducing the risk of long-term data exposure.
Adaptability across various operating systems and devices makes it an option for organizations with diverse IT ecosystems. It allows for seamless integration into existing networks and is particularly effective at navigating through firewalls and network address translation (NAT). This makes the protocol potentially suitable for companies with complex network infrastructures. Its open-source nature facilitates regular updates and community-driven enhancements.
OpenVPN also supports adding custom directives. Custom directives allow the assignment of static IP addresses to connecting VPN clients or to send traffic through a proxy server after the VPN connection is made.
The protocol can be configured to support load balancing, allowing for an even distribution of client connections and traffic load. This can be useful for businesses with high volumes of traffic or those requiring high availability for network services.
OpenVPN isn’t without its drawbacks. Setup complexity can be a barrier for those without sufficient expertise, potentially leading to incorrect configurations that may compromise security. While the protocol can be quick, it may not be as fast as some of the newer protocols like WireGuard, which can impact performance for bandwidth intensive activities. Since the protocol is not natively supported on most platforms, it requires the installation of third-party software, which can add to complexity and management overhead.
Comparing OpenVPN with Other Protocols
OpenVPN can be an option for some businesses because of its security and configurability. Depending on specific needs such as speed, ease of use, and mobile connectivity, other protocols like IKEv2/IPSec and WireGuard may offer compelling advantages. The choice of protocol should be based on a balanced consideration of an organization’s priorities, resources, and the nature of the data traffic it needs to secure.
OpenVPN vs. PPTP
OpenVPN is known for its robust security, which outweighs the older PPTP (Point-to-Point Tunneling Protocol). PPTP may offer speed but lags behind in terms of encryption standards, using 128-bit keys. This may make PPTP a less favorable option for enterprises especially concerned with protecting sensitive data.
OpenVPN vs. L2TP/IPsec
L2TP (Layer 2 Tunneling Protocol), often paired with IPsec, provides better security than PPTP but still lacks the flexibility and firewall traversal capabilities of OpenVPN. Enterprises might find OpenVPN more reliable because it doesn't face the same issues with NAT firewalls that L2TP/IPsec does. It also offers a more secure connection by default.
OpenVPN vs. IKEv2/IPsec
IKEv2/IPsec is known for speed and the ability to quickly re-establish lost connections, which is particularly useful for mobile users. OpenVPN offers a higher level of security and configurability. While IKEv2/IPsec can be faster, OpenVPN's security features may make it a preferred choice for enterprises requiring stringent data protection.
OpenVPN vs. SSTP
SSTP (Secure Socket Tunneling Protocol), integrated into Windows platforms, offers a level of service comparable to OpenVPN. However, OpenVPN's open-source nature means it is subject to scrutiny by the global tech community, which is thought by some to lead to a more secure and private experience.
OpenVPN vs. WireGuard
WireGuard is a modern VPN protocol with a much smaller codebase, making it easier to audit and less prone to bugs. It is designed to be faster and more secure than OpenVPN. While WireGuard's performance is noteworthy, OpenVPN's widespread adoption and proven track record continue to make it a reliable choice for many organizations.
How to Set Up OpenVPN
Setting up OpenVPN in an enterprise context involves several steps to ensure secure communication across the network. This guide outlines the basic process to get the protocol up and running.
By following these steps, organizations can create a secure, private communication channel for remote access and site-to-site connections. It's crucial to ensure the setup is done by individuals with the necessary technical knowledge to avoid any potential misconfigurations that could lead to security vulnerabilities.
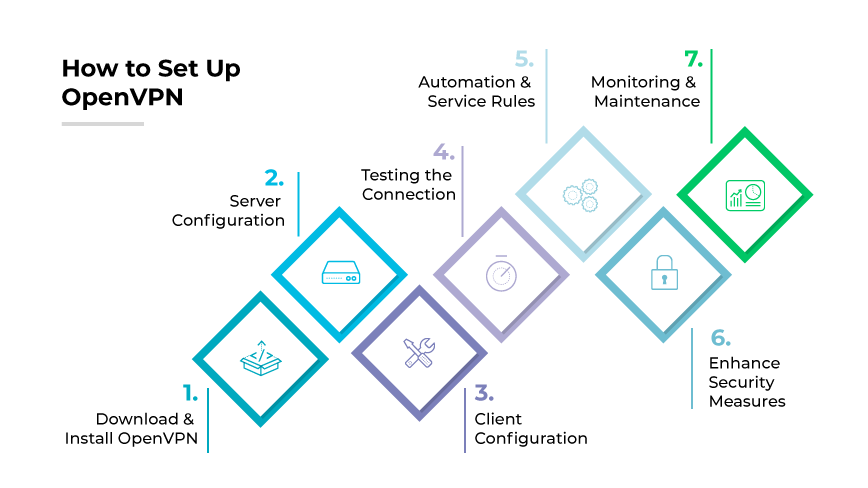
1. Download and Install OpenVPN
- Download the OpenVPN package suitable for your operating system.
- Install the software following the provided instructions, ensuring all necessary components are included.
2. Server Configuration
- Set up the OpenVPN server, which involves configuring network settings, such as routing and subnet creation.
- Generate cryptographic keys and certificates, which will be used to encrypt the VPN traffic.
3. Client Configuration
- Install the OpenVPN client software on the devices that will connect to the OpenVPN server.
- Import the configuration file provided by the server, including the necessary certificates and keys.
4. Testing the Connection
- Establish a connection between the VPN client and the server to test the VPN tunnel.
- Check for any connectivity issues and ensure that the traffic is properly encrypted and routed through the VPN.
5. Automation and Service Rules
- Configure the service to start automatically upon system boot.
- Define user access rules and permissions within the configuration to maintain network security.
6. Enhance Security Measures
- Implement additional authentication methods, such as multifactor authentication, to bolster security.
- Set up a firewall and define rules that align with your organization's security policies.
7. Monitoring and Maintenance
- Regularly monitor VPN connections for any unusual activity or performance issues.
- Keep software updated to the latest version to incorporate security patches and feature improvements.