What Is an SSL VPN?
An SSL VPN is a virtual private network that enables a secure connection over the internet for remote access via web browsers using SSL or TLS encryption.
It provides users secure access to network resources without specialized client software, making it a convenient option for organizations to extend corporate network access to remote employees securely. This VPN type is generally user friendly, facilitating secure remote work with minimal setup.
How Does an SSL VPN Work?
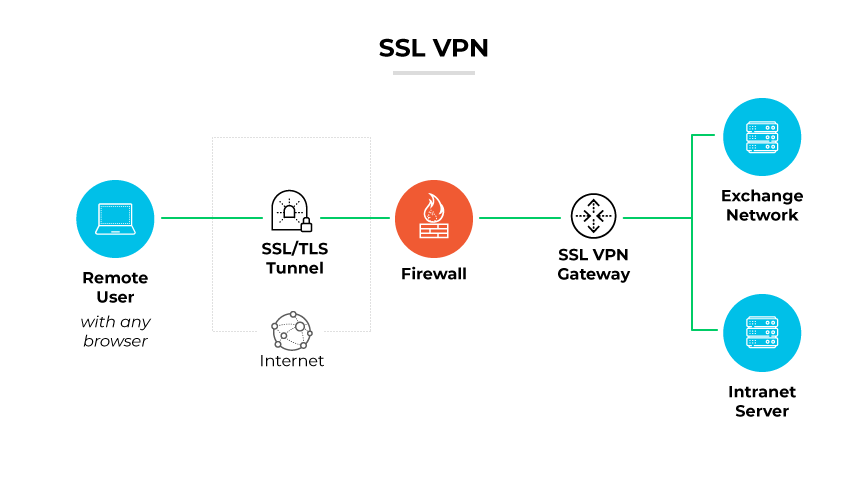
An SSL VPN (Secure Sockets Layer Virtual Private Network) uses the Secure Sockets Layer (SSL)/Transport Layer Security (TLS) protocol to create a secure, encrypted connection over the internet. This connection is typically used for giving remote users access to internal network resources without requiring specialized client software—just a standard web browser on any operating system.
The SSL VPN works by initiating a secure session from a user's device to the VPN server. When a user enters their credentials on a login page, the SSL VPN creates an encrypted tunnel between their web browser and the SSL VPN gateway. This tunnel ensures transmitted data is secure, confidential, and tamperproof.
Once the secure tunnel is established, the SSL VPN maintains a secure connection by using robust encryption standards. This allows remote users to access network resources securely as if they were physically connected to the network's internal infrastructure. The SSL VPN also validates the server's identity to the user, often through certificates, ensuring that users connect to the authenticated network only.
While traditional VPNs may require client installation and configuration on each device, an SSL VPN can be accessed through any device with a compliant web browser, simplifying remote access.
Types of SSL VPN
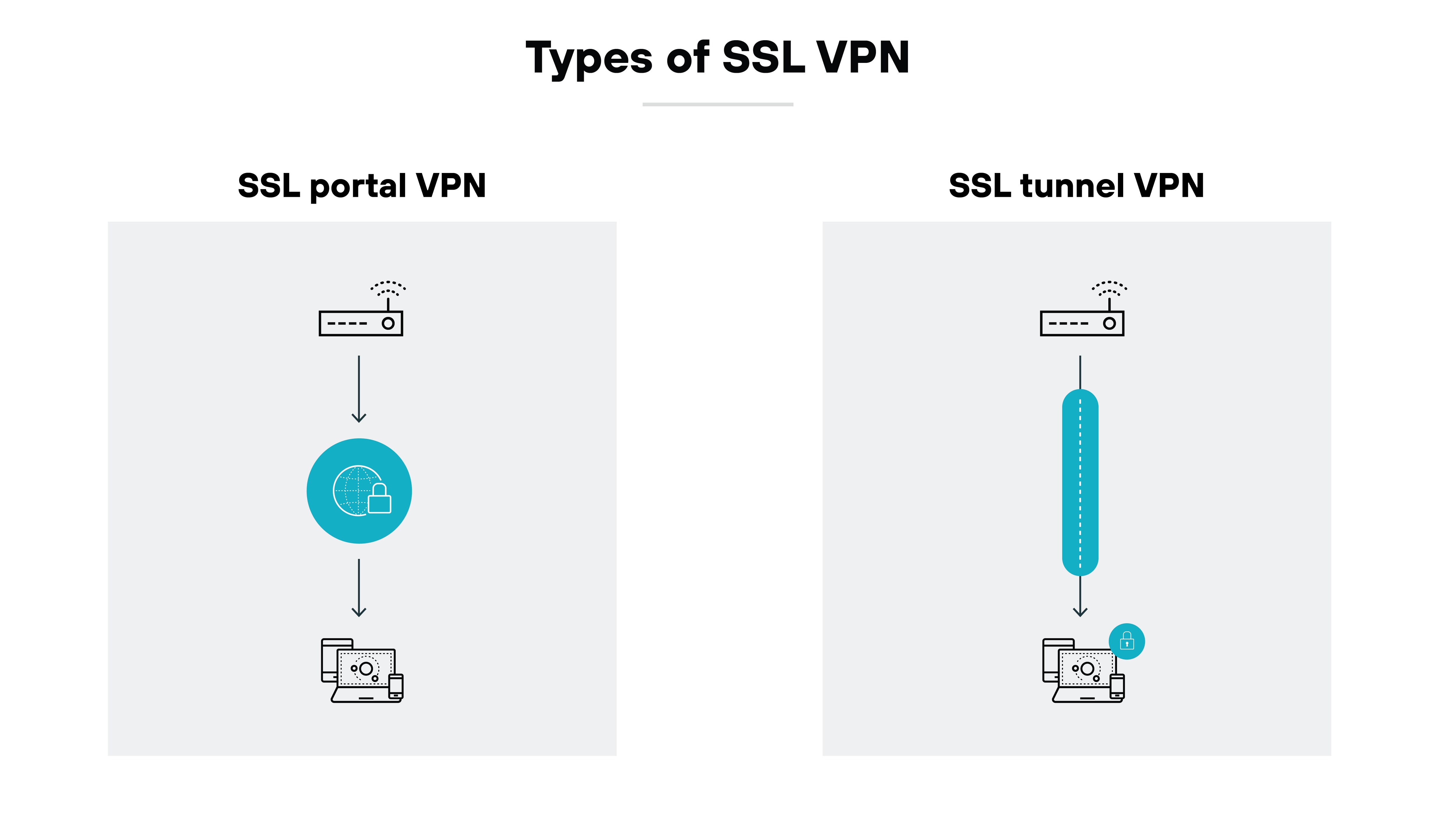
SSL VPNs address secure remote access needs with two distinct types: SSL Portal VPN and SSL Tunnel VPN. Both types provide secure connectivity, but they differ in the level of access and complexity they offer to the end user.
SSL Portal VPN
An SSL portal VPN offers a user-friendly, web-based interface where authenticated users can securely access specific network services through a single sign-on. Users connect through their browsers to a portal page, which serves as the gateway to authorized resources. The simplicity of an SSL portal VPN makes it suitable for straightforward access needs, but it’s limited to browser-accessible services and does not support complex client-server applications.
SSL Tunnel VPN
In contrast, an SSL Tunnel VPN provides more extensive access to network services, including applications and protocols that are not naturally web based. It requires the installation of client-side software or browser plug-ins like JavaScript or Java, enabling the creation of a tunnel that secures all traffic to the network. An SSL Tunnel VPN offers a broader range of access, suitable for users who need a connection to multiple services or applications within a network.
SSL VPN Benefits
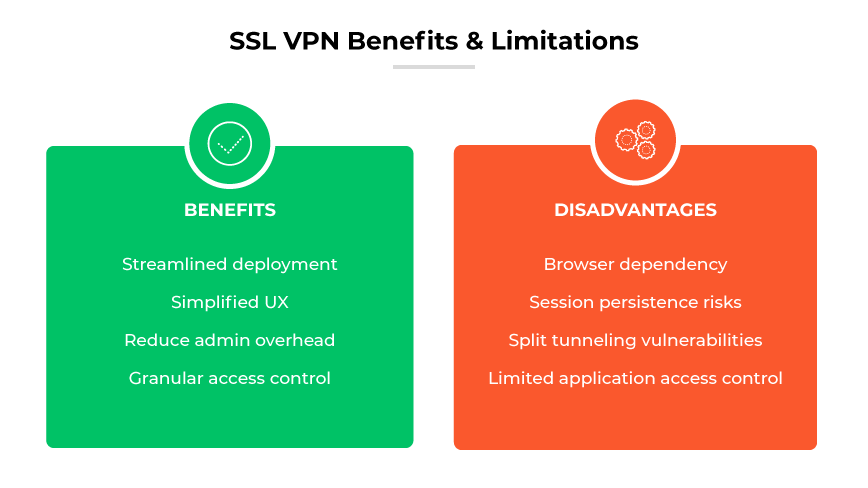
Streamlined Deployment
SSL VPN deployment is streamlined since they leverage TLS protocols native to modern web browsers, eliminating the need for additional client software. This simplicity accelerates the setup process, allowing users to access network resources rapidly and securely.
Simplified User Experience
SSL VPNs offer a user friendly interface akin to typical web browsing, facilitating ease of use without compromising on security. The intuitive experience reduces the learning curve for new users and minimizes the need for extensive user support.
Reduced Administrative Overhead
Due to their browser based nature, SSL VPNs significantly reduce administrative burden. Automatic updates and lesser need for configuration contribute to lower IT support costs and simpler management.
Granular Access Control
SSL VPNs provide detailed access control, enabling administrators to create tunnels to specific applications rather than the entire network. This enhances security by limiting user access to only necessary resources.
SSL VPN Disadvantages
Browser Dependency
SSL VPNs are inherently dependent on web browsers, which can limit the scope of their protection to web based applications. Reliance on browsers means that non-web applications may not benefit from the same level of security, potentially exposing other aspects of enterprise systems to risk.
Session Persistence Risks
Given that SSL VPNs maintain sessions through browsers, any session left open inadvertently exposes the network to potential unauthorized access. This risk is heightened if the device is shared or in a location with less stringent security controls.
Split Tunneling Vulnerabilities
The convenience of split tunneling with SSL VPNs can be a double-edged sword, as it allows traffic to bypass the VPN's secure tunnel. This can inadvertently create openings for attackers to exploit unsecured pathways into the network.
Limited Application Access Control
While SSL VPNs can offer granular control at the application level, they may not provide comprehensive coverage across all enterprise resources. This can lead to inconsistent security policies and potential exposure of sensitive data.
IPsec vs. SSL VPN
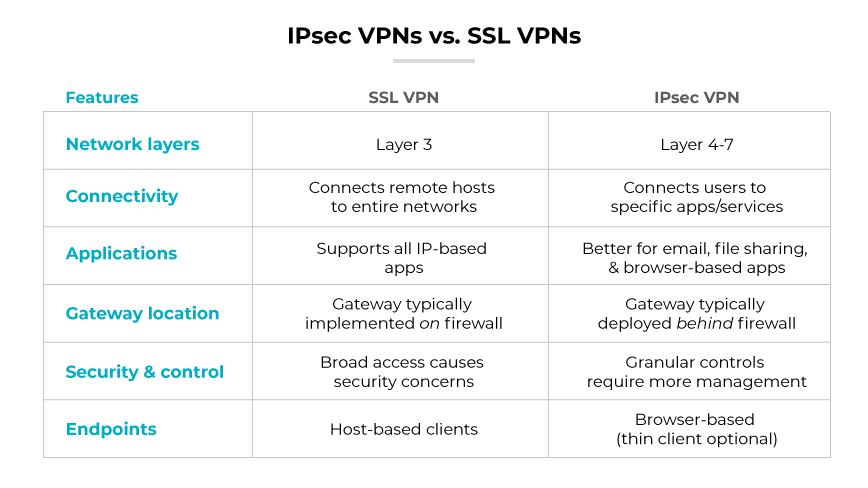
An IPsec VPN creates a secure, encrypted connection at the network level. An SSL VPN provides secure access through a web browser at the application level.
IPsec VPNs are typically used for site-to-site connections and require installing client software on devices, which can be a complex process. They offer a high level of security by encrypting all traffic between the VPN client and the VPN server, making them suitable for connecting entire networks over the internet.
SSL VPNs are user friendly, requiring no special client software apart from a standard web browser. This makes SSL VPNs more adaptable to a remote workforce where users need secure access to specific applications rather than the entire network. However, because SSL VPNs operate at the application level, they may not be as comprehensive in their security coverage as IPsec VPNs, potentially leaving non-web traffic less protected.
