What Are the Different Types of VPN Protocols?
Types of VPN protocols include:
- Internet Protocol Security (IPsec)
- Secure Socket Tunneling Protocol (SSTP)
- WireGuard
- OpenVPN
- SoftEther
- Point-to-Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP)
Internet Protocol Security (IPsec)
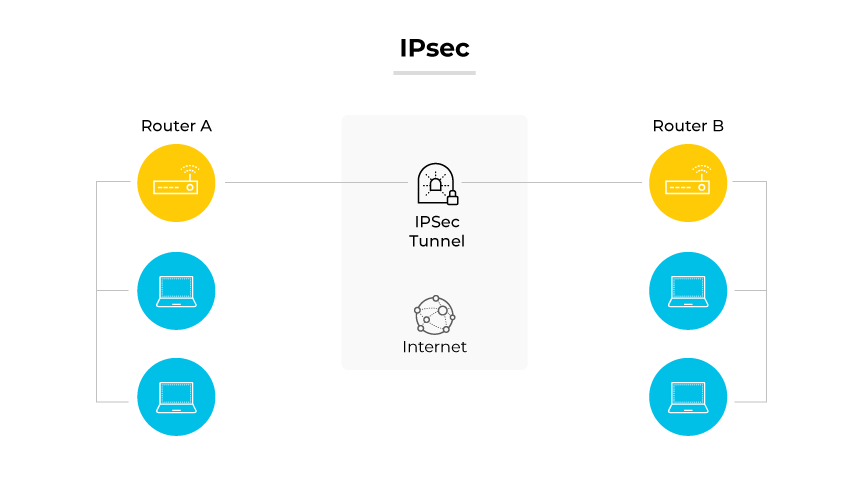
Internet Protocol Security (IPsec) is a set of protocols that support secure communication over Internet Protocol (IP) networks through authentication and encryption. Its primary purpose is to ensure data integrity, data confidentiality, and data origin authentication between two communicating parties.
IPsec operates by encrypting and authenticating all IP packet transfers. It functions through two main modes: Transport and Tunnel. Transport mode encrypts only the message within the data packet, while Tunnel mode encrypts the entire data packet. Two primary protocols within IPsec, the Authentication Header (AH) and Encapsulating Security Payload (ESP), provide data origin authentication, connectionless integrity, and an anti-replay service.
IPsec is widely implemented in the formation of secure tunnels, especially for VPNs. Enterprises use IPsec for secure remote user access to corporate networks, site-to-site connections, and network layer encryption.
IPsec advantages include its high security and versatility across different network layer protocols. Configuration complexity can be a drawback, requiring expertise for proper setup and maintenance. While IPsec is protocol-independent and supports a wide range of encryption algorithms, managing its keys and certifications can present challenges.
Secure Socket Tunneling Protocol (SSTP)

Secure Socket Tunneling Protocol (SSTP) is a VPN communication protocol developed to provide secure, encrypted connections over a network. SSTP uses SSL/TLS encryption, which is the same technology that underpins secure internet connections. SSL/TLS encryption ensures the privacy and security of data as it travels across the internet.
SSTP works by channeling VPN traffic through the SSL 3.0 channel. This means it can benefit from features like SSL's integrated connection integrity and encryption capabilities. SSTP typically uses the standard HTTPS port (TCP 443), which allows it to bypass most firewalls and network restrictions. SSTP is a reliable choice for users who need to ensure their VPN connections are not blocked or throttled by local network management tools.
SSTP is commonly used in scenarios where other VPN protocols might be blocked. Since it operates over the HTTPS port, it is less likely to be detected and filtered. This is helpful in environments with restrictive internet policies or for those who need to access potentially sensitive information over a public Wi-Fi network.
SSTP benefits include its high level of security, strong encryption methods, and the protocol's ability to traverse firewalls. SSTP is a proprietary protocol developed by Microsoft, which may limit its trustworthiness for some users. SSTP is primarily designed for Windows, which can restrict its usability on other operating systems.
WireGuard
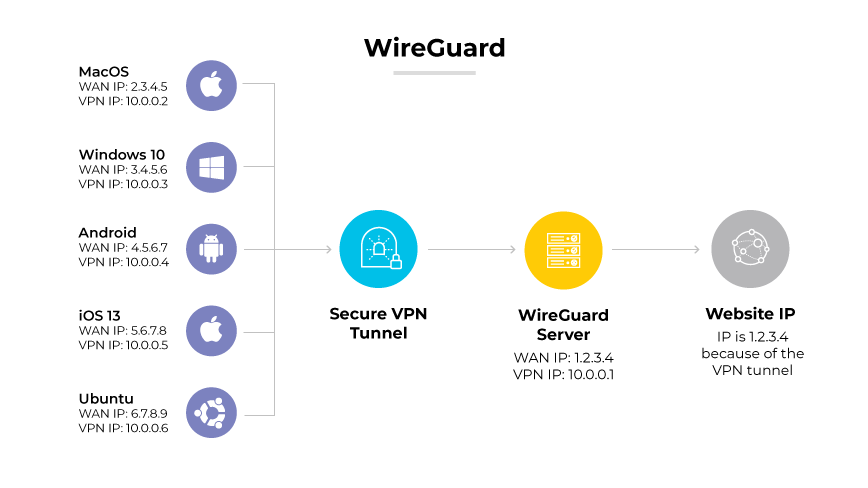
WireGuard is a cutting-edge VPN protocol known for its simplicity and high-speed performance. WireGuard is designed to be much simpler and faster than legacy protocols, using state-of-the-art cryptographic techniques. As an open-source project, WireGuard's streamlined approach results in better efficiency and ease of use.
Functioning through a unique mechanism called cryptokey routing, WireGuard establishes secure VPN connections with remarkable speed and agility. It works by assigning static IP addresses to VPN clients and managing traffic through cryptographic keys. This approach simplifies the setup process, reduces latency, and increases the protocol's performance over traditional VPN protocols.
WireGuard is beneficial for businesses with a mobile workforce or requirements for fast, reliable connections for cloud services. Since WireGuard is lightweight, it can run on various devices (embedded systems, full-fledged servers, etc.) making it versatile for different enterprise network scenarios.
WireGuard has its drawbacks. The static IP address assignment can raise privacy concerns as it could potentially log user activity. WireGuard is still undergoing development, which means it may lack the extensive testing and wide-scale trust established by older protocols.
OpenVPN
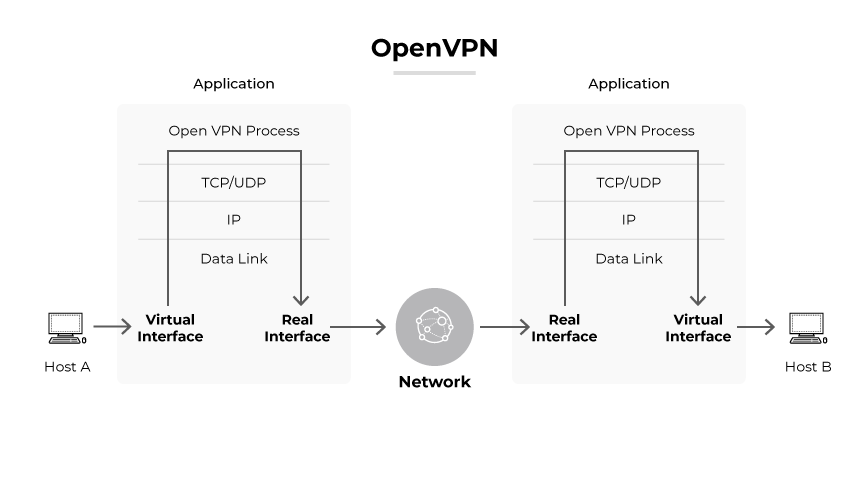
OpenVPN is a robust, secure VPN protocol favored in the enterprise environment for its strong encryption and configurability. This protocol works by creating secure point-to-point or site-to-site connections in routed or bridged configurations. OpenVPN uses custom security protocols that utilize SSL/TLS for key exchange.
OpenVPN operates by encapsulating data in SSL/TLS encrypted packets, which are then transmitted over the network. This protocol can run over either the TCP (Transmission Control Protocol) or UDP (User Datagram Protocol) internet protocols. TCP ensures reliable delivery of data packets while UDP prioritizes speed, making OpenVPN versatile for different network performance needs.
Businesses use OpenVPN for its adaptability to various network types and ability to establish a secure, reliable connection over intranet and internet. OpenVPN is useful for organizations with remote workforces and/or high security requirements.
OpenVPN advantages include its strong security profile, open-source nature (which allows for peer review and audits), and the ability to bypass firewalls. OpenVPN is not known to be easy to set up and configure, particularly for those without extensive networking knowledge. The protocol does not natively support most operating systems.
SoftEther
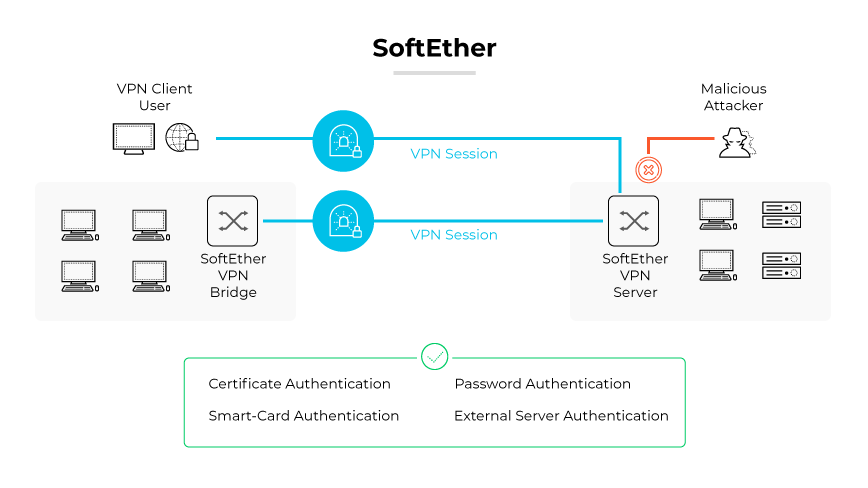
SoftEther (Software Ethernet), is a versatile VPN protocol known for performance and interoperability. SoftEther is an open-source, multiprotocol VPN software that supports SSL VPN, L2TP/IPsec, OpenVPN, and SSTP, all within a single VPN server.
The protocol operates by establishing secure client-server communication through SSL-VPN Tunneling on HTTPS. SoftEther bypasses firewalls and NATs, making it highly effective for users within restricted network environments. SoftEther is also comprehensive VPN solution that facilitates remote-access and site-to-site VPN.
SoftEther works well in various scenarios, including individual remote access, corporate networks, and connecting multiple on-premises sites securely. Its ability to support different VPN protocols makes it a universal tool for creating VPN tunnels.
SoftEther stands out for strong encryption capabilities, resistance to network restrictions, and support for various operating systems. SoftEther is less known compared to established protocols like OpenVPN, which can limit adoption. It may present a steeper learning curve for network administrators.
Point-to-Point Tunneling Protocol (PPTP)
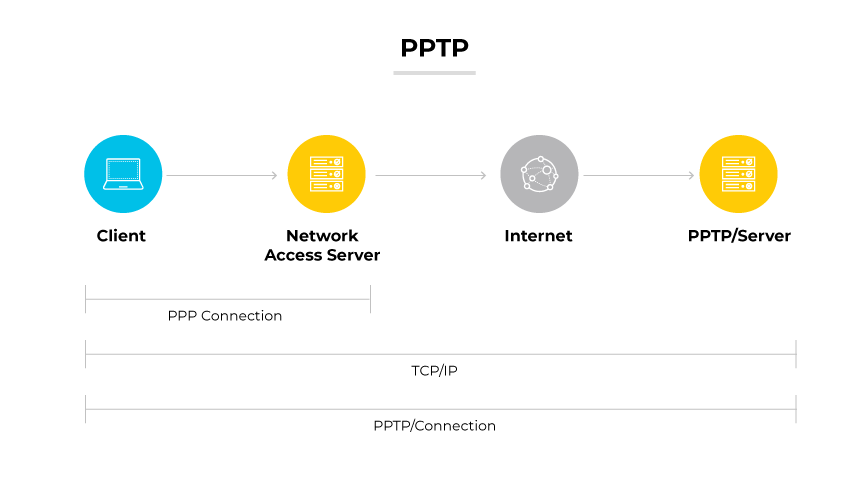
Developed by Microsoft, Point-to-Point Tunneling Protocol (PPTP) is one of the oldest VPN protocols. PPTP facilitates secure data transmission by creating a tunnel for point-to-point communication. The protocol encapsulates data packets within an IP envelope, allowing them to be sent across a network.
PPTP works by using a control channel over TCP and a GRE tunnel operating to encapsulate PPP packets. The simple setup makes it relatively fast and widely compatible with various devices and network configurations. PPTP is not recommended for sensitive communications because it uses weaker encryption standards.
The primary use case for PPTP is scenarios where legacy support is required, or speed is more critical than security. PPTP is not advisable for transmitting confidential enterprise data because of its known security vulnerabilities.
PPTP pros include speed and ease of setup. The protocol is integrated into most operating systems. The disadvantages outweigh the benefits because PPTP is insecure. Advanced encryption standards have surpassed PPTP, making it obsolete for enterprises concerned with protecting sensitive data.
Layer 2 Tunneling Protocol (L2TP)

Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol. It does not provide encryption or confidentiality by itself. L2TP relies on an encryption protocol that it passes within the tunnel to provide privacy. L2TP is often paired with IPsec, which is responsible for encryption and secure transport of data between endpoints.
L2TP works by encapsulating data packets within L2TP frames that are sent over the internet. When combined with IPsec, data packets are encrypted and authenticated, providing a secure conduit for transmitting sensitive information. This pairing is commonly referred to as L2TP/IPsec. The protocol is widely used for creating VPN connections.
Typical use cases for L2TP include connecting branch offices to a central corporate network, access, and enhancing security for data transmission over the internet. L2TP remains a preferred choice for businesses because it isn’t as complex as newer protocols and offers support across various devices and platforms.
L2TP benefits include compatibility and the ability to work across multiple devices. L2TP has several disadvantages, including potential speed bottlenecks (because of double encapsulation) and difficulties traversing firewalls compared to protocols that use stealth techniques.
Which VPN Protocol Is Best for Your Business?
To choose the best VPN protocol for your business, evaluate security, speed, and network compatibility requirements. Protocols like L2TP/IPsec are widely supported and offer a balance of speed and security. Protocols with stronger encryption and more rigorous authentication processes may be more appropriate for organizations requiring enhanced security measures.
Each protocol comes with its own set of advantages. Some prioritize encryption strength, others are optimized for speed to support bandwidth-intensive tasks, and several offer superior stability for mobile devices and remote users.
The right choice will align with your business's specific use cases, network architecture, VPN services, and performance expectations. A careful assessment of requirements will guide you to the most suitable protocol for a secure and efficient VPN experience. Work with your VPN provider to make the best decision possible.
| VPN Protocols Comparison | ||
|---|---|---|
| Protocol | Advantages | Disadvantages |
| IPsec | - High security - Versatile across network protocols |
- Complex configuration - Key and certificate management challenges |
| SSTP | - Strong encryption - Bypasses firewalls using HTTPS port |
- Proprietary to Microsoft - Limited to Windows OS |
| WireGuard | - Simple and fast - State-of-the-art cryptography - Efficient and easy to use |
- Static IP assignments may raise privacy concerns - Still under development |
| OpenVPN | - Strong encryption and security - Open-source and auditable - Flexible across different networks |
- Difficult to set up and configure - Requires networking knowledge |
| SoftEther | - Strong encryption and interoperability - Supports various protocols - Effective in restricted networks |
- Less known, which can limit adoption - Steeper learning curve |
| PPTP | - Fast and easy to set up - Widely compatible with devices |
- Known security vulnerabilities - Outdated encryption standards |
| L2TP/IPsec | - Widely compatible and easy to use - Works across various devices and platforms |
- Can be slow due to double encapsulation - Difficulty with firewall traversal |
