- 1. How Does a VPN Concentrator Work?
- 2. Why Use a VPN Concentrator?
- 3. VPN Concentrator Benefits
- 4. VPN Concentrator Disadvantages
- 5. VPN Concentrator Encryption Protocol Types
- 6. VPN Concentrator vs. VPN Router
- 7. VPN Concentrator vs. Site-to-Site VPN
- 8. VPN Concentrator vs. IPsec Encryption
- 9. VPN Concentrator vs. VPN Client
- 10. VPN Concentrator FAQs
- How Does a VPN Concentrator Work?
- Why Use a VPN Concentrator?
- VPN Concentrator Benefits
- VPN Concentrator Disadvantages
- VPN Concentrator Encryption Protocol Types
- VPN Concentrator vs. VPN Router
- VPN Concentrator vs. Site-to-Site VPN
- VPN Concentrator vs. IPsec Encryption
- VPN Concentrator vs. VPN Client
- VPN Concentrator FAQs
What Is a VPN Concentrator?
- How Does a VPN Concentrator Work?
- Why Use a VPN Concentrator?
- VPN Concentrator Benefits
- VPN Concentrator Disadvantages
- VPN Concentrator Encryption Protocol Types
- VPN Concentrator vs. VPN Router
- VPN Concentrator vs. Site-to-Site VPN
- VPN Concentrator vs. IPsec Encryption
- VPN Concentrator vs. VPN Client
- VPN Concentrator FAQs
A VPN concentrator is a network device designed to manage VPN traffic for multiple users.
It establishes and controls VPN connections, allowing remote workers to access the corporate network securely. This device supports a high number of simultaneous connections, ensuring that remote access is both reliable and secure. Secure remote access is critical for organizations with a substantial remote workforce or multiple branches.
How Does a VPN Concentrator Work?
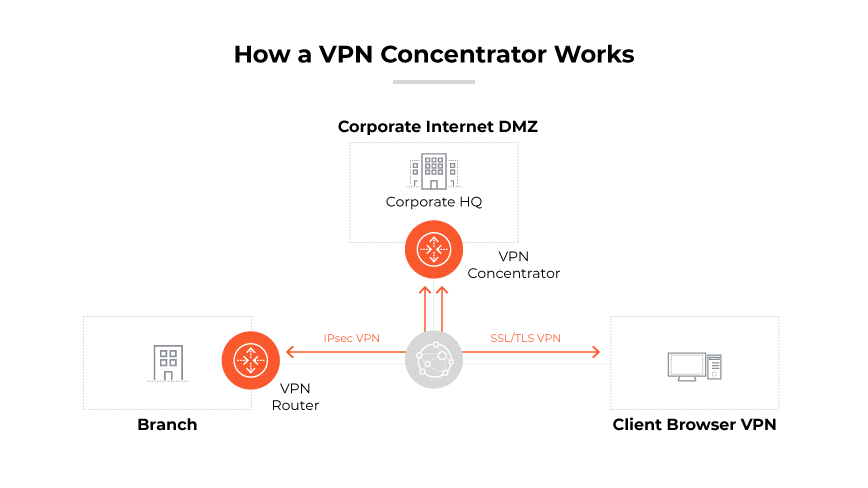
A VPN (virtual private network) concentrator serves as a robust connector and manager for multiple encrypted VPN tunnels within an enterprise network. It begins its role at the network’s edge, ensuring that all incoming and outgoing data passes through its secure channels. The concentrator authenticates remote users, granting access to the network only after verifying their credentials. Once a user is authenticated, the concentrator assigns a unique IP address to them, enabling individual identification within the network.
The device handles the heavy lifting of encryption and decryption, ensuring that data sent to and from the enterprise network is unreadable to any unauthorized parties. By managing all VPN connections, the concentrator maintains the integrity and confidentiality of the data traffic flowing in and out of the enterprise network. This function is critical for protecting against data breaches and ensuring secure communication for remote or mobile employees.
In addition, the concentrator maintains the cryptographic keys necessary for secure data transmission. It uses established VPN protocols to manage the complexities of creating, maintaining, and terminating the encrypted tunnels, ensuring seamless and secure connectivity for all users. This process is vital for companies that require a high level of data protection and for employees who need to access sensitive corporate resources from various locations.
Why Use a VPN Concentrator?
A VPN concentrator is used in an enterprise environment to handle large volumes of VPN connections. Its purpose is to establish and manage secure communications for remote workers accessing corporate resources. This device functions as a router specifically designed for creating, configuring, and managing VPN network traffic. It serves as a central point for remote connections, channeling secure, encrypted data to and from multiple endpoints in a controlled and efficient manner.
Organizations employ a VPN concentrator to support simultaneous connections, enabling remote access to a network without compromising security. This capability is essential for large-scale operations where employees, stakeholders, or branch offices require dependable and consistent access to the central network for daily operations.
VPN Concentrator Benefits
Seamless Integration
Once the VPN client software is initiated, it automatically connects to the VPN concentrator. This automatic tunnel creation allows for a seamless user experience without manual configuration for each session.
Centralized Control
A VPN concentrator centralizes the management of network connections, allowing for simplified administrative oversight of VPN access and security policies.
Advanced Routing Capabilities
As an advanced form of routing equipment, VPN concentrators manage more complex protocols and algorithms than standard routers. This provides specialized functionality tailored for secure, high-volume connections.
Efficient Scalability
The concentrator is adept at quickly generating multiple VPN tunnels. This accommodates the connection needs of numerous remote employees without the latency associated with individual VPN client setups.
Access Management
With a VPN concentrator, administrators can implement fine-grained access controls. This allows them to restrict user access to sensitive areas of the network based on defined roles or attributes.
VPN Concentrator Disadvantages
High Initial Investment
A VPN concentrator can entail significant upfront costs. The expense is often associated with the enterprise-grade hardware and software required for deployment.
Bandwidth Limitations
VPN concentrators have finite bandwidth capacities. When numerous remote workers connect simultaneously, the available bandwidth may be insufficient, leading to potential service degradation.
Complexity in Management
The configuration of a VPN concentrator demands skilled personnel. It requires network engineers to ensure smooth integration with existing systems and adherence to security protocols.
Performance Ceiling
The concentrator has a maximum performance limit. To enhance performance beyond this limit, additional hardware may be necessary, incurring further investment.
Scalability Concerns
Scaling up services with a hardware VPN concentrator can be challenging. Expansion often requires additional concentrators, which increases costs and complexity.
Single Point of Failure
If a VPN concentrator experiences a failure, all connected network communications can be compromised, which can be particularly disruptive for large organizations with extensive remote workforces.
VPN Concentrator Encryption Protocol Types

PPTP/MPPE
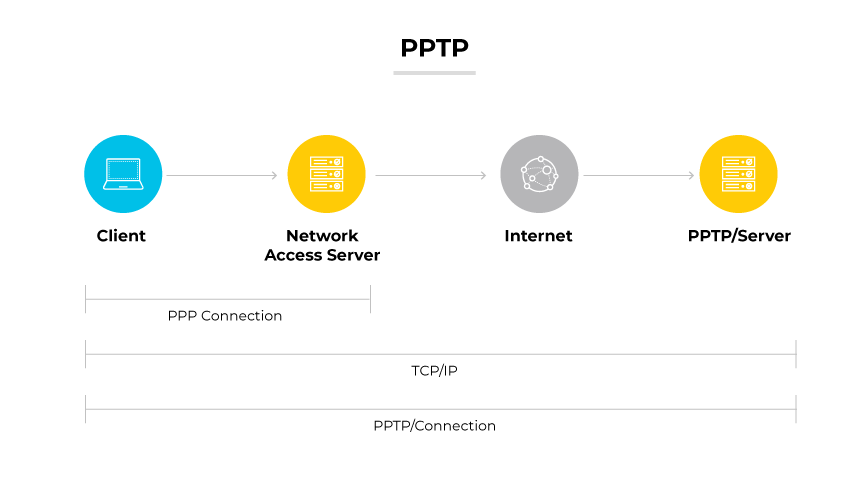
Point-to-Point Tunneling Protocol combined with Microsoft Point-to-Point Encryption is a common encryption protocol for VPNs. It leverages MPPE to encrypt data, as PPTP does not offer encryption independently.
L2TP/IPsec
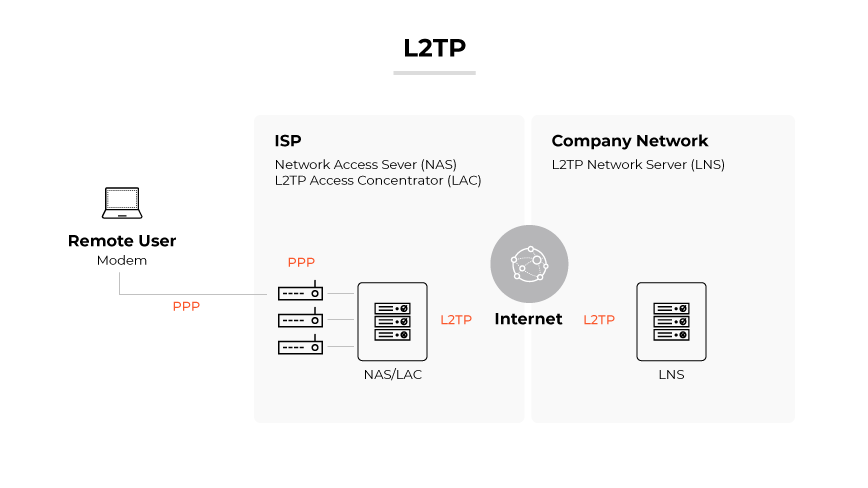
Layer 2 Tunneling Protocol over IPsec is frequently used in remote-access VPNs, especially with legacy systems. IPsec is responsible for encryption services when using L2TP.
IPsec
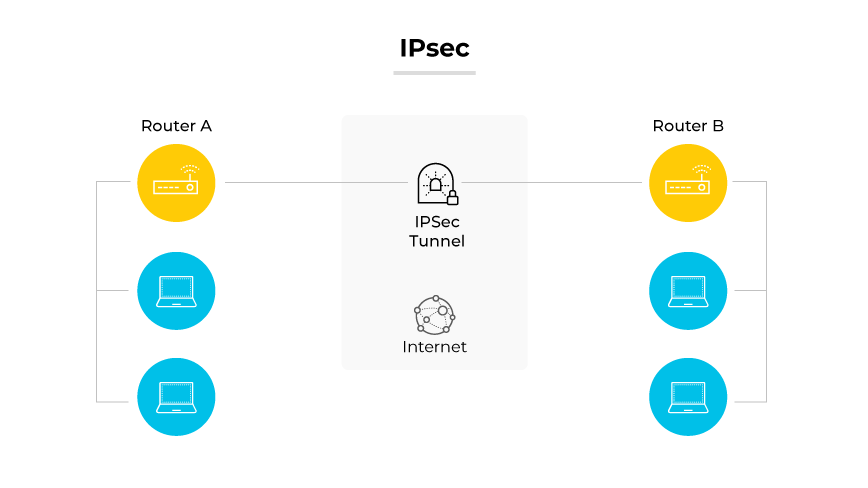
Internet Protocol Security is a robust suite of protocols. It provides high-level encryption and authentication. IPsec operates in two modes, each serving different security functions.
SSL/TLS
Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are encryption protocols that can secure VPN connections. They facilitate browser-based secure remote access, allowing VPN concentrators to support diverse client systems without dedicated VPN software.
VPN Concentrator vs. VPN Router
A VPN concentrator is designed for enterprises requiring extensive remote access capabilities. It can handle a high number of simultaneous VPN connections, providing robust security and seamless connectivity for a large number of remote employees. Its advanced features are tailored to maintain performance and security across complex and large-scale network infrastructures.
In contrast, a VPN router is geared toward smaller networks, suitable for encrypting the data traffic of devices within a single location. While it offers a foundational level of security, its capabilities are not intended for the scalability and performance demands of larger businesses with substantial remote workforce or multisite networks.
VPN Concentrator vs. Site-to-Site VPN
A VPN is ideal for organizations that have a dispersed workforce requiring secure, remote access to the network. VPN concentrators are adept at managing traffic and ensuring secure connections for users, regardless of their location, across various devices including mobile and laptops.
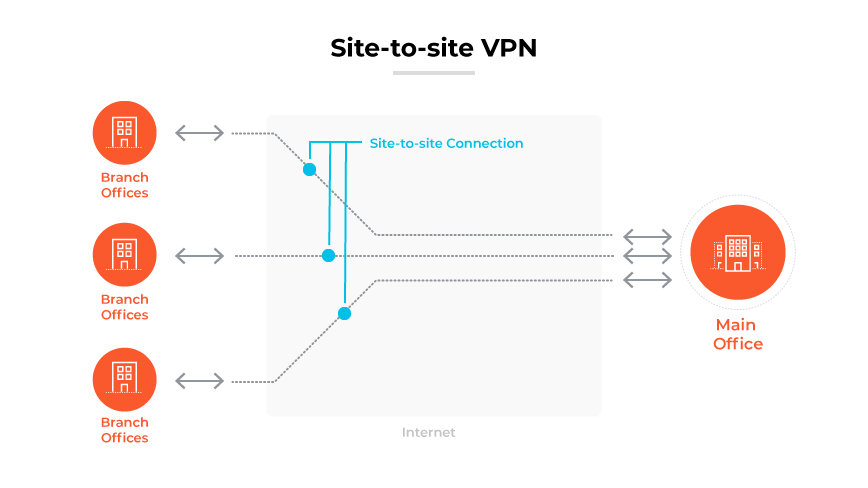
In contrast, a site-to-site VPN is a configuration that creates a virtual bridge connecting entire networks at different locations, making them act as a single network. This is particularly useful for businesses with multiple branches that need to work closely together and share resources as if they were located within the same local network. Site-to-site VPNs are not primarily concerned with individual user connections but focus on linking network resources across different offices.
VPN Concentrator vs. IPsec Encryption
A VPN concentrator is used in creating and managing a large quantity of VPN tunnels, often in an enterprise setting. The VPN concentrator is responsible for ensuring that the connection is stable and secure, managing encryption, and maintaining the integrity of data transmission.
IPsec encryption, on the other hand, is a protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. It is commonly used for establishing VPN tunnels, offering high levels of security for data. While a VPN concentrator might employ IPsec as one of the methods for creating a secure tunnel, IPsec itself is concerned with the actual encryption and security of the data packets being sent over the network.
VPN Concentrator vs. VPN Client
A VPN concentrator provides a centralized VPN solution, handling security protocols, encryption, and traffic routing for multiple users at the same time, often across diverse geographic locations. The concentrator ensures secure, encrypted connections for a large number of devices, centralizing the VPN administration for an organization.
In contrast, a VPN client is software that allows an individual device to establish a secure connection to a VPN server. It is used by remote workers or individuals who need to access the corporate network securely from various locations. While the VPN concentrator serves the collective network security needs, the VPN client addresses the secure connection requirements of a single user or device.
