- 1. What Is a Firewall?
- 2. What Is an Intrusion Detection System (IDS)?
- 3. What Is an Intrusion Prevention System (IPS)?
- 4. What Are the Differences Between a Firewall, IDS, and IPS?
- 5. What Are the Similarities Between a Firewall, IDS, and IPS?
- 6. Can a Firewall and IDS or IPS Work Together?
- 7. IDS vs. IPS vs. Firewall FAQs
- What Is a Firewall?
- What Is an Intrusion Detection System (IDS)?
- What Is an Intrusion Prevention System (IPS)?
- What Are the Differences Between a Firewall, IDS, and IPS?
- What Are the Similarities Between a Firewall, IDS, and IPS?
- Can a Firewall and IDS or IPS Work Together?
- IDS vs. IPS vs. Firewall FAQs
IPS. vs. IDS vs. Firewall: What Are the Differences?
- What Is a Firewall?
- What Is an Intrusion Detection System (IDS)?
- What Is an Intrusion Prevention System (IPS)?
- What Are the Differences Between a Firewall, IDS, and IPS?
- What Are the Similarities Between a Firewall, IDS, and IPS?
- Can a Firewall and IDS or IPS Work Together?
- IDS vs. IPS vs. Firewall FAQs
The firewall, IPS, and IDS differ in that the firewall acts as a filter for traffic based on security rules, the IPS actively blocks threats, and the IDS monitors and alerts on potential security breaches.
A firewall sets the boundaries for network traffic, blocking or allowing data based on predetermined protocols. An IDS watches over network activities, flagging any irregularities for review, without directly affecting data flow. An IPS plays an assertive role, not just detecting, but also preventing identified threats from compromising the network.
What Is a Firewall?

A firewall is a network security solution that inspects and regulates traffic based on predetermined security rules, allowing, denying, or rejecting the traffic accordingly.
Firewalls work as a checkpoint between internal networks and potential external threats. They analyze data packets against defined security protocols. Depending on these protocols, firewalls determine whether data should be permitted or denied.
Every piece of data on the internet travels in network packets. Firewalls assess these packets against a set of rules, blocking them if they don't conform. These data packets, which are structured for internet transit, carry essential information, including their source, destination, and other crucial data that defines their journey across the network.
What Is an Intrusion Detection System (IDS)?

An intrusion detection system (IDS) identifies potential threats and weaknesses in networked systems. An IDS examines network traffic, alerting administrators to suspicious activities without intervening in data transmission.
IDSes are positioned out of the main traffic flow. They typically operate by mirroring traffic to assess threats, preserving network performance by analyzing a duplicate stream of data. This setup ensures the IDS remains a non-disruptive observer.
IDS systems come in various forms, including network intrusion detection system (NIDS), host based intrusion detection system (HIDS), protocol based (PIDS), application protocol based (APIDS), and hybrid. There is also a subgroup of IDS detection methods. The two most common variations are signature based IDS and anomaly based IDS.
An IDS differentiates between usual network operations and anomalous, potentially harmful activities. It achieves this by evaluating traffic against known patterns of misuse and unusual behavior, focusing on inconsistencies across network protocols and application behaviors.
What Is an Intrusion Prevention System (IPS)?
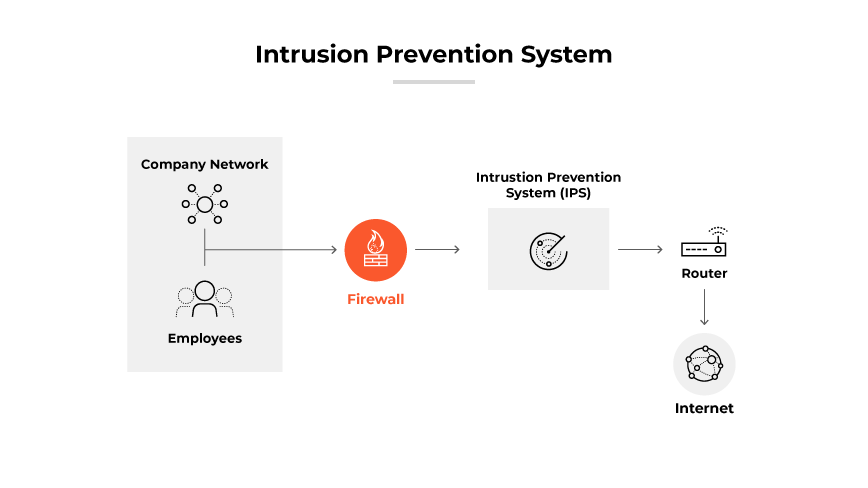
Intrusion prevention systems (IPS) are dynamic security solutions that intercept and analyze malicious traffic. They operate preemptively to mitigate threats before they can infiltrate network defenses. This reduces the workload of security teams.
IPS tools are especially effective at identifying and stopping attempts to exploit vulnerabilities. They act swiftly to block these threats, often bridging the gap between the emergence of a vulnerability and the deployment of a patch. With the evolution of network security, IPS functionality integrates into broader systems like unified threat management devices and next generation firewalls. Modern IPS tools also extend into cloud connected services.
IPS placement is in the direct path of network traffic. This allows the IPS to scrutinize and act on threats in real time, contrasting with the passive monitoring approach of its precursor, the IDS. Typically positioned just beyond the firewall, the IPS examines incoming data and takes automated actions when necessary. IPS systems can signal alerts, discard harmful data, block source addresses, and reset connections to prevent further attacks.
To minimize false positives, IPS systems differentiate between genuine threats and benign data. Intrusion prevention systems achieve this using various techniques including signature based detection, which relies on known patterns of exploits; anomaly based detection, which compares network activity against established baselines; and policy based detection, which enforces specific security rules configured by administrators. These methods ensure only authorized access is permitted.
What Are the Differences Between a Firewall, IDS, and IPS?
| Intrusion Prevention System vs. Intrusion Detection system vs. Firewall | |||
|---|---|---|---|
| Parameter | Firewall | IPS | IDS |
| Purpose | A network security device that filters incoming and outgoing traffic based on predetermined security rules. | A device that inspects and prevents identified threats in real-time by analyzing traffic. | A system that monitors network or system activities for malicious actions or policy violations. |
| Operation | Filters traffic based on rules applied to addresses and port numbers. | Examines traffic for real-time attacks and intervenes to stop them on detection. | Observes traffic and looks for attack patterns or anomalies, generating alerts. |
| Configuration mode | Operates in either inline or transparent mode at the network's boundary. | Typically inline, positioned after the firewall within the network layer. | Generally operates in monitoring mode, not inline with traffic flow. |
| Traffic path | Should be the primary route of network traffic. | Placed after the firewall to examine filtered traffic. | Analyzes traffic after it has passed through the firewall. |
| Placement | Located at the network perimeter as the initial defense line. | Positioned right after the firewall, before the internal network. | Resides within the network, typically after the IPS for deeper traffic analysis. |
| Response to unauthorized traffic | Blocks or permits traffic based on rule evaluation. | Actively prevents the progression of detected threats. | Issues alerts or alarms upon detecting suspicious activities. |
Traffic Control Versus Monitoring
A firewall functions by regulating traffic, acting as a gatekeeper that permits or blocks data packets based on predefined security protocols to maintain the integrity of the internal network. In contrast, an intrusion prevention system (IPS) actively controls the traffic by taking automated actions to block threats, operating directly in the traffic flow. Meanwhile, an intrusion detection system (IDS) solely monitors the network, assessing for signs of malicious activity and alerting administrators, without directly influencing the traffic stream.
Position in Network Security Architecture
The firewall serves as the first line of defense against external threats. It examines all incoming and outgoing data, only allowing that adheres to the established security policy. An IPS, unlike the passive IDS, is actively involved in network traffic flow. Positioned behind the firewall, the IPS can analyze and take action on data, potentially stopping threats before they reach internal resources.
Method of Defense Implementation
Firewalls primarily operate by a set of defined rules that control network traffic flow based on IP addresses, ports, and protocols. An IDS, on the other hand, uses pattern recognition to identify suspicious activities by comparing network traffic against a database of known threats. It works as an observer, signaling alerts for unusual behavior without taking action. Meanwhile, an IPS takes a more proactive approach. IPSes actively analyze and take preventive measures against potential threats, such as blocking harmful data or resetting connections to thwart ongoing attacks.
Impact on Network Performance
Firewalls are efficient at their role with minimal impact on network performance. IDS systems monitor traffic in a duplicate stream, so they are non-disruptive to the network's operational flow. In contrast, IPS systems can have a more substantial impact on network performance. This is because of their inline positioning and active threat prevention mechanisms. However, it is important to note that modern ISP design minimizes this impact.
What Are the Similarities Between a Firewall, IDS, and IPS?
| How Are Firewalls, IDS, and IPS Alike? |
|---|
|
Security Objective
Firewalls, IDS, and IPS are all critical components of network security, designed to protect information systems from threats and unauthorized access. Each technology plays a role in identifying and managing the flow of data packets to ensure only safe and legitimate traffic is allowed, contributing to the overall defense strategy of an organization's digital assets.
Policy Based Management
These security mechanisms are all managed through policies defined by network administrators. Firewalls enforce access controls, while IDS and IPS systems use policies to determine the normal baseline of network behavior and the appropriate response to threats. Policies in these systems are crucial in defining the security posture of the network.
Deployment in Diverse Environments
The deployment of firewalls, IDS, and IPS is versatile across different computing environments. Whether it is on premises hardware, software based solutions, or cloud environments, each can be configured to suit the specific security needs of the network it is protecting, offering flexibility in a variety of IT infrastructures.
Support for Threat Detection and Prevention
Firewalls, IDS, and IPS all support the detection and prevention of threats. They provide a layer of security that contributes to the detection of suspicious activities, with firewalls filtering traffic and IDS/IPS systems analyzing it for potential threats, enhancing the security measures within a network.
Can a Firewall and IDS or IPS Work Together?
Firewalls, intrusion detection systems, and intrusion prevention systems are fundamental network security components. With today’s modern solutions, they can work together to provide a comprehensive security framework.
A firewall serves as the primary barrier at the edge of the network, monitoring and controlling incoming and outgoing traffic based on predefined rules. In conjunction with a firewall, an IDS analyzes traffic patterns to detect anomalies, and an IPS takes preventive actions against identified threats.
The collaboration between these systems enhances security. The firewall filters initial traffic, while the IDS and IPS analyze the filtered traffic for potential threats. This layered approach ensures that even if a threat bypasses the firewall, the IDS can alert administrators to suspicious activities, and the IPS can act to prevent the threat from causing harm. Such integration allows for a more robust security posture, capable of responding to a wide range of security incidents.
Recent developments in network security have led to the convergence of these tools into unified solutions. Next generation firewalls incorporate the functionalities of traditional firewalls with IDS and IPS capabilities, creating a single, more effective point of policy enforcement. These unified systems simplify the security infrastructure and can enforce policies based on comprehensive data, including user identity, enabling more nuanced security controls.