- 1. How does FWaaS work?
- 2. Why is FWaaS important?
- 3. What are the primary features of FWaaS?
- 4. What are the benefits of FWaaS?
- 5. What are the potential challenges of FWaaS?
- 6. How much does FWaaS cost?
- 7. What are the differences between FWaaS and NGFWs?
- 8. What is the role of FWaaS in the SASE framework?
- 9. FWaaS FAQs
What Is Firewall as a Service (FWaaS)? | FWaaS Defined & Explained
Firewall as a service (FWaaS) is a cloud-based firewall solution that provides network security capabilities through a subscription model.
Unlike traditional firewalls, FWaaS operates in the cloud, offering features such as traffic inspection, threat prevention, and application control without the need for on-premises hardware.
How does FWaaS work?
Firewall as a service works by transplanting the traditional firewall model into a cloud environment.
Instead of relying on physical hardware, FWaaS is a type of firewall setup that uses cloud infrastructure to deliver firewall capabilities. This setup provides a flexible, scalable, efficient way to protect incoming and outgoing network traffic.
Like this:
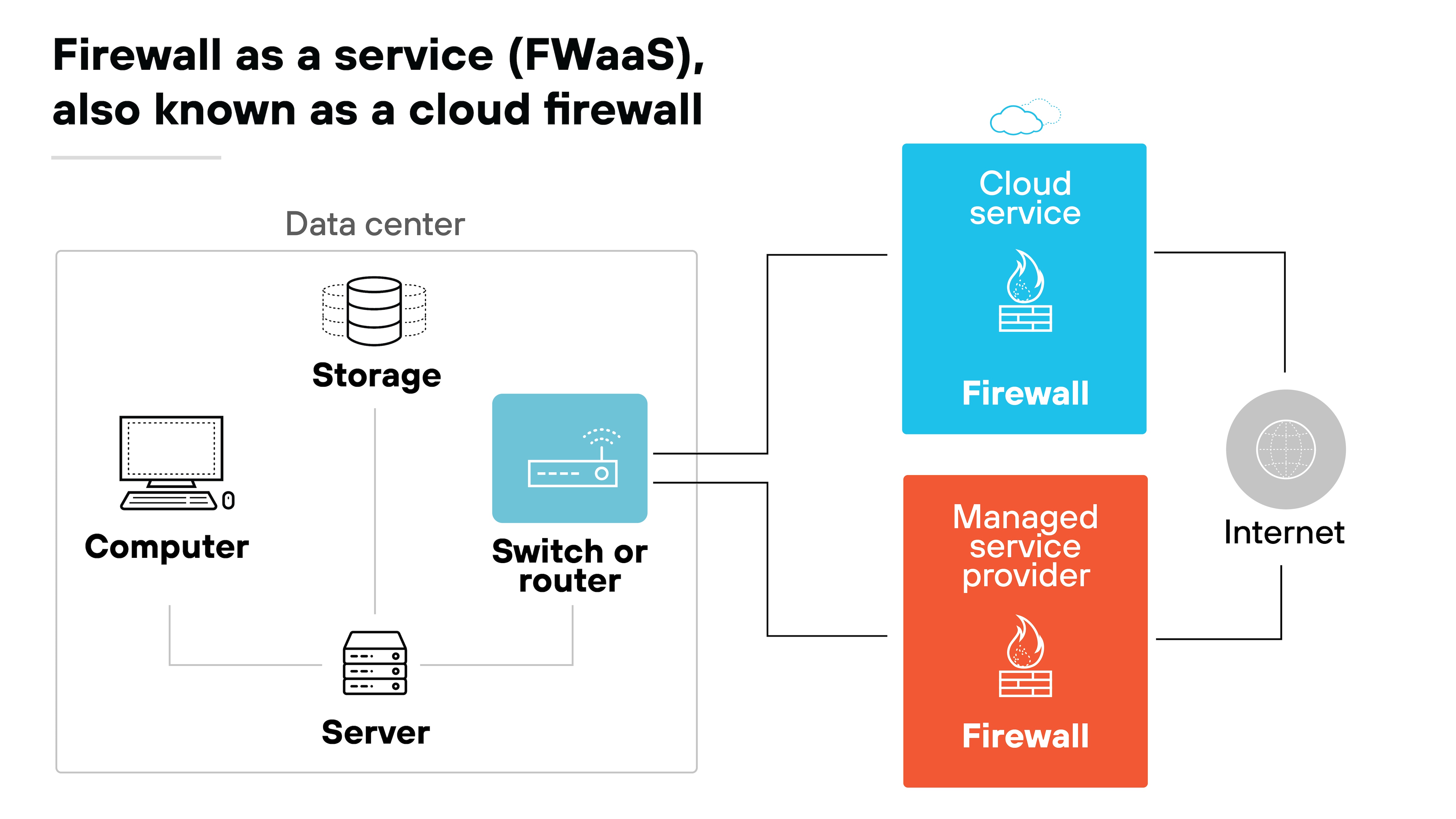
In essence, FWaaS acts as a proxy firewall within the cloud. Third-party providers create a cloud environment capable of hosting numerous firewall implementations. Each customer gets a virtually isolated section, ensuring their data and activities remain secure and private.
The process begins with the provider setting up an FWaaS instance for the customer. Which includes creating a configuration panel where customers can define their firewall rules.
Customers can set filtering criteria, app-specific controls, DNS options, and other custom settings to match their security needs.
Once configured, customers route their local network traffic through this virtual firewall.
The cloud firewall stands between the company’s assets and the wider internet, establishing robust protection against external threats.
This setup tends to work especially well for organizations with multiple branch offices. Users can connect from anywhere, but the security policies enforced by the FWaaS apply uniformly. And that ensures consistent protection, regardless of the user's location.
Why is FWaaS important?
FWaaS is important because businesses need it to secure modern, distributed networks effectively. It offers the flexibility, scalability, and centralized management required to protect against emerging threats and ensure consistent security across all environments.
Considering the rise of cloud computing, remote work, and mobile devices, it’s well established that traditional network perimeters have become obsolete.
Businesses need FWaaS to address the challenges that come along with the modern way of doing business, technologically speaking.
Basically, traditional firewalls were designed for static, on-premises networks. And that makes them ineffective for protecting today's dynamic, distributed network environments.
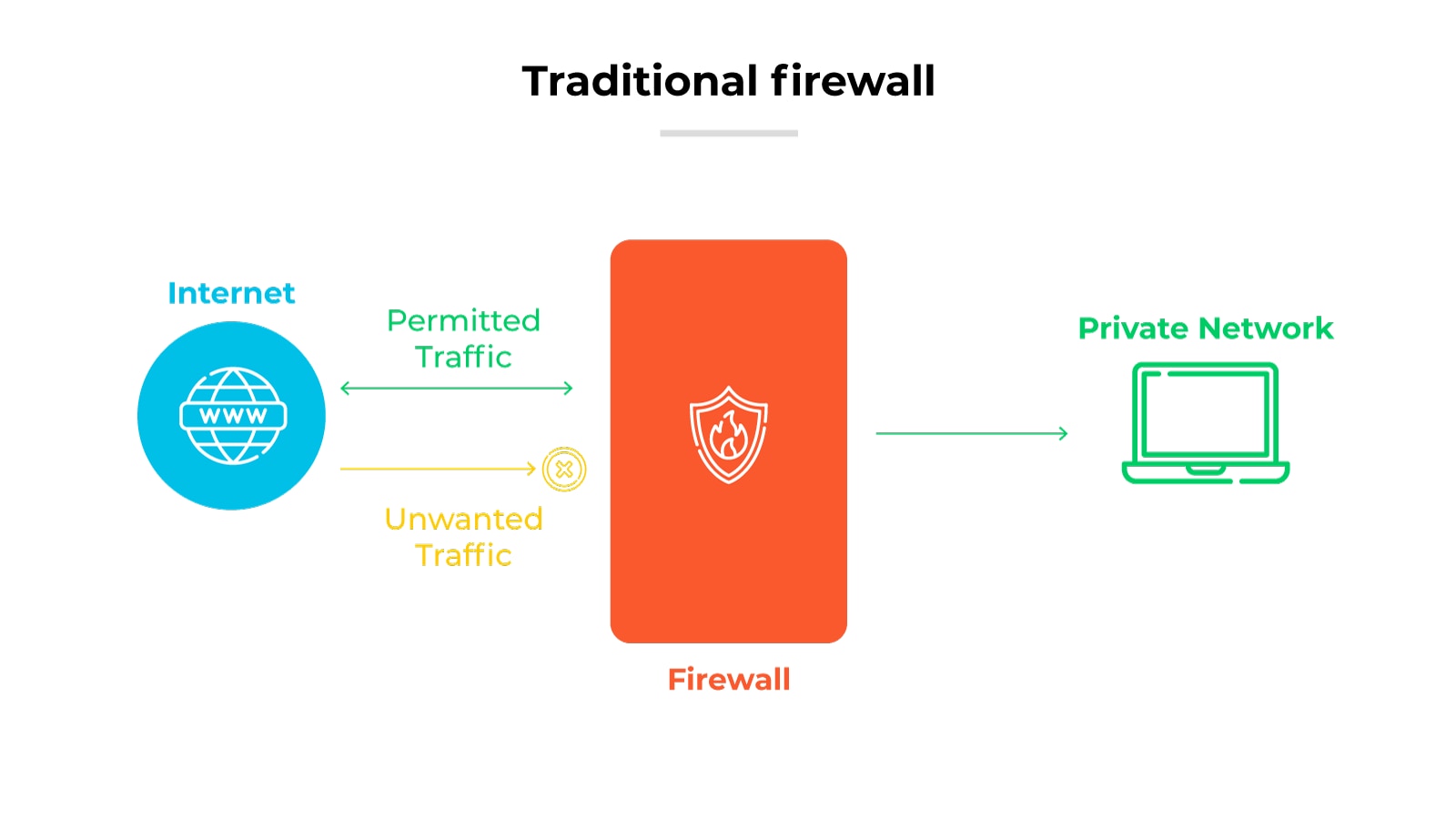
FWaaS provides the flexibility and scalability that modern businesses really need. As companies continue to adopt cloud services, maintaining consistent security across all locations and devices is becoming critical.
Conveniently, FWaaS centralizes firewall management. Which makes it way easier to enforce security policies uniformly and reduce the risk of security gaps.
Plus, FWaaS makes network security management way easier. Because it offloads routine maintenance and updates to the service provider. And that allows internal IT teams to focus on more strategic projects.
Meanwhile, firewalls are always up, running, and up-to-date. Given how volatile today’s threat landscape is, taking a proactive approach to network security is key.
What are the primary features of FWaaS?
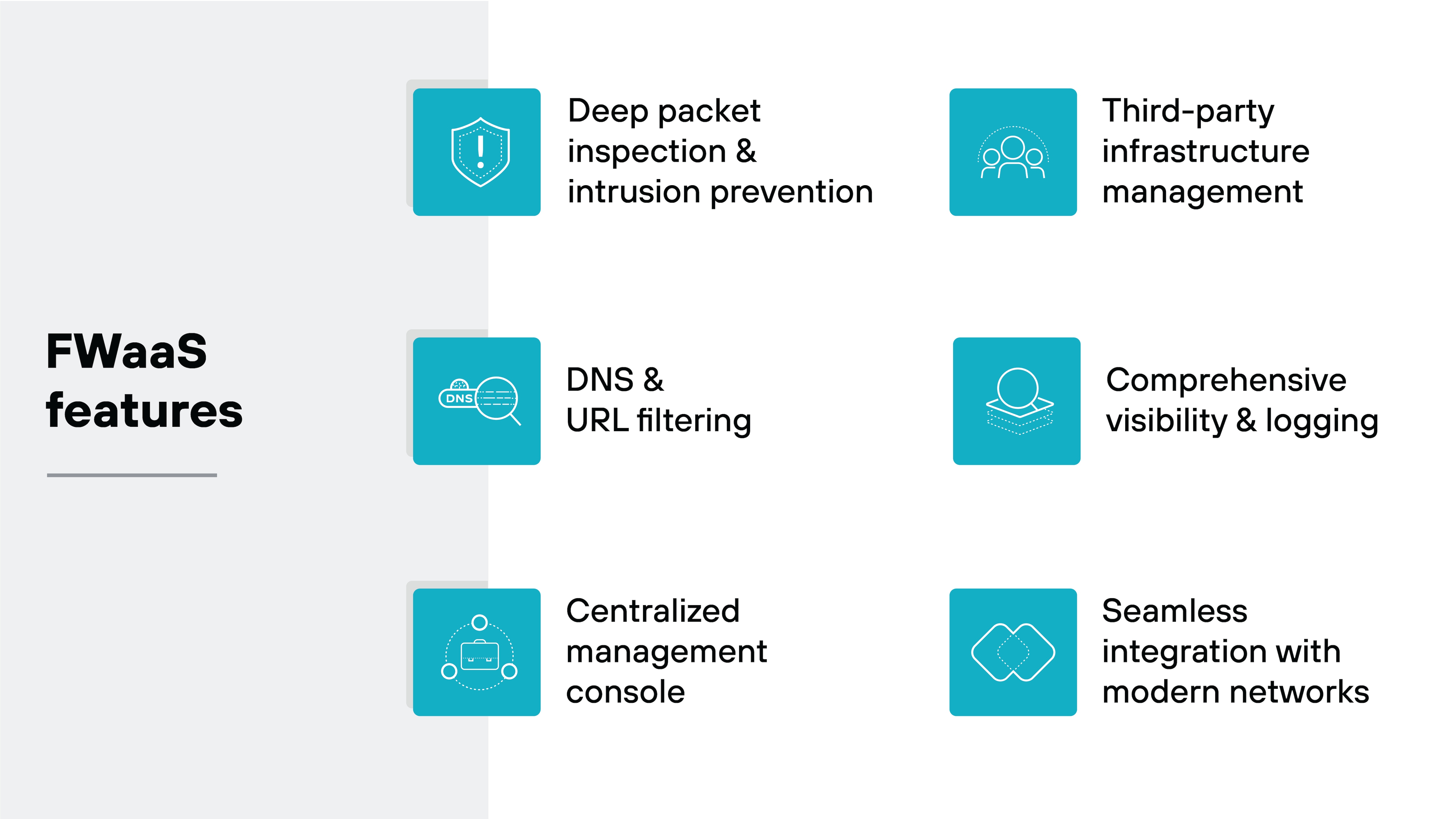
FWaaS offers a range of features that enhance security, simplify management, and provide scalability for modern organizations, including:
Deep packet inspection
Intrusion prevention
DNS and URL filtering
Centralized management consoles
Comprehensive visibility and logging
Instant scalability
Third-party infrastructure management
Seamless integration with modern networks
Let’s dive into the details.
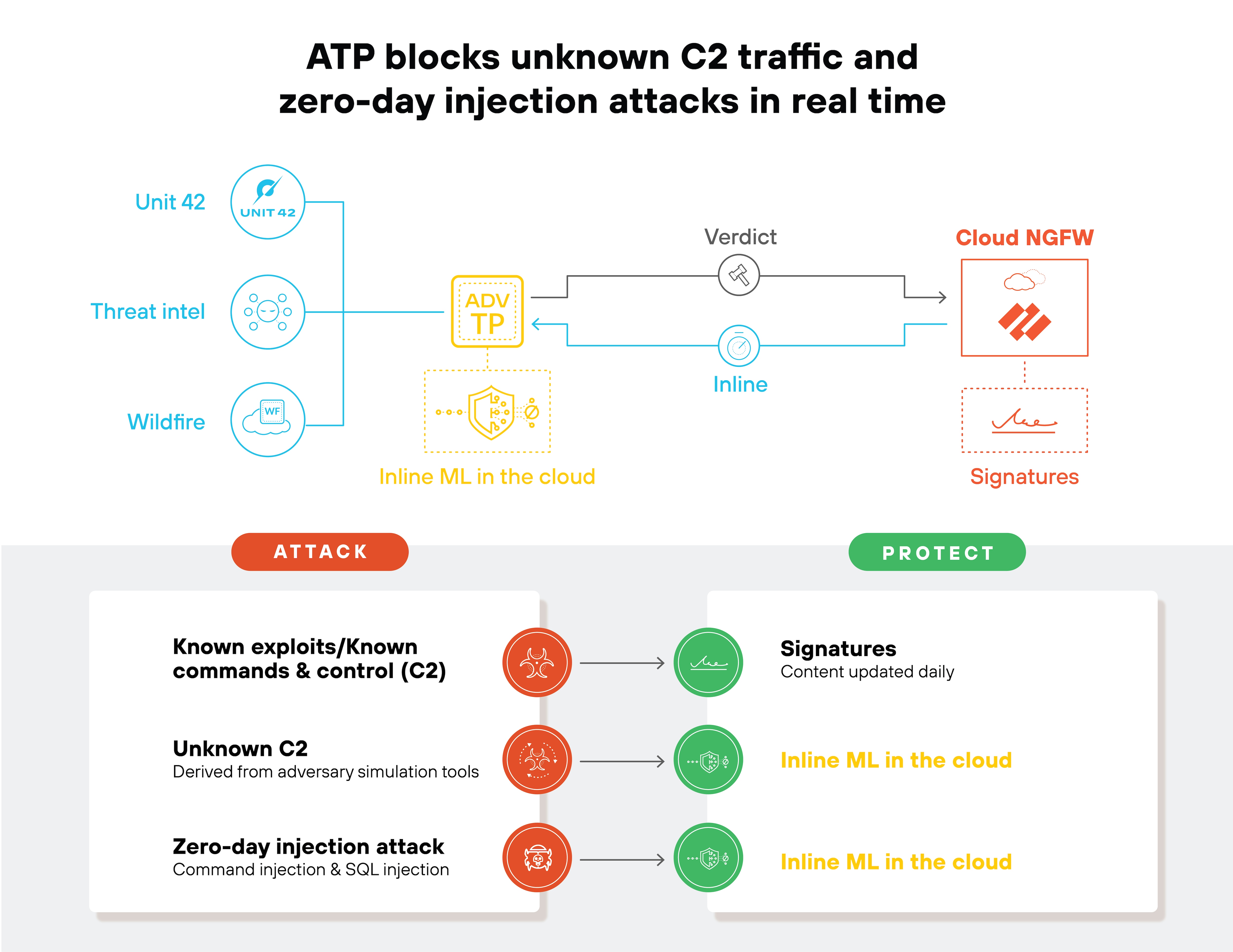
Deep packet inspection and intrusion prevention
FWaaS includes deep packet inspection (DPI) and intrusion prevention systems (IPS) as key security tools.
DPI examines the contents of data packets, including SSL-encrypted traffic, to detect and block threats.
IPS tools further enhance security by identifying and preventing intrusions in real-time.
For example:
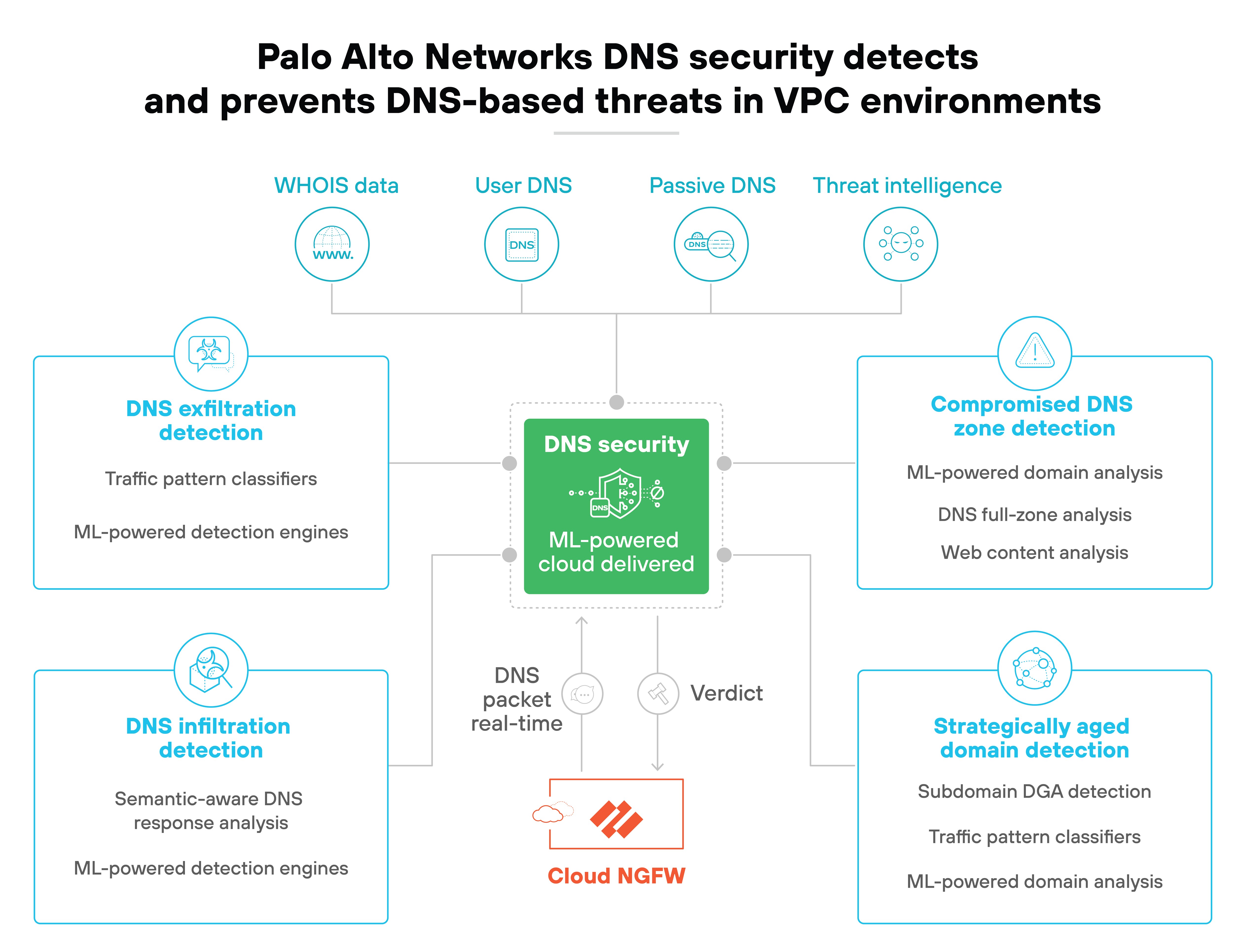
DNS and URL filtering
DNS and URL filtering are also essential features of FWaaS.
These tools control access to malicious sites by filtering domain names and URLs. This adds an extra layer of protection, preventing users from accessing harmful websites.
For instance, here’s how DNS security is delivered to Palo Alto Networks Cloud NGFW resources:
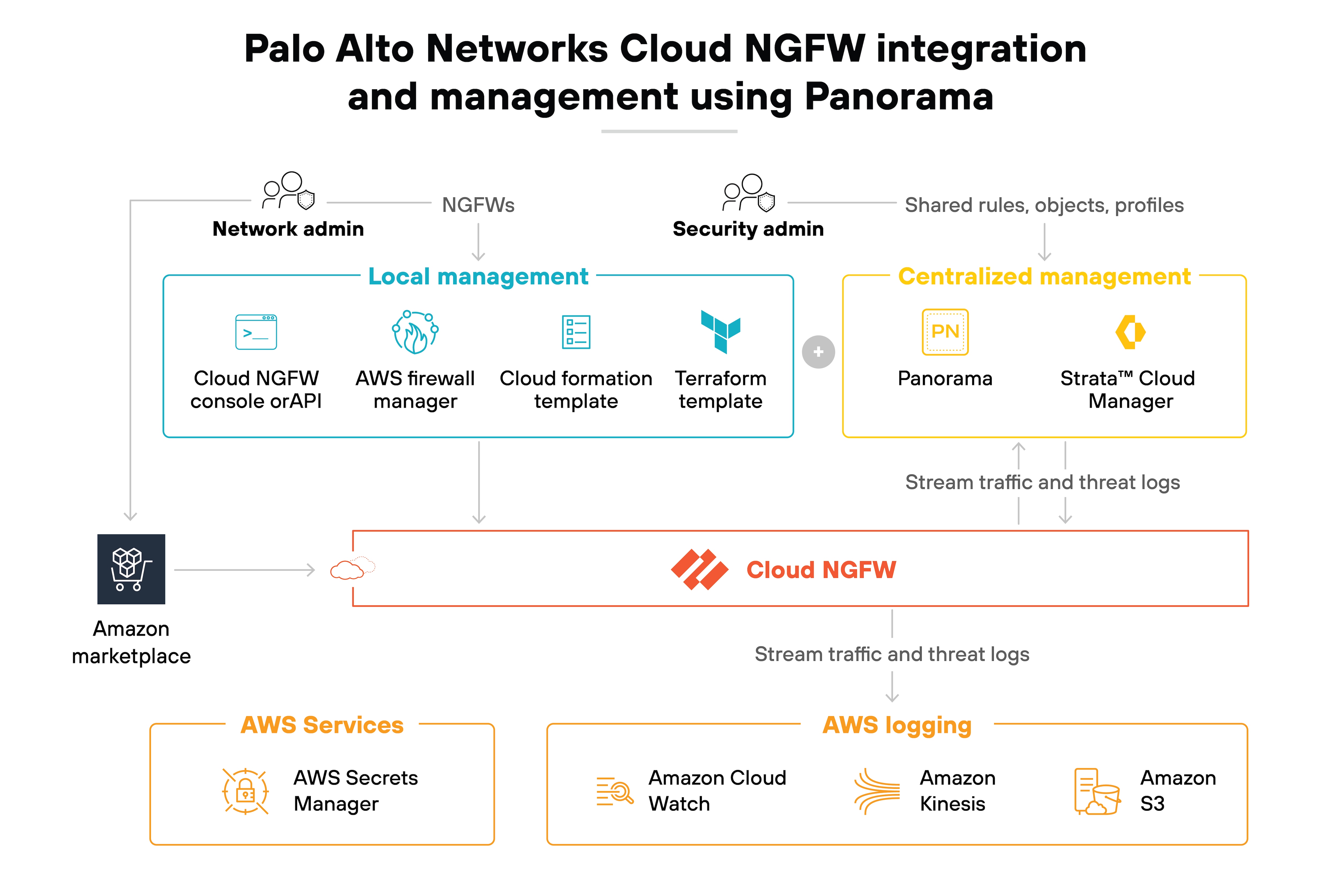
Centralized management console
A key feature of FWaaS is the centralized management console.
The single pane of glass allows admins to control filters, access settings, and distribute security policies across all endpoints from one location.
As explained, centralization makes management a lot simpler. And ensures consistent security policy enforcement.
Most FWaaS vendors offer centralized management systems that provide visibility and control over NGFWs. Customers can usually follow a simple configuration and integration process to integrate the FWaaS solution with the management tool.
Like so:
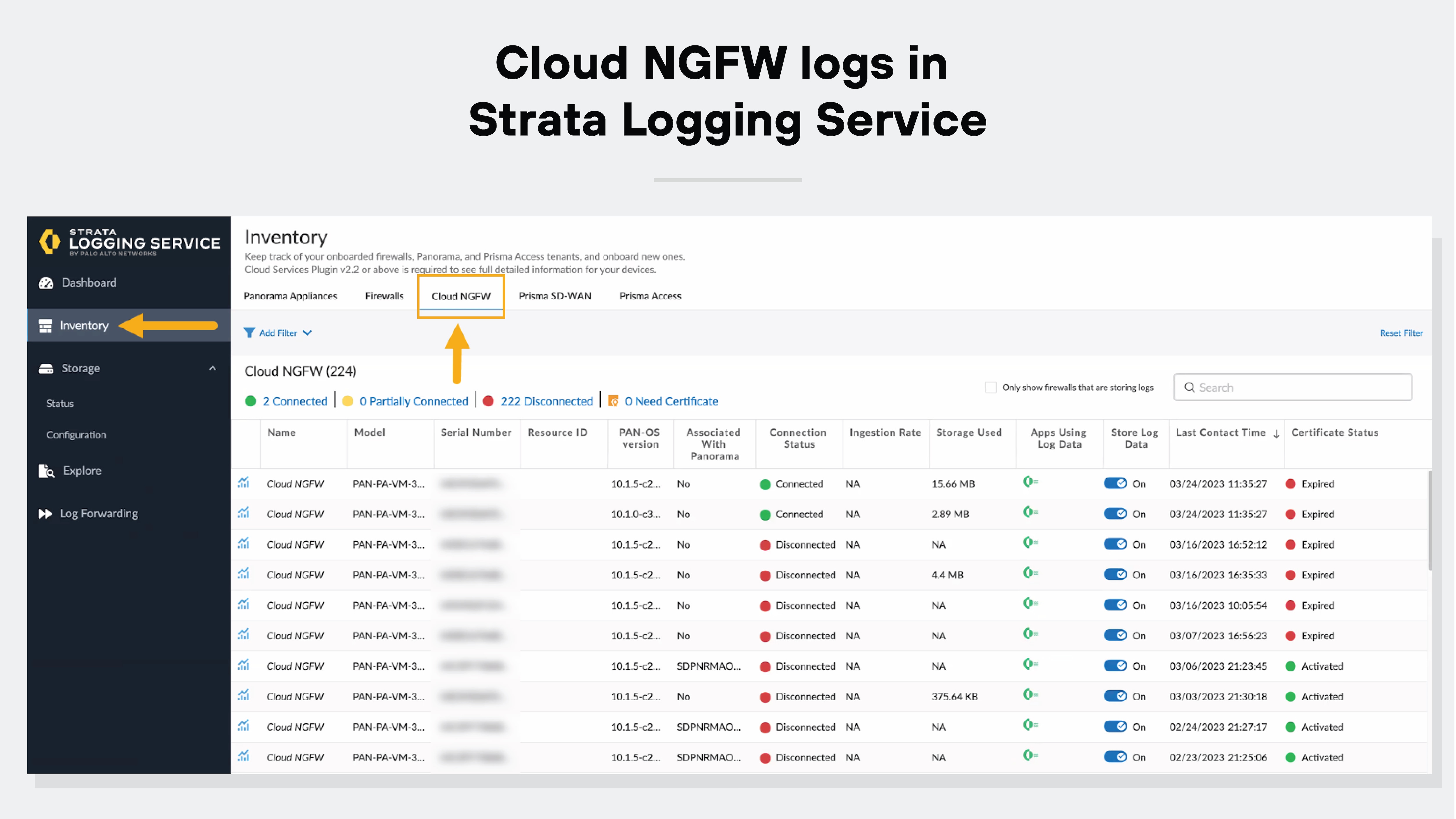
Comprehensive visibility and logging
FWaaS provides detailed visibility and logging capabilities.
Logging systems track all network activity and usually integrate easily with cloud security information and event management (SIEM) technology. This provides a thorough record of network events and facilitates quick identification of potential security issues.
Here’s what logging might look like:
Third-party infrastructure management
FWaaS relies on third-party infrastructure management to ensure high levels of reliability–not to mention reduce the workload on network and IT personnel.
Specialized cloud firewall providers handle the infrastructure, maintenance, and updates. Again, this frees up internal resources to focus on other critical security tasks.
This way, the firewall stays up-to-date with the latest security patches and enhancements.
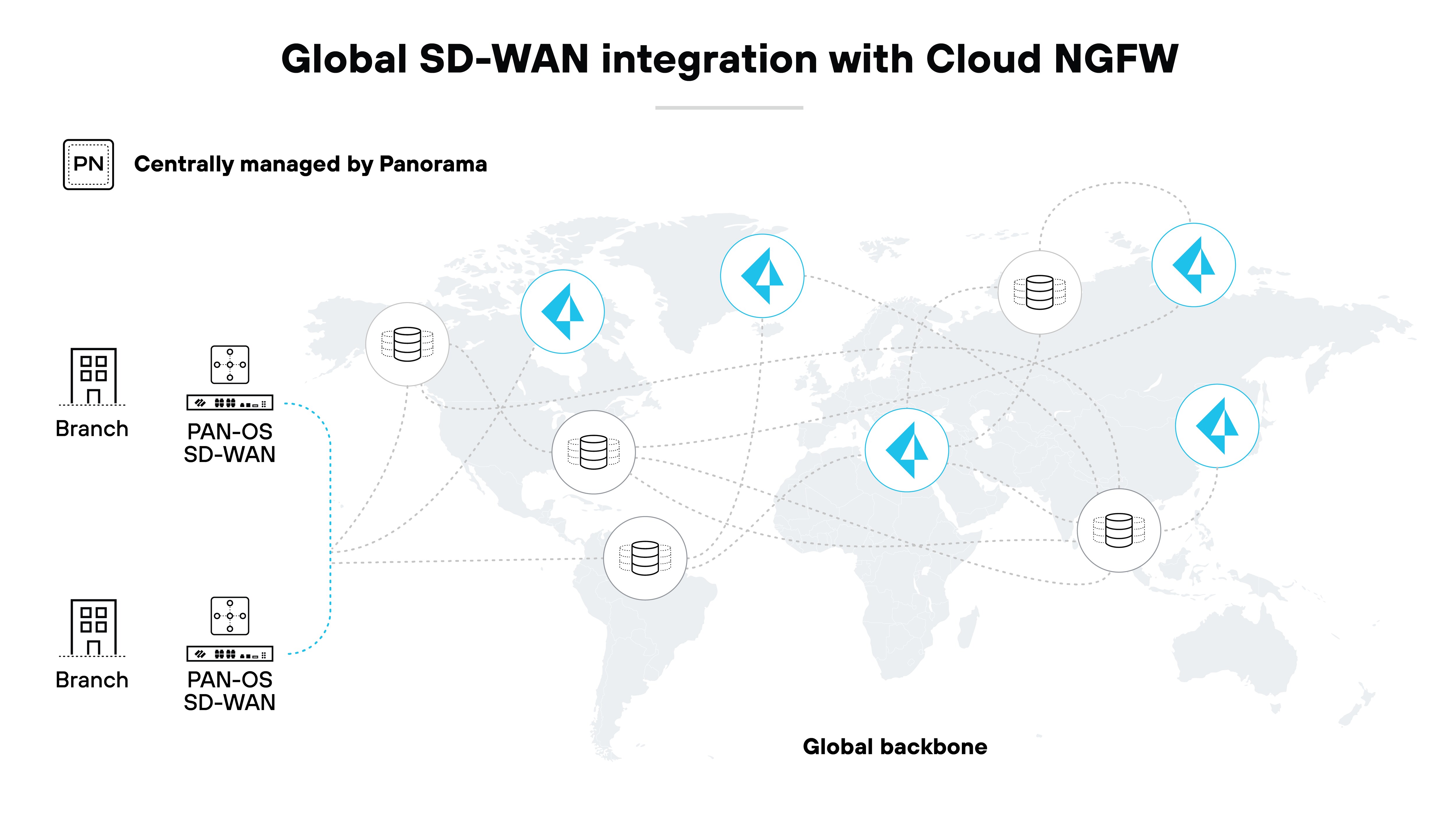
Seamless integration with modern networks
FWaaS is designed to integrate seamlessly with modern network architectures, including software-defined networks (SDNs) and wide area networks (SD-WANs).
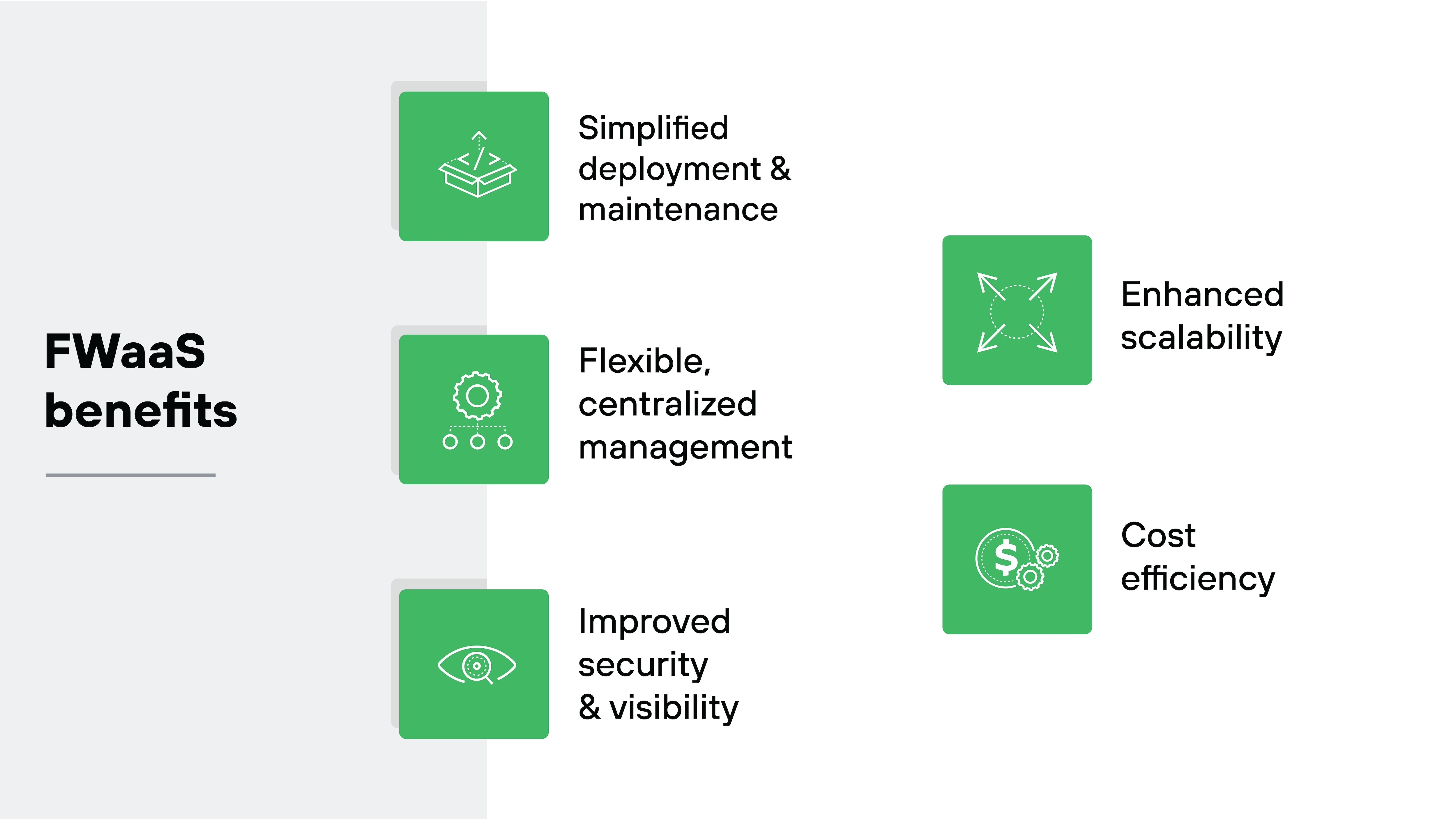
FWaaS offers numerous benefits, including:
Simplified deployment and management
Enhanced scalability
Improved security and visibility
Flexible and centralized management
Cost efficiency
These benefits make firewall as a service an attractive option for organizations looking to bolster their security posture while maintaining flexibility and controlling costs.
Simplified deployment and maintenance
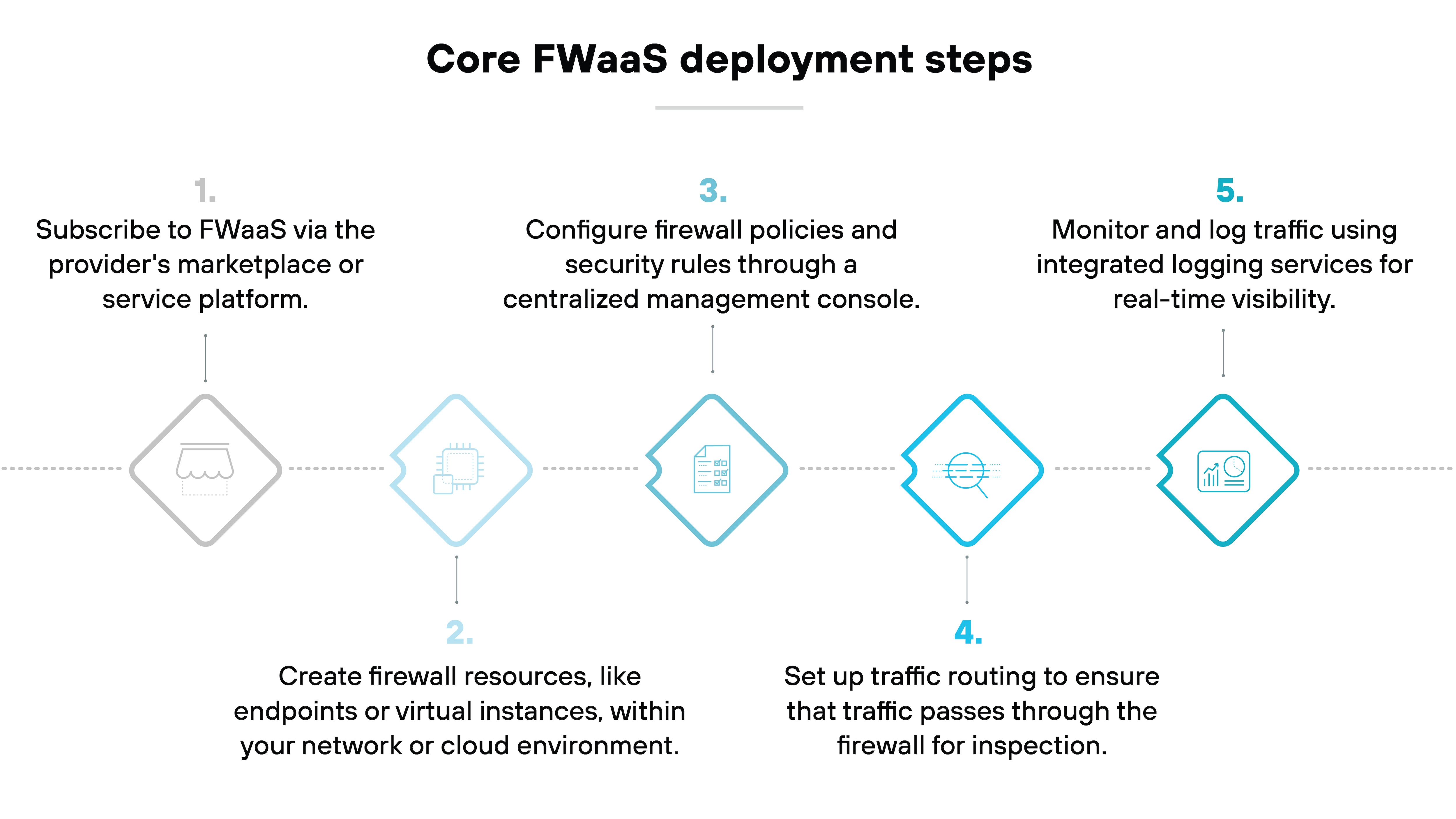
One of the most compelling benefits of FWaaS is how easy most solutions are to deploy and maintain.
Typical firewalls require lots of time and resources to set up and maintain. But FWaaS simplifies this process by offloading the heavy lifting to the service provider.
Instant scalability
The ability to scale instantly is a standout feature of FWaaS.
Customers can expand their cloud firewall coverage rapidly by purchasing additional capacity without the need for new hardware.
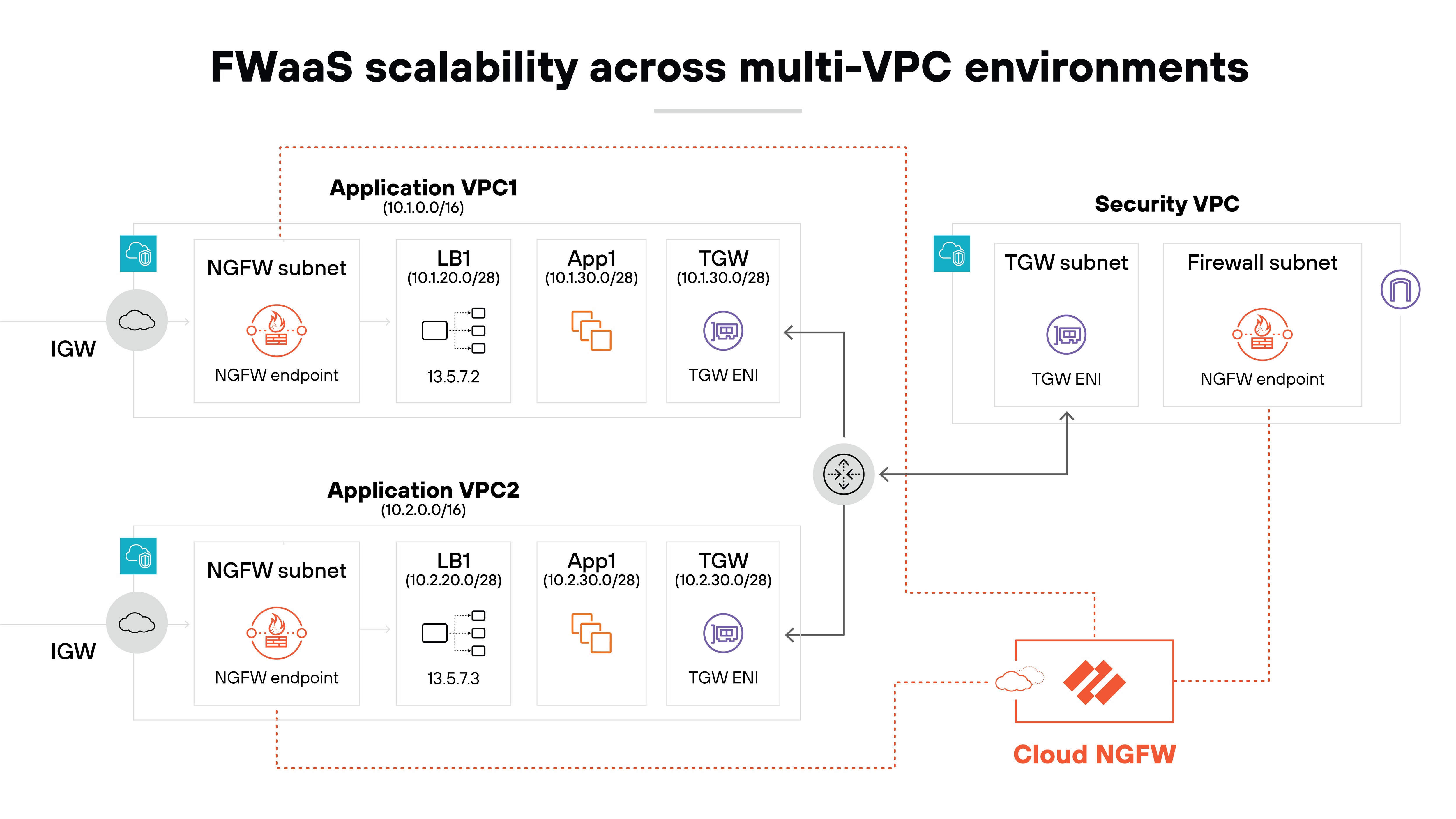
This is especially useful because it means that security measures can grow alongside the business. The FWaaS model is easy to adapt when there’s increased traffic or additional security requirements.
Improved security and visibility
As established, FWaaS provides enhanced security features and visibility into network traffic.
FWaaS offerings often include advanced threat detection capabilities, like deep packet inspection and intrusion prevention systems (IPS). Which makes it possible to identify and mitigate threats in real-time.
Not to mention, with firewall as a service, you typically have visibility into all traffic. Including SSL/TLS-encrypted traffic. So no potential threats go unnoticed.
Flexible, centralized management
Managing network security is hard and complex. Especially for organizations with multiple locations or remote workers.
As explained, the flexible, centralized management that FWaaS offers via management consoles majorly simplifies this process.
Cost efficiency
Cost is a critical consideration for all organizations. And FWaaS does provide a notably cost-effective alternative to traditional firewall solutions for the right candidates.
With FWaaS, there’s no need to invest in expensive hardware. As noted, the service is typically offered on a subscription basis, which means capital expenditures (CAPEX) become operating expenditures (OPEX).
Also, since the service provider handles maintenance, organizations do tend to save on the costs associated with maintaining and upgrading hardware.
The shift to a more predictable, manageable cost structure can significantly benefit the bottom line.
What are the potential challenges of FWaaS?
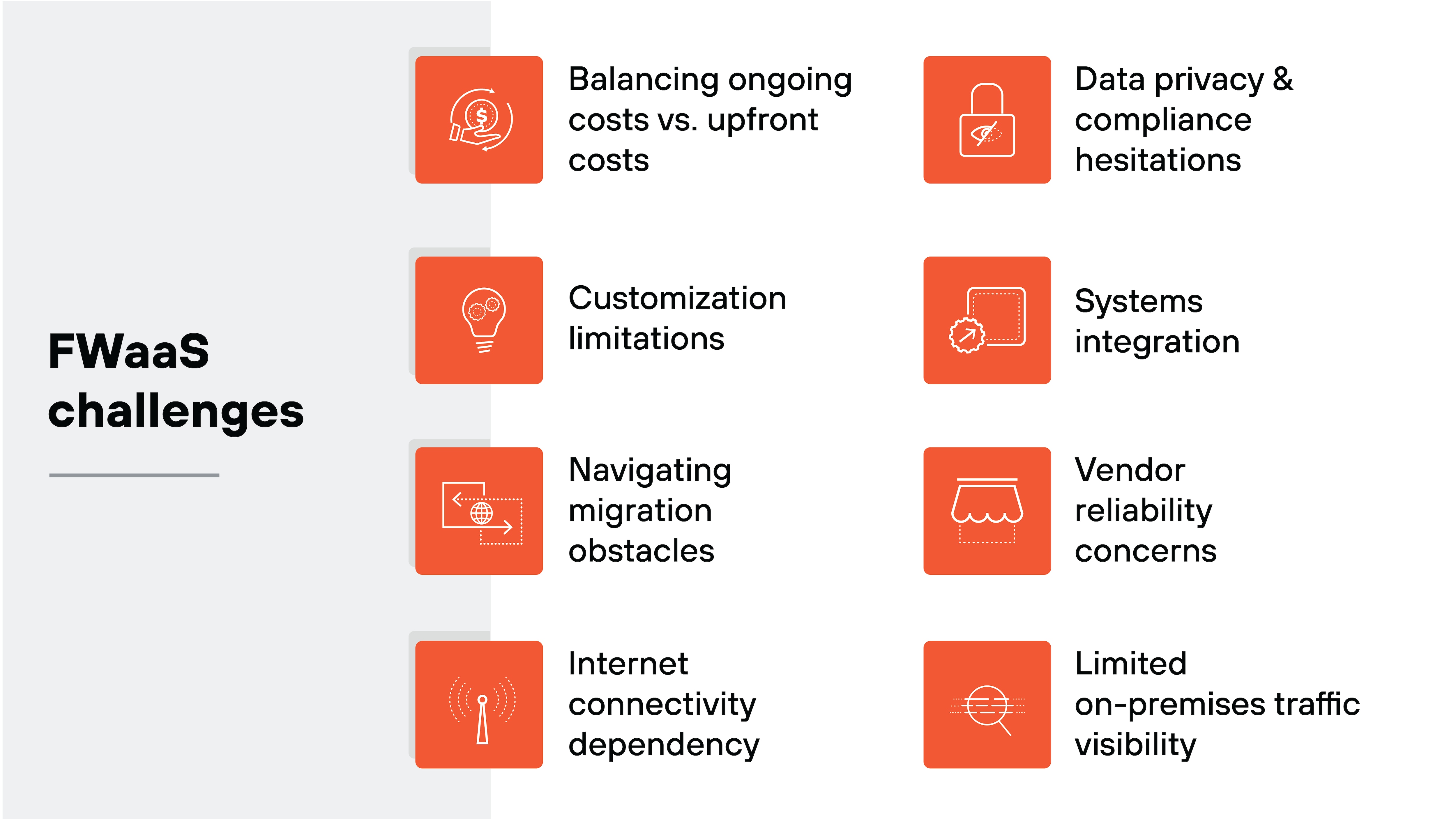
While FWaaS offers many advantages, as with all technologies, there are also potential challenges that organizations need to consider.
It’s worth noting, though, that although FWaaS does present a handful of potential challenges, each can be effectively mitigated with careful planning and collaboration with your service provider.
Balancing ongoing costs vs. upfront costs
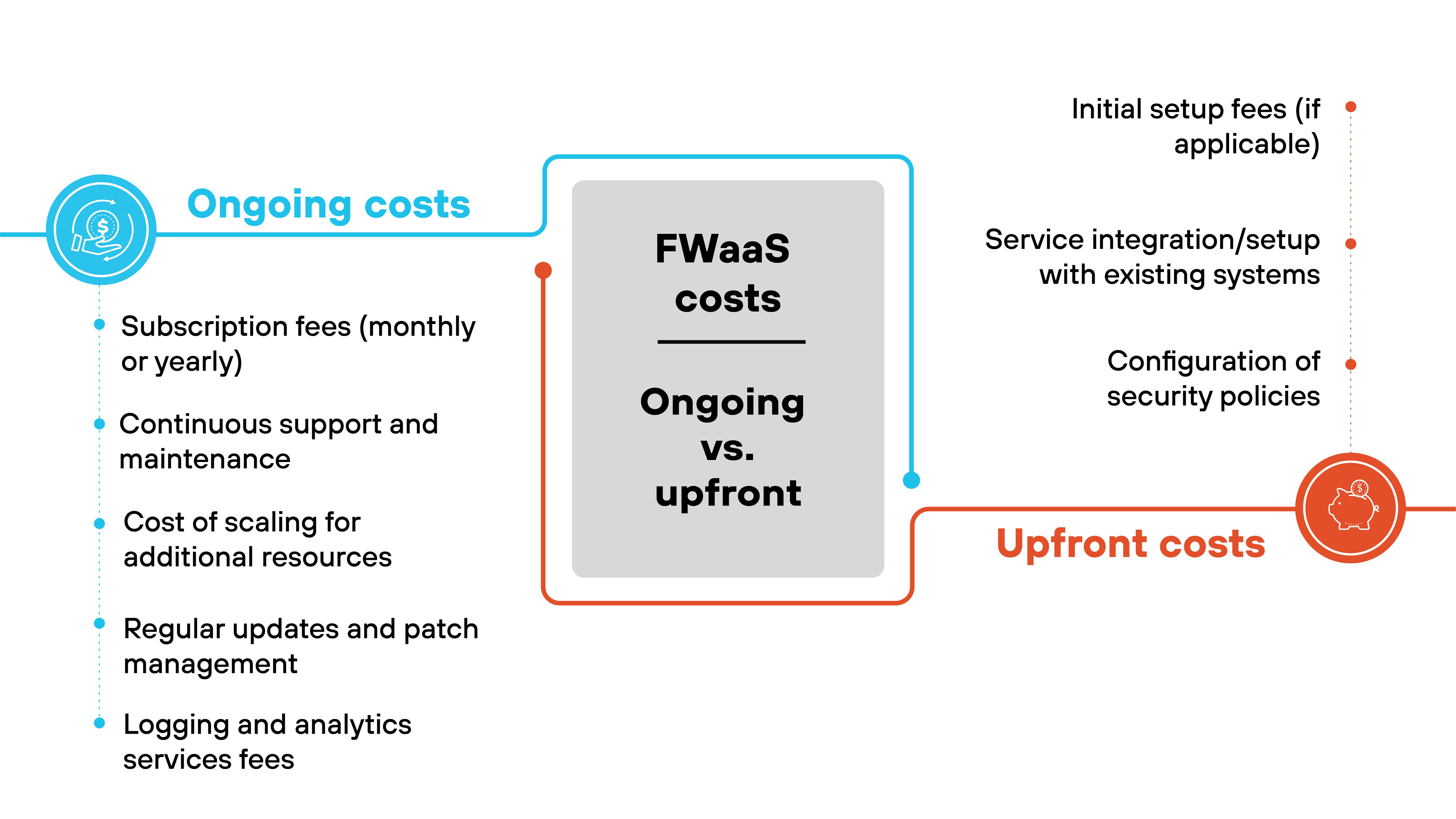
While it’s true that FWaaS generally removes the need for upfront hardware investments, it also comes with ongoing subscription fees.
For some organizations, these recurring costs may eventually outweigh the initial investment required for traditional firewalls.
Be sure to carefully evaluate the total cost of ownership in advance. Consider the long-term benefits, like reduced maintenance and management overhead, which can offset the subscription costs.
Customization limitations
Unlike regular firewalls, FWaaS can limit customization.
This can be tricky for organizations with unique security needs or complex network setups. Out-of-the-box settings might not fit your specific requirements.
Work closely with your FWaaS provider to understand the customization options available.
Navigating migration obstacles
Depending on your objectives, implementing FWaaS can involve modifying existing network structures and configurations.
If you’re migrating from traditional firewalls, the process might require network security personnel to acquire new skills and adapt to new systems.
Fortunately, planning the migration carefully can help mitigate this challenge. Work with your FWaaS provider closely to be sure the transition is a smooth one.
Internet connectivity dependency
FWaaS depends heavily on a stable internet connection. If your organization faces internet slowdowns or outages, your network security could be at risk.
This can pose a problem for businesses in areas with unreliable internet access.
Data privacy and compliance hesitations
Sending network traffic through third-party cloud servers may lead to concerns about privacy and meeting compliance requirements.
If your organization handles sensitive data, you might hesitate for fear of potential exposure to data breaches.
Fortunately, FWaaS providers are generally in the network security business, and most offer strong data privacy policies and compliance attestations as a result.
Choose a FWaaS vendor with compelling data privacy measures to alleviate these concerns.
Systems integration
If your infrastructure includes older equipment, bringing FWaaS into the current network environment can pose challenges.
Engage with your FWaaS provider heavily during the planning phase, and be sure the solution is compatible with your current systems. Explore custom development if needed.
Proper planning will lessen the chance of disruptions, and potential security vulnerabilities.
Vendor reliability concerns
How effective your FWaaS solution is really depends on the reliability of the vendor.
These sorts of vendor issues could leave your network exposed to potential risks:
Service outages
Security breaches
Inconsistent or delayed updates
Limited or slow customer support
Weak SLAs

Vet potential vendors thoroughly. Check their track record, customer reviews, and security measures. A reliable vendor will have transparent policies and strong infrastructure.
Limited on-premises traffic visibility
Traditional firewalls inspect network traffic locally—directly on-site.
In contrast, FWaaS conducts traffic inspection in the cloud. This approach might limit your visibility into activity occurring within your local network, depending on the solution you choose.
Using a hybrid approach if necessary can address this challenge. Combine FWaaS with local inspection tools to ensure comprehensive visibility and threat detection within your network.
How much does FWaaS cost?
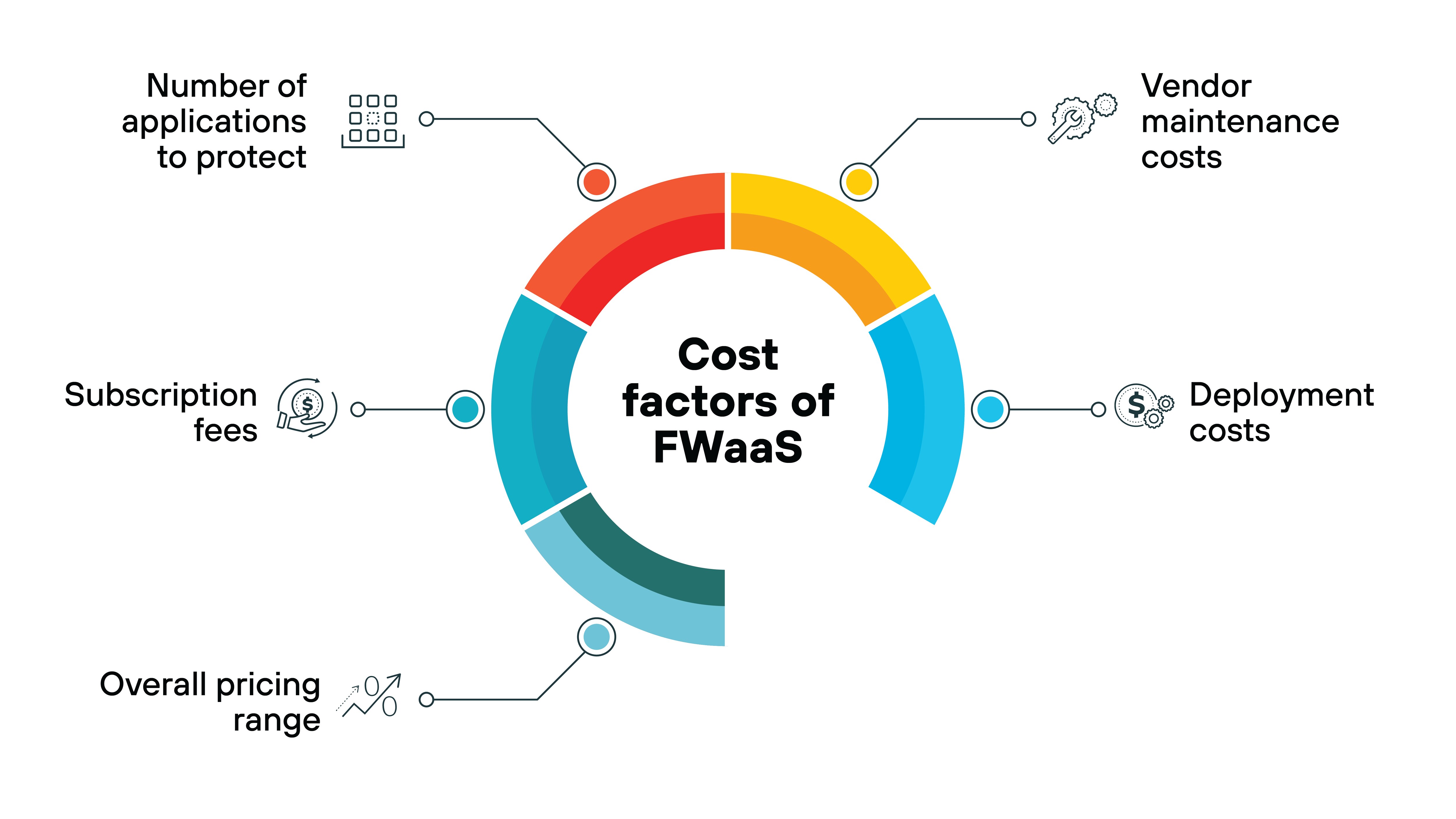
Ultimately, firewall as a service costs can vary widely depending on several factors, including:
- Number of applications to protect: The more applications that require protection, the higher the cost.
- Subscription fees: Ongoing fees that are charged by the provider for using the FWaaS solution.
- Provider maintenance costs: Costs associated with the maintenance and management performed by the provider.
- Deployment costs: Costs related to the initial deployment of the FWaaS solution.
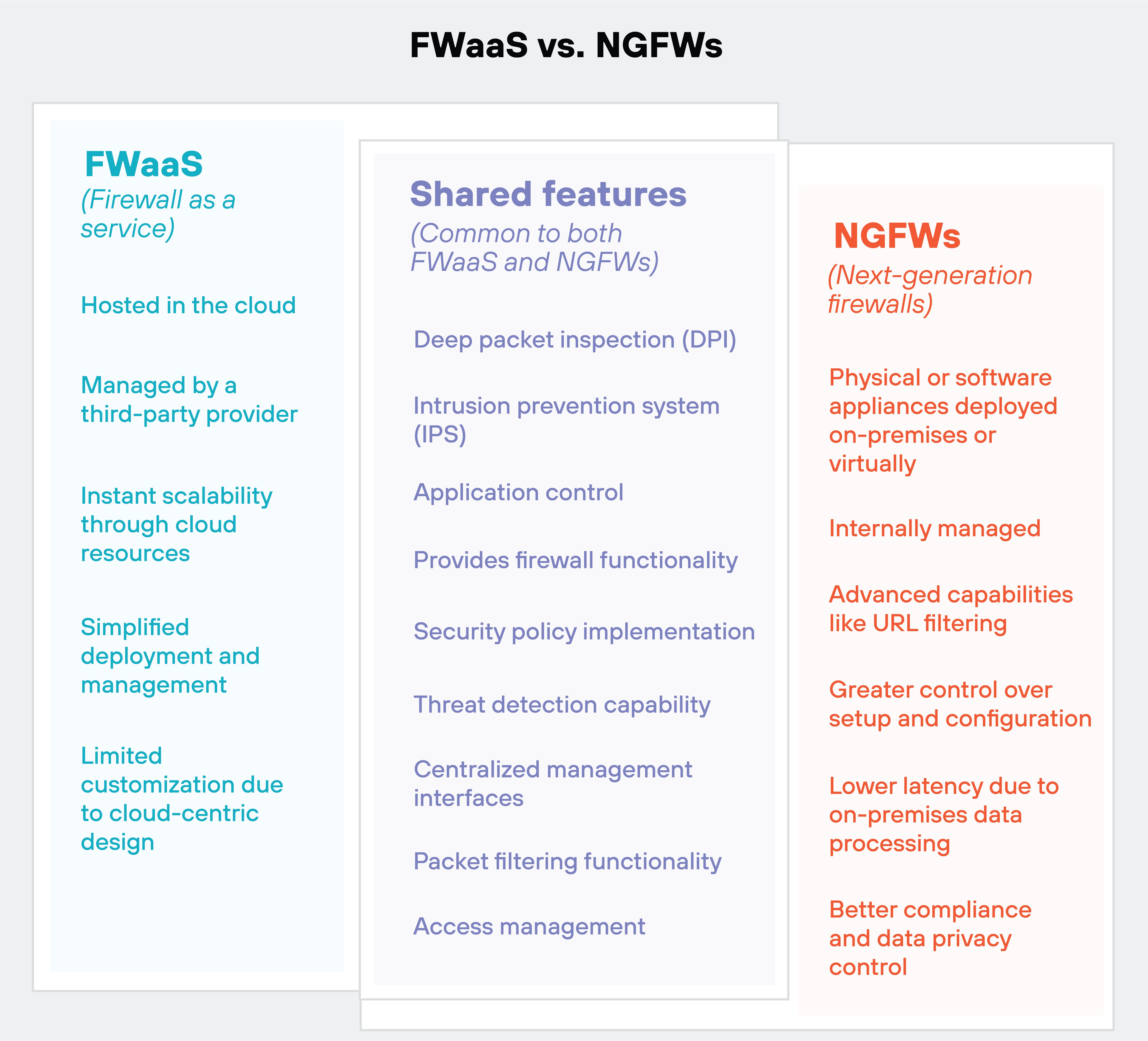
FWaaS and next-generation firewalls (NGFWs) are two distinct firewall variations, each designed to meet different needs and serve different purposes.
Overall, FWaaS provides a scalable, managed solution that works well for organizations looking for ease of deployment and management.
NGFWs offer advanced security features and greater customization, making them suitable for organizations with specific security needs and the resources to manage them.
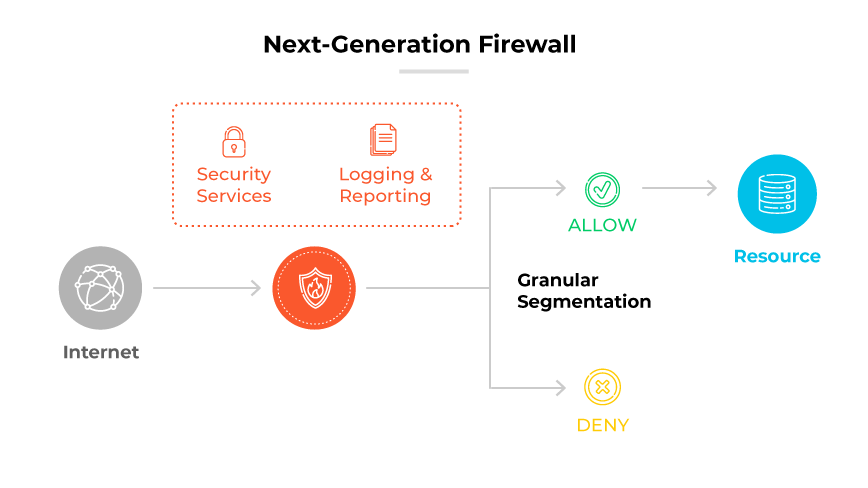
Deployment approach
FWaaS is a cloud-based service that provides firewall functionality as part of a cloud computing environment.
It operates through cloud-based management, often by a third-party provider (though not always), making it accessible from anywhere with internet connectivity.
On the other hand, NGFWs are physical or software appliances that are deployed either on-premises or virtually. This standard approach can be more complex and requires on-site hardware or software installations.
Management structure
One of the main distinctions between FWaaS and NGFWs is the management structures.
FWaaS is managed externally by a provider using web interfaces or APIs. The provider handles updates, maintenance, and scaling, allowing your network security to focus on other work.
NGFWs, however, are internally managed, offering greater control over setup and configuration. This control can be beneficial for organizations with specific security requirements, but it also requires more resources and expertise to maintain.
Functional range
FWaaS offers fundamental firewall features along with limited supplementary security services. This makes it suitable for organizations looking for a straightforward, scalable security solution.
In contrast, NGFWs provide advanced capabilities such as deep packet inspection (DPI), intrusion prevention systems (IPS), URL filtering, and application-level controls. These features make NGFWs a better option for organizations that need comprehensive security measures.
Customization options
Customization is another area where FWaaS and NGFWs differ.
FWaaS solutions tend to offer limited customization due to the cloud-centric design. This can be seen as a limitation for organizations with unique security needs.
NGFWs allow more tailored customization for security policies, providing flexibility to adjust settings based on specific organizational requirements.
Scalability
Scalability is a major advantage of FWaaS.
It achieves scalability through cloud resources and infrastructure, allowing organizations to quickly adjust their security measures as their needs grow. This is particularly useful for businesses with fluctuating security demands.
NGFWs' are equally scalable, but the actual process depends on available hardware and resources, making it more involved and labor intensive.
Cause of latency
When considering performance, some FWaaS solutions can introduce potential latency due to reliance on cloud-based processing. This might be a concern for organizations requiring high-speed data processing.
In contrast, NGFWs demonstrate lower latency because data processing happens within the organization’s premises, providing faster response times.
Compliance and data privacy implications
Data privacy and compliance are crucial considerations.
FWaaS has a tendency to raise data privacy concerns with some because network traffic is routed through third-party cloud servers. This can be a perceived issue for organizations handling sensitive data.
However, as established, FWaaS vendors are in the network security business by nature. Typically data privacy and compliance concerns can be allayed through a simple conversation with the vendor.
One could argue that NGFWs provide better control over compliance since data is processed within the organization’s environment. To some, this is an assurance that privacy and regulatory requirements are more easily met.
But again, data privacy and compliance have more to do with the vendor than the firewall variation.
What is the role of FWaaS in the SASE framework?
FWaaS plays a crucial role within the secure access service edge (SASE) framework.
SASE is a cloud-based networking architecture that combines software-defined WAN (SD-WAN) with a set of security services, including:
- FWaaS
- SWG
- CASB
- ZTNA
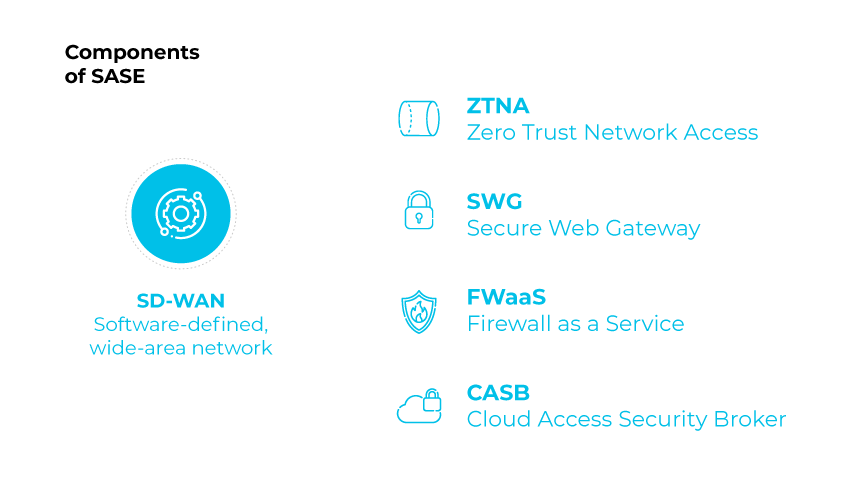
Together, these services create a unified security architecture that can protect all aspects of a network, regardless of where users or applications are located.
The integration provides comprehensive security and access control at the network edge, moving away from traditional on-premises data center perimeters.
Like this:
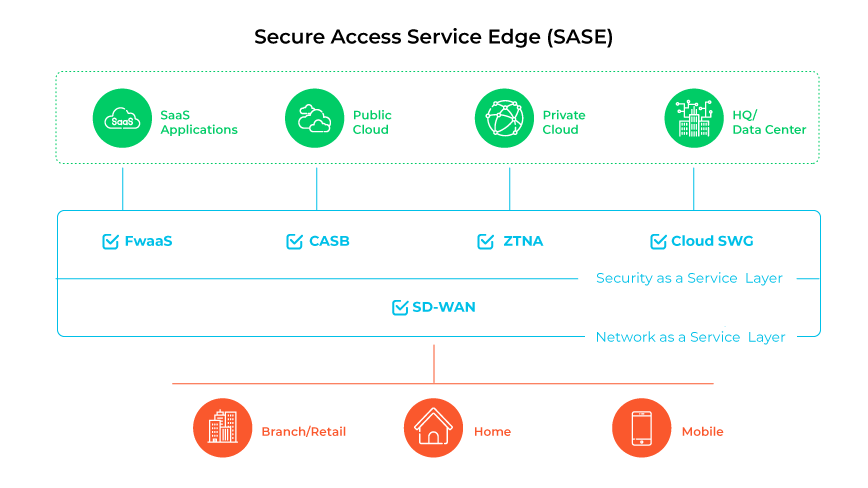
FWaaS is integral to the SASE framework because it provides cloud-native firewall capabilities. Which means it enforces security policies across all network traffic, regardless of user or application location.