- 1. How Does a Packet Filtering Firewall Work?
- 2. Packet Filtering Firewall Use Cases
- 3. Packet Filtering Firewall Benefits
- 4. Packet Filtering Firewall Challenges
- 5. Types of Packet Filtering Firewalls
- 6. Comparing Packet Filtering Firewalls with Other Security Technologies
- 7. Packet Filtering Firewall FAQs
What Is a Packet Filtering Firewall?
A packet filtering firewall is a network security device that filters incoming and outgoing network packets based on a predefined set of rules.
Rules are typically based on IP addresses, port numbers, and protocols. By inspecting packet headers, the firewall decides if it matches an allowed rule; if not, it blocks the packet. The process helps protect networks and manage traffic, but it does not inspect packet contents for potential threats.
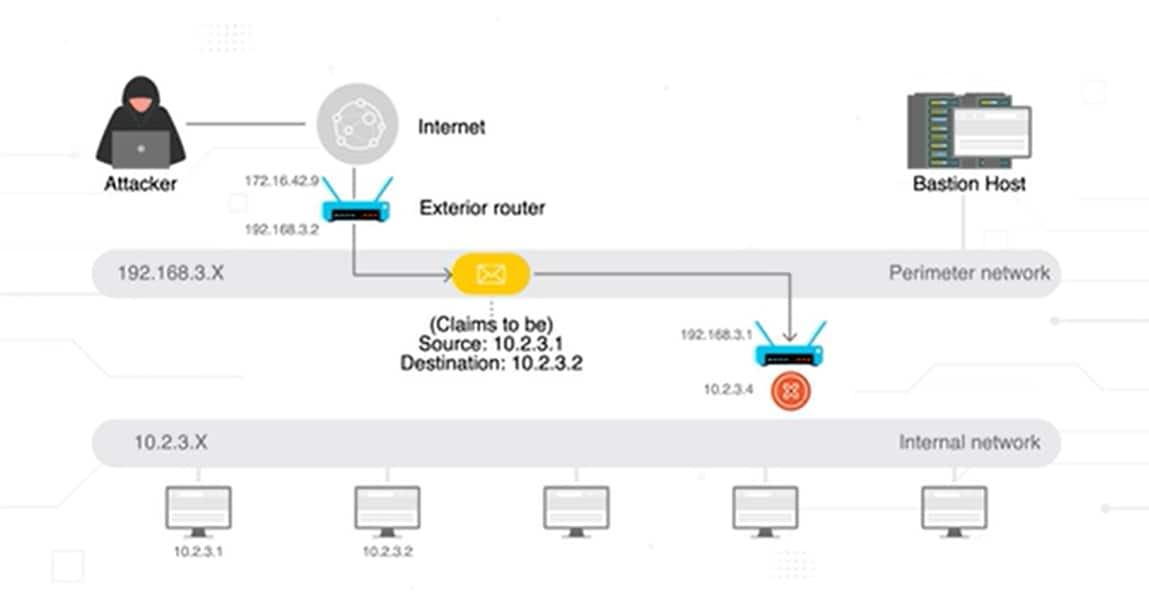
How Does a Packet Filtering Firewall Work?

This type of firewall operates at a fundamental level by applying a set of predetermined rules to each network packet that attempts to enter or leave the network. These rules are defined by the network administrator and are critical in maintaining the integrity and security of the network.
Packet filtering firewalls use two main components within each data packet to determine their legitimacy: the header and the payload.
The packet header includes the source and destination IP address, revealing the packet's origin and intended endpoint. Protocols such as TCP, UDP, and ICMP define rules of engagement for the packet's journey. Additionally, the firewall examines source and destination port numbers, which are similar to doors through which the data travels. Certain flags within the TCP header, like a connection request signal, are also inspected. The direction of the traffic (incoming or outgoing) and the specific network interface (NIC) the data is traversing, are factored into the firewall's decision making process.
Packet filtering firewalls can be configured to manage both inbound and outbound traffic, providing a bidirectional security mechanism. This ensures unauthorized access is prevented from external sources attempting to access the internal network, and internal threats trying to communicate outwards.
Packet Filtering Firewall Use Cases

A primary packet filtering firewall use case is the prevention of IP spoofing attacks, where the firewall examines the source IP addresses of incoming packets. By ensuring the packets originate from expected and trustworthy sources, the firewall can prevent attackers from masquerading as legitimate entities within the network. This is particularly important for perimeter defenses.
In addition to security, packet filtering firewalls are used to manage and streamline network traffic flow. By setting up rules that reflect network policies, these firewalls can limit traffic between different subnets within the enterprise. Limiting traffic between different subnets helps contain potential breaches and segment network resources according to departmental needs or sensitivity levels.
Another use case for packet filtering firewalls is scenarios where speed and resource efficiency are valued. Due to their less computationally intensive nature, packet filtering firewalls can quickly process traffic without significant overhead.
Packet Filtering Firewall Benefits
High Speed Efficiency
One of the main benefits of packet filtering firewalls is their ability to make quick decisions. By operating at the network layer, they rapidly accept or reject packets based on set rules without the need for deep packet inspection. This results in very fast processing, allowing for efficient network traffic flow and reduced chances of bottlenecks.
Transparent Operation
Packet filtering firewalls are designed to be transparent to the end user. They operate autonomously, applying rules to network traffic without requiring user intervention or notification unless a packet is dropped. The transparency ensures network security measures do not impede the user experience or require extensive training for the end users.
Cost Efficiency
Packet filtering firewalls are cost efficient. They often come integrated into network routers, which eliminates the need for separate firewall devices.
Initial Simplicity and Ease of Use
Ease of use was once thought to be an advantage of packet filtering firewalls. They do not typically require complex setup.
Packet Filtering Firewall Challenges
Limited Logging Capabilities
One of the significant disadvantages of packet filtering firewalls is limited logging capabilities. These systems often log minimal information about network traffic, which can be a compliance issue for businesses subject to strict data protection standards. Without comprehensive logging, identifying patterns of suspicious activity becomes more challenging, potentially leaving security vulnerabilities unaddressed.
Inflexibility
Packet filtering firewalls are not known for flexibility. They are designed to monitor specific details such as IP addresses or port numbers, but this is a limited scope in the broader context of modern network access management. Advanced firewalls provide greater visibility and control, adjusting dynamically to evolving security concerns. Packet filters require manual setup and maintenance.
Less Secure
Compared to more advanced firewalls, packet filtering firewalls are less secure. They base their filtering decisions on superficial information like IP addresses and port numbers, without considering the context of user devices or application usage. Their inability to inspect beyond the packet exterior means they can't identify or block payloads containing malicious code, making them susceptible to address spoofing and other sophisticated attacks.
Stateless Operation
The fundamentally stateless nature of packet filtering firewalls limits their ability to protect against complex threats. Since they treat each packet in isolation, they don't remember past actions, which is a shortcoming when it comes to ensuring continuous security. This lack of state awareness can allow threats to slip through if firewall rules are not meticulously crafted and updated.
Difficult to Manage
Packet filtering firewalls may offer ease of use initially but can quickly become difficult to manage as network size and complexity grow. Rule sets must be manually configured and updated, increasing the workload for security teams and the potential for human error. The lack of automation in threat management and packet inspection further complicates the task of maintaining a secure network environment.
Protocol Incompatibility
Another challenge is incompatibility with certain protocols that packet filtering firewalls face. Protocols that require dynamic port allocation or maintenance of state information can present difficulties. This limitation can hinder the use of legitimate services and complicate security policy enforcement.
Types of Packet Filtering Firewalls
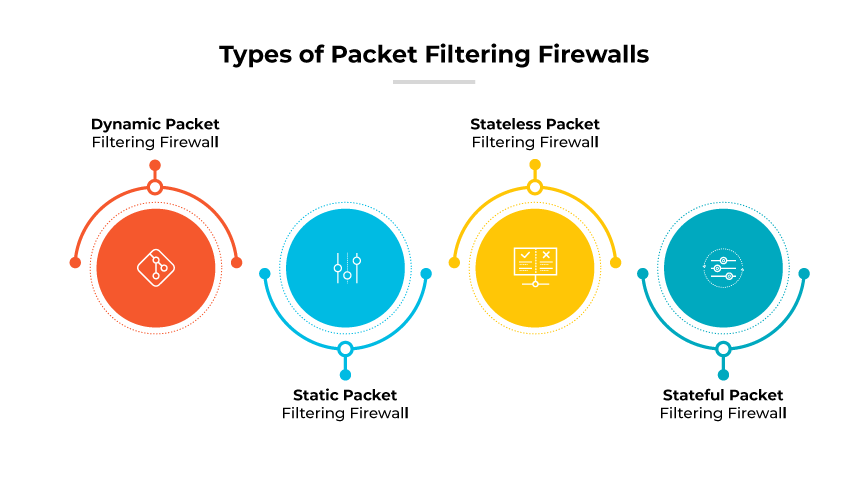
Dynamic Packet Filtering Firewall
Dynamic packet filtering firewalls are adaptive and can modify rules based on network traffic conditions. They allow for a more flexible approach to network security. Dynamic packet filtering firewalls can be useful for handling transfer protocols that allocate ports dynamically. Dynamic packet filtering firewalls are beneficial because they can open and close ports as needed, which enhances security without sacrificing the functionality of applications like FTP.
Static Packet Filtering Firewall
Static packet filtering firewalls are characterized by their fixed configuration. Administrators manually set rules that remain unchanged unless updated by human intervention. This type of firewall is practical for smaller networks with consistent traffic patterns, where the administrative overhead of frequent rule changes is not viable. Static firewalls are straightforward and dependable, providing a basic level of security that can be sufficient for less complex network environments.
Stateless Packet Filtering Firewall
Stateless packet filtering firewalls evaluate each packet in isolation without considering previous or future packets. They rely on predetermined rules to manage network access, offering a fast and lightweight solution. However, the lack of contextual understanding can make stateless firewalls less secure, as they cannot detect patterns in malicious traffic that could indicate a sophisticated attack.
Stateful Packet Filtering Firewall
Stateful packet filtering firewalls maintain a record of active connections and make decisions based on the state of network traffic. This means they can identify and allow packets that are part of an established connection, which increases security by preventing unauthorized access that a stateless system might not detect. Stateful firewalls provide a higher level of security.
Types of Firewalls Defined and Explained
Comparing Packet Filtering Firewalls with Other Security Technologies
Packet Filtering Firewall vs. Proxy Server
Proxy servers function as intermediaries between users and the internet, offering a different layer of security compared to packet filtering firewalls. Unlike packet filters, which operate at the network level, proxies work at the application layer, examining and handling traffic for specific applications. Proxies can anonymize internal network traffic and manage connections in a more granular fashion. They provide a higher level of content filtering and user authentication, which packet filtering firewalls do not inherently support. Combining packet filtering with a proxy can yield a more comprehensive security framework, protecting against a wider array of threats by addressing the limitations of packet filtering firewalls.
Packet Filtering vs. Stateful Inspection Firewall
Stateful inspection firewalls represent an advancement over traditional packet filtering firewalls by maintaining context awareness of network traffic. They monitor the state of active connections and make decisions based on the sequence and state of packets. This enables them to detect and prevent various types of attacks that a simple packet filtering firewall might miss, such as those exploiting established connections. While packet filters quickly allow or deny packets based solely on header information, stateful inspection builds a dynamic control flow for more accurate and secure data packet assessment.
Packet Filtering Firewall vs. Circuit Level Gateway
Circuit level gateways provide security mechanisms at the session layer, making them adept at verifying the legitimacy of sessions without inspecting the contents of each packet. They differ from packet filtering firewalls by ensuring all sessions are legitimate and packets are part of a known connection. This method adds an additional layer of security by tracking the session state of connections, which can prevent certain types of network attacks that do not involve packet spoofing but rather exploit the weaknesses in session management protocols. Circuit level gateways are particularly effective in environments where session integrity is more critical than the granular inspection of packet contents.