What Is a Distributed Firewall?
A distributed firewall is a network security solution that enforces firewall policies across multiple strategic points within a network.
This design allows for comprehensive traffic analysis and security checks, moving away from a centralized gateway to a more flexible, scalable approach that can keep pace with distributed and complex network architectures. It broadens the security perimeter to protect the network's interior by preventing malicious activity from spreading internally.
How Does a Distributed Firewall Work?
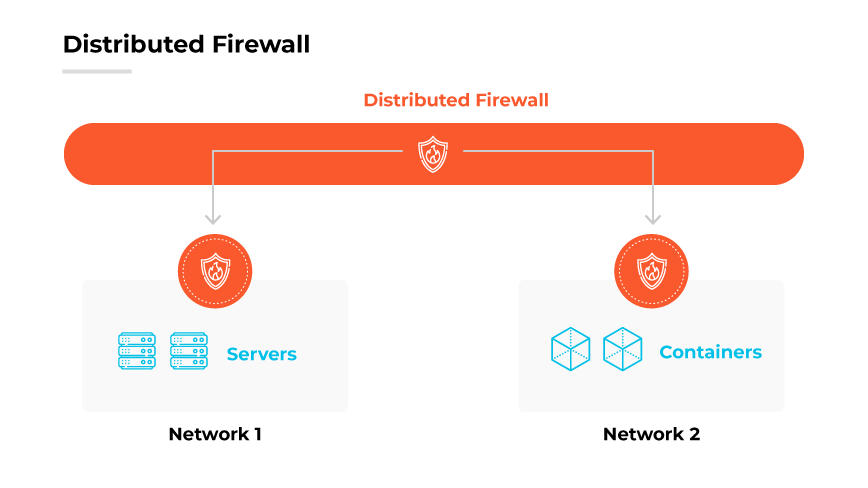
A distributed firewall is a type of internal firewall that works by embedding security services directly into the fabric of a network, particularly within each host or virtual environment.
It enforces security at multiple points, close to the protected assets, instead of channeling all traffic through a central firewall device. This decentralization allows for granular policy enforcement that can reflect the roles and requirements of specific network segments.
The distributed firewall integrates with the network infrastructure, using a central management platform to distribute policies to firewall instances running on individual hosts or virtual machines. These instances work in tandem to inspect and filter traffic entering and leaving each node. The rules can be consistently applied and automatically adjusted based on the dynamic context of the traffic, such as the user identity or the nature of the data.
Policies in a distributed firewall are typically identity based rather than reliant solely on IP addresses, allowing for network security measures that adapt to fluid environments like those found in virtualized data centers. This setup ensures security protocols travel with the data or application, even in complex, changing networks. Protection is always in place, whether a virtual machine moves within the network or scales across multiple environments.
Types of Firewalls Defined and Explained
Distributed Firewall Features
Centralized Management
Distributed firewalls are managed from a central location, simplifying consistent security policy implementation across the entire network. This centralization aids in uniform policy enforcement and streamlines the monitoring process.
Granular Policy Enforcement and Access Control
These firewalls enforce detailed security measures tailored to the specific needs of different parts of the network. This capability allows for precise control and reduces the risk of widespread network vulnerabilities via malicious traffic.
Distributed firewalls allow organizations to implement detailed access management for their assets. Such precision in access control surpasses what conventional firewalls can achieve without adding to the complexity or the demand on processing resources.
Identity-based Control
Rather than solely relying on IP addresses, these firewalls offer identity based firewall control, aligning security policies with user identity, application, and content. This aligns security closely with enterprise governance policies.
Real-time Policy Updates
Security policies can be updated and propagated in real-time, ensuring immediate responsiveness to emerging threats. This ensures that security measures are current and effective.
Independent Host Protection
By applying firewall rules at the host level, distributed firewalls ensure that if one device is compromised, the threat is contained and does not propagate through the network. This local enforcement is critical for limiting the scope of potential breaches.
Distributed Firewall Use Cases
Large Scale Enterprise Security
In vast enterprise networks with diverse infrastructure, distributed firewalls manage security across various segments, ensuring consistent policy enforcement and isolation of potential breaches.
Cloud Environment Protection
Distributed firewalls are well suited for cloud services where resources and data are dispersed across multiple servers, allowing for adaptive, scalable security measures.
Internet Service Provider Networks
ISPs leverage distributed firewalls to secure their networks and offer robust security features to customers, enhancing overall protection for both the provider and the users.
Remote Workforce Connectivity
Businesses with remote or distributed workforces use distributed firewalls to secure remote connections and enforce corporate security policies across all user endpoints.
Virtualized Application Traffic Management and Access Control
A key application for distributed firewalls is managing east-west traffic, facilitating secure communication and data exchange within and across the tiers of a virtualized application. It also provides refined access control for virtual server and desktop environments.
Microsegmentation
This approach facilitates the division of a network into smaller, secure segments. By doing so, it effectively confines threats, restricting their movement across the network.
Distributed Firewall Benefits
Enhanced Security
Distributed firewalls enhance security by providing inspection and control directly at the host level, which can mitigate the risk of internal threats and lateral movement of attackers within the network.
Scalability
They offer a scalable security framework that can grow with the network, enabling protection for an increasing number of hosts without compromising performance.
Reduced Complexity
By decentralizing the security framework, distributed firewalls reduce the complexity associated with managing a centralized firewall, particularly in large and dynamic network environments.
Cost Efficiency
Distributed firewalls can lead to cost savings by using existing infrastructure for security tasks, reducing the need for specialized hardware and associated maintenance.
Why Are Distributed Firewalls Important?
Distributed firewalls are essential in a networked environment where threats can originate from both external and internal sources. They extend protection beyond the traditional network perimeter, embedding security directly within the network infrastructure. This approach offers a more resilient and responsive defense mechanism, critical for complex and dynamic enterprise environments.
As network architectures evolve to include cloud services and remote work scenarios, the perimeter based model of security becomes less effective. Distributed firewalls provide security that is adaptive and follows the flow of data across various environments. They enable continuous monitoring and enforcement of security policies, a necessity for contemporary networks that are frequently changing.
The importance of distributed firewalls also lies in their scalability and ability to enforce detailed policies. They allow organizations to maintain rigorous security standards without compromising on network performance. This ability to protect a growing and diversifying network infrastructure is vital for maintaining the integrity and confidentiality of enterprise data.