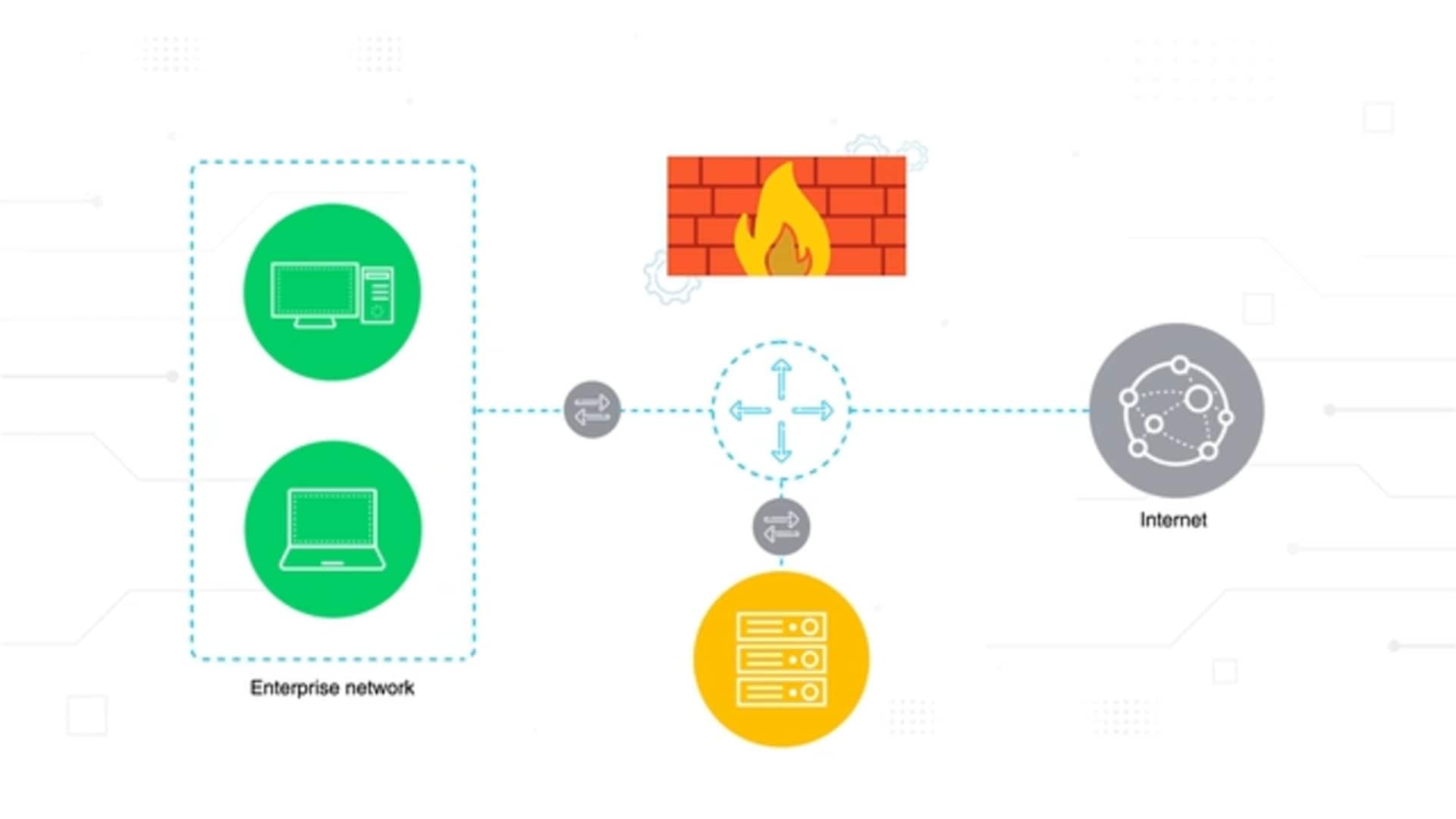
What Is a Host-Based Firewall?
A host-based firewall is software that works on a singular device in a network, providing a protection layer by examining incoming and outgoing traffic.
It effectively filters harmful content, ensuring malware, viruses, and other malicious activities do not infiltrate the system. In environments where network security is paramount, host-based firewalls complement perimeter-based solutions. While perimeter defenses secure the broader network's boundaries, host-based firewalls bolster security at the device level.
How Does a Host-Based Firewall Work?
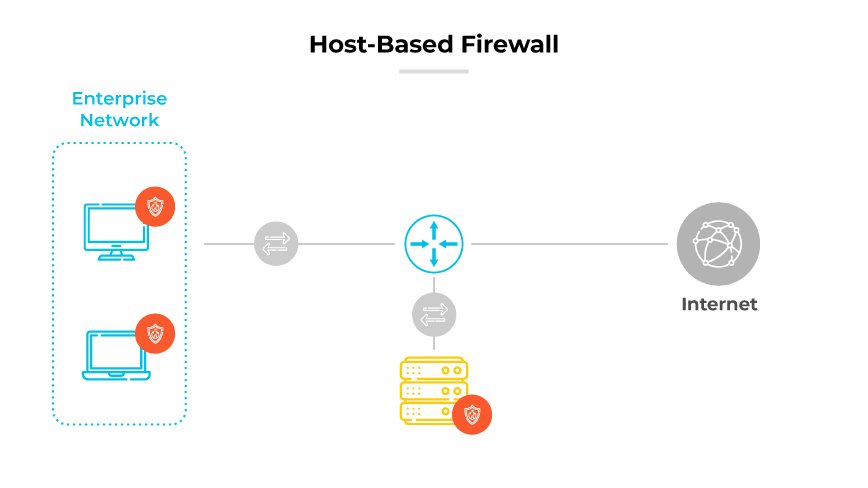
A host-based firewall works as a shield directly on a server or endpoint device. It analyzes and directs network traffic flow. Its primary role is to enforce security policies that determine what kind of data packets can enter or leave the host system.
Upon installation, the firewall establishes a set of rules that identify permissible and impermissible communications based on parameters like IP addresses, port numbers, and protocols. This barrier is critical in preventing unauthorized access and detecting potential threats at the point of entry or exit from a host.
Each time a data packet arrives or departs, the host-based firewall inspects it against its rule set. If a packet matches an approved rule, the firewall permits it to pass through. Conversely, if it matches a disallowed rule, or if there is no matching rule, the firewall blocks the packet.
This selective filtering prevents malicious traffic, such as worms or targeted attacks, from penetrating the host. Host-based firewalls are especially valuable in multinetwork environments, ensuring consistent protection as the device moves across different networks or operates outside the protection of a network firewall.
Host-based firewall management requires regular updates to its rule set to adapt to evolving security threats. Administrators can configure these firewalls to generate security logs, which provide valuable data for monitoring network activity and identifying suspicious patterns.
Types of Firewalls Defined and Explained
Host-Based Firewall Benefits
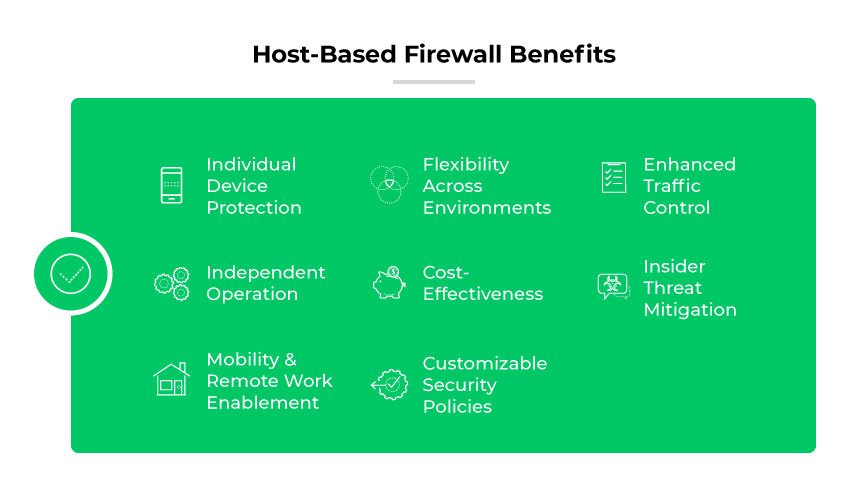
Individual Device Protection
Host-based firewalls provide robust security at the device level, allowing for unique rule sets that cater to the specific needs and roles of each device within an enterprise environment.
Flexibility Across Environments
Since host-based firewalls are installed on individual devices, they maintain consistent protection regardless of network changes, ensuring that a device's security is constant across different environments.
Enhanced Traffic Control
These firewalls offer granular control over incoming and outgoing traffic, enabling precise management of data packets based on predetermined security rules.
Independent Operation
Host-based firewalls operate independently of network-based firewalls, adding an extra layer of defense that remains active even if network perimeter defenses fail.
Cost-Effectiveness
With options ranging from open source to commercial, host-based firewalls can be cost effective, providing protection without a large investment.
Insider Threat Mitigation
They can mitigate risks posed by insider threats by enforcing rules that restrict network activities based on applications, users, or roles within the organization.
Mobility and Remote Work Enablement
As they secure devices independently of the network, host-based firewalls are ideal for protecting laptops and mobile devices that connect to various networks, including public Wi-Fi.
Customizable Security Policies
Administrators can tailor security policies to the precise needs of each host, allowing for flexibility and adaptability in response to changing security requirements or threat landscapes.
Host-Based Firewall Disadvantages

Resource Consumption
Host-based firewalls require computational resources from the devices they are installed on, potentially impacting the performance of the host system.
Complexity in Large Networks
The deployment and management of host-based firewalls can be complex and resource intensive, especially in environments with many endpoints.
Inconsistency in Rules
Ensuring consistency in firewall rules across multiple devices is challenging, leading to potential security gaps and uneven protection levels.
Limited Scope of Protection
Host-based firewalls are less effective in filtering traffic on a network scale and may not be able to handle non-standard protocols or sophisticated threats.
Potential for Misconfiguration
Host-based firewalls are decentralized by nature, so there is an increased risk of misconfiguration. Misconfiguration can lead to security vulnerabilities or unintended network traffic blockages.
Vulnerability to Localized Threats
These firewalls are susceptible to local security breaches, such as those caused by malware or unauthorized user actions on the host device.
How to Set Up a Host-Based Firewall
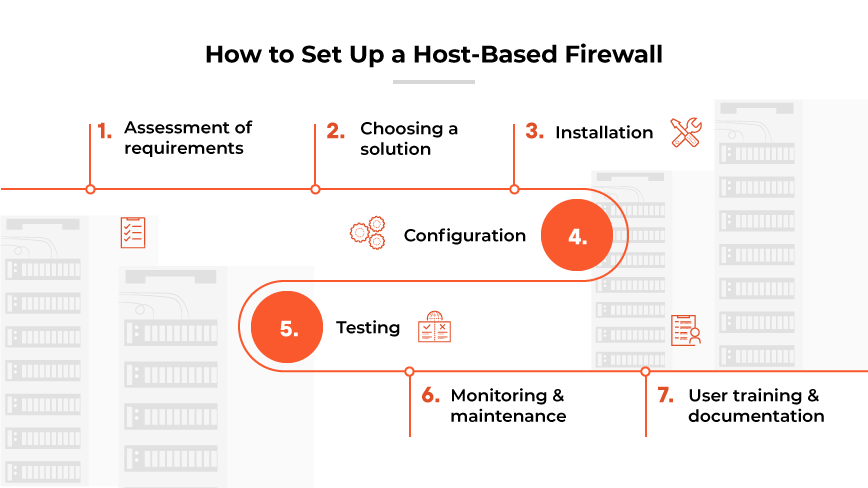
Setup steps and configuration complexity vary based on the host-based firewall solution and vendor. Always refer to vendor documentation for precise instructions tailored to the product. The following instructions offer a broad framework for the setup process but should not replace guidance the firewall solution vendor provides.
1. Assessment of Requirements
- Determine the security needs of each host within the enterprise.
- Identify the types of traffic that need to be allowed or denied.
2. Choosing a Host-Based Firewall Solution
- Select a host-based firewall product that fits the organization's needs.
- Consider factors such as compatibility with the operating system and specific features offered.
3. Installation
- Deploy the firewall software on each host.
- Ensure that the firewall runs with the necessary permissions to control network traffic.
4. Configuration
- Define a set of rules that specify allowed and blocked traffic.
- Configure default deny rules, allowing only necessary communication.
- Set up rules based on the principle of least privilege.
5. Testing
- Test the rules to ensure they work as intended.
- Verify that legitimate traffic is allowed and unauthorized traffic is blocked.
6. Monitoring and Maintenance
- Regularly monitor the firewall logs for unusual activity.
- Keep the firewall software up to date with security patches.
- Periodically review and update the rules as needed.
7. User Training and Documentation
- Educate relevant personnel on the importance of the firewall.
- Document the configuration and rule sets for compliance.
Host-Based Firewalls vs. Network Firewalls
Host-based firewalls operate directly on a single computer or device, monitoring and controlling incoming and outgoing network traffic at that point. They serve as a line of defense, analyzing data packets on a per device basis. This provides a tailored security posture, as rules can are custom for the specific needs of each host. The flexibility of host-based firewalls is beneficial, particularly in environments where devices frequently change networks or operate outside a secure corporate network.
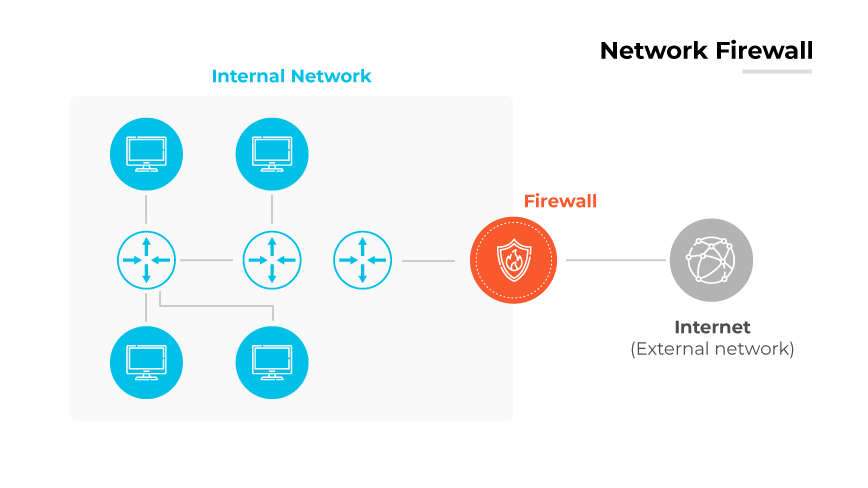
In contrast, network firewalls operate at the gateway between the internal network and the outside world, providing a shield for all devices within the network perimeter. They are capable of handling larger volumes of traffic and offer a centralized security solution. Network firewalls are the first line of defense against external threats and are less susceptible to insider tampering compared to host-based firewalls.
| Host-Based vs. Network-Based vs. Application-Based Firewalls | |||
|---|---|---|---|
| Host-Based Firewall | Network-Based Firewall | Application-Based Firewall | |
| Form factors & placement | Integrated within the host, acts as software protection | Stationed at the network's entry, can be hardware or virtual | Adjacent to applications, offering specific security services |
| Mobility | Follows the device, ensuring protection across networks | Stationary, protecting the network at a fixed point | Flexible, moving with the application's environment |
| Security | Secures endpoints against direct attacks | Defends against external threats at the network boundary | Manages access and use within individual applications |
| Maintenance | Requires individual device configuration | Centralized management through network administration | Needs continuous alignment with application updates |
| Scalability | Constrained by the host's resources | Scalable, particularly with cloud-based solutions | Dependent on the application's architecture |
| Skillsets | Basic technical knowledge is typically sufficient | Advanced networking knowledge is necessary | Requires specialized knowledge of application security protocols |
Host-Based Firewalls vs. Application-Based Firewalls
Host-based firewalls are integral to the security framework of individual devices. They control the incoming and outgoing network traffic based on an established set of security rules on the devices they reside on, such as personal computers or servers. This type of firewall provides a customizable security posture specific to the host it protects, offering a detailed approach to security within a device's operating environment. Their localized nature makes host-based firewalls adept at securing endpoints against threats that may bypass network defenses.
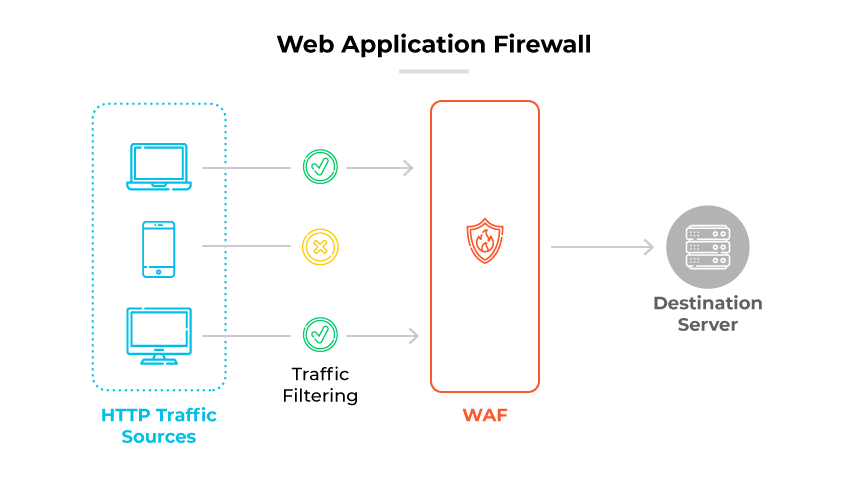
Application-based firewalls, also known as web application firewalls, focus on traffic at the application layer and regulate interactions specific to individual applications. They are adept at understanding and filtering traffic that pertains to web applications, databases, and other services that operate at this layer of the network stack. These firewalls provide granular control over app-to-app communication, user actions within applications, and can enforce policies based on content, user identity, and behaviors within the application. Application-based firewalls add a layer of security that is contextually aware of the application's logic and usage patterns.
The distinction between host-based and application-based firewalls is their scope of protection and the granularity of control. While host-based firewalls provide comprehensive coverage across all network activities of a host, application-based firewalls offer specialized protection that aligns with the specific requirements and operational context of individual applications.